
News
XWorm Malware Evolves into Ransomware Threat
State intelligence agencies maintain RATs functionally identical to XWorm, proving that control depends on who holds the keyboard.

News
State intelligence agencies maintain RATs functionally identical to XWorm, proving that control depends on who holds the keyboard.
News
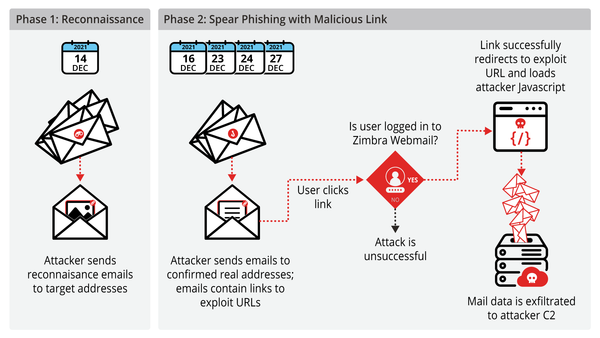
Attackers exploited a zero-day vulnerability in Zimbra Collaboration Suite by hiding malicious code within seemingly harmless calendar invitation (.ICS) files to bypass security defenses and gain access to corporate networks.

Nextcloud
Nextcloud Talk deployment enables enterprise-grade self-hosted video calling through sophisticated WebRTC implementation, TURN/STUN server configuration, and privacy-preserving communication.
![[Video] KDE Linux Ends Three-Decade Distributor Dependence](/content/images/size/w600/2025/09/kde-linux.png)
kde
KDE Linux marks the desktop environment team's first official operating system release, breaking away from three decades of dependence on third-party Linux distributors.

Monero
While the IRS burned $625,000 trying to crack Monero's privacy in 2020, the community is now investing serious money to make sure nobody ever can.
kali
Kali Linux 2025.3 delivers native wireless injection capabilities to Raspberry Pi devices and adds 10 new offensive security tools. The standout feature removes the need for external USB adapters when conducting wireless assessments on ARM hardware.
crypto
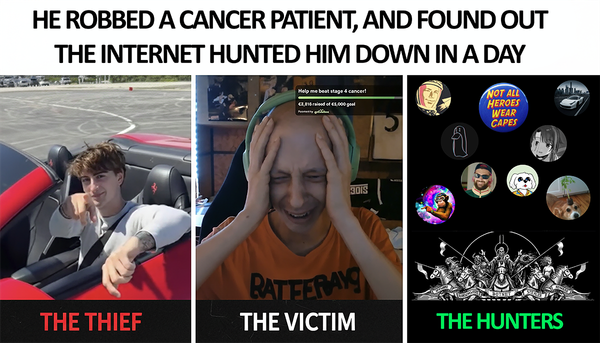
A dying cancer patient lost $32,000 in medical funds when Steam-hosted malware drained his crypto wallet during a live broadcast.
TorVPN
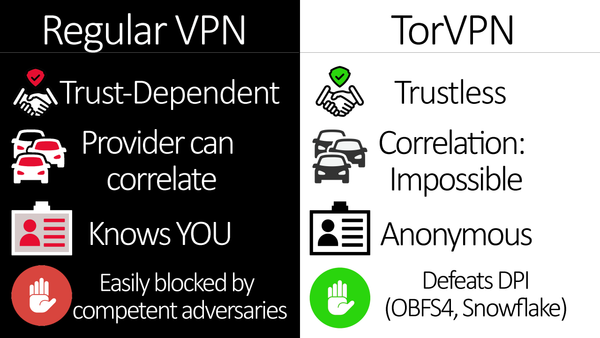
The Tor Project's new Android VPN application fundamentally restructures mobile anonymity through per-app circuit isolation, making commercial VPN trust assumptions obsolete while providing automatic censorship circumvention that adapts faster than authoritarian blocking attempts.
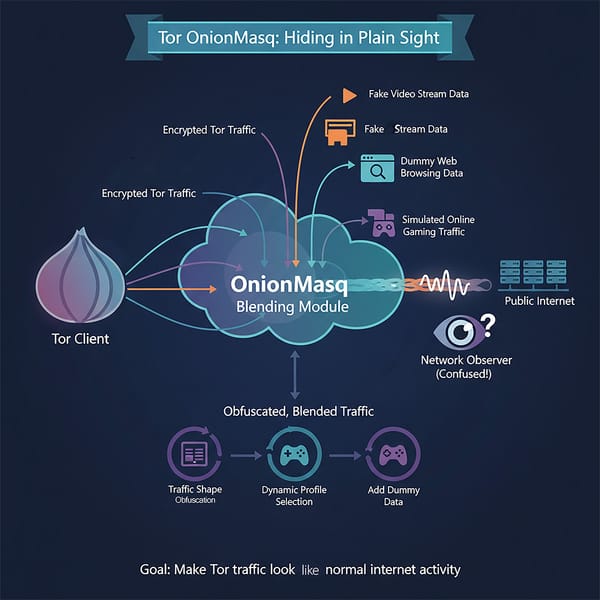
onionmasq
OnionMasq creates VPN-like behavior by trapping applications in kernel-isolated sandboxes where only Tor-routed network interfaces exist, eliminating the bypass vulnerabilities that plague proxy-based solutions.

Monero
While Bitcoin stops at 8 decimal places, Monero goes to 12, a design choice that exposes who's actually thinking about money's future versus who's building digital gold for hodlers.

Surveillance
German and Dutch authorities demonstrated how postal metadata, cryptocurrency analysis, and international surveillance cooperation can penetrate darknet anonymity tools in a multi-million euro drug case.
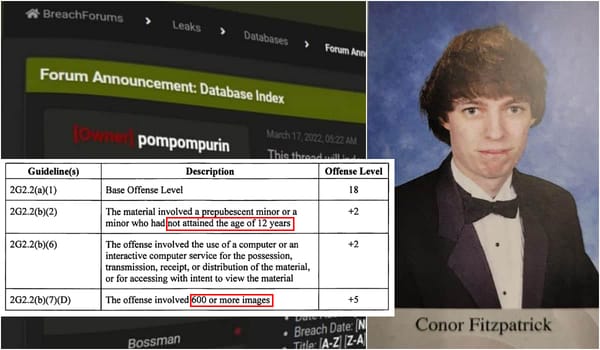
breachforums
Update/correction: On September 16, 2025, the Justice Department announced that Conor Brian Fitzpatrick (aka “Pompompurin”) was resentenced to three years in federal prison.