How Nextcloud End-to-End Encryption Achieves Zero-Knowledge File Storage Through Client-Side Key Management
Nextcloud E2EE implements client-side encryption with hierarchical key management, enabling zero-knowledge cloud storage where server administrators cannot access encrypted file contents even with full system privileges.
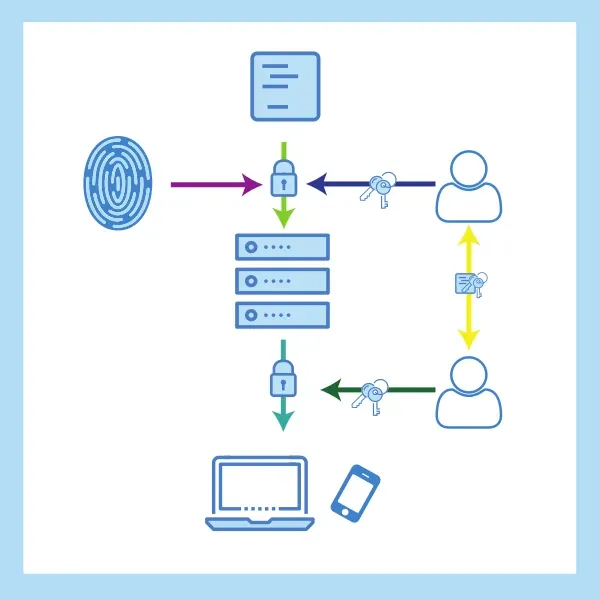
Nextcloud end-to-end encryption transforms your self-hosted file sharing into true zero-knowledge cloud storage. This means that server administrators cannot access your encrypted file contents, even if they have full database and filesystem privileges. Think of it like having a safety deposit box where even the bank employees cannot see what you put inside. Unlike server-side encryption that only protects data when stored on disk, Nextcloud E2EE documentation implements client-side encryption where your cryptographic keys never leave your devices. This protects your file contents against server compromise, legal demands, and insider threats while still allowing you to collaborate with others through carefully designed key sharing mechanisms.
Cryptographic Architecture and Hierarchical Key Management
Nextcloud E2EE uses a smart hierarchical key management system. It starts with your password, which gets strengthened through PBKDF2 key stretching to create your master key. This master key then generates unique encryption keys for each folder using HKDF key derivation functions. Each encrypted folder gets its own AES-256-GCM encryption key that protects both file contents and metadata. When you want to share files with others, RSA-4096 or Ed25519 public key pairs enable secure key sharing between users without requiring shared passwords or pre-established secure channels.
File encryption operates at the client level where libsodium cryptographic library provides authenticated encryption for file contents using AES-256-GCM with random initialization vectors, while file names undergo deterministic encryption to enable server-side duplicate detection and storage optimization. Metadata protection extends to file sizes, modification timestamps, and directory structures through padding schemes and obfuscation techniques that prevent server-side analysis of usage patterns and content characteristics.
File encryption happens on your device before anything gets sent to the server. The libsodium cryptographic library provides the authenticated encryption for your file contents using AES-256-GCM with random initialization vectors. This means each file gets encrypted differently, even if you upload the same file twice. File names also get encrypted, but in a special way that allows the server to detect duplicates and save storage space. The system also protects metadata like file sizes, modification dates, and folder structures through padding schemes and obfuscation techniques. This prevents the server from analyzing your usage patterns or learning anything about your content.
Certificate management handles secure key exchange between users through self-signed certificates. When you first connect with someone, your devices use trust-on-first-use (TOFU) mechanisms. This is like the first time you meet someone and verify their identity. For high-security environments, you can pre-share certificate fingerprints for extra verification. Nextcloud security hardening provides detailed security hardening procedures including certificate pinning, key rotation policies, and audit logging. These help detect potential man-in-the-middle attacks or unauthorized attempts to access your keys.
Recovery key generation creates cryptographically secure backup keys that enable access restoration following password loss, device failure, or account recovery scenarios. These recovery keys use 256-bit entropy generated through cryptographically secure random number generators, then undergo password-based encryption using user-provided recovery phrases before secure storage in encrypted form on Nextcloud servers or offline backup media.
Recovery key generation creates secure backup keys that help you regain access if you lose your password, your device breaks, or you need to recover your account. These recovery keys use 256-bit entropy generated through cryptographically secure random number generators. Think of them as master backup keys. They get protected with password-based encryption using recovery phrases that you provide, then stored securely either on your Nextcloud server in encrypted form or on offline backup media for extra security.
How Your Devices Share Keys Securely
Administrative recovery capabilities provide enterprise-grade key escrow functionality where designated administrators can access recovery keys for compliance, data retention, or employee departure scenarios. This capability requires careful balance between operational requirements and privacy guarantees, with configurable policies determining recovery key access controls, audit trail requirements, and notification procedures for key recovery operations.
Backup encryption ensures that recovery keys and encrypted file backups maintain confidentiality during transport and storage through additional encryption layers using administrator-controlled master keys. Offline recovery procedures enable restoration of encrypted data without network connectivity through portable key material and backup verification mechanisms that prevent data loss during disaster recovery scenarios.
What Nextcloud E2EE Protects You From
❌ Threats Blocked
✅ How It Works
Client Deployment and Configuration Management
Desktop client configuration requires careful attention to key storage security, with encryption keys protected through platform-specific credential management systems including Windows Credential Manager, macOS Keychain, and Linux Secret Service API. Client applications implement secure memory handling with explicit key clearing, anti-debugging protections, and runtime application self-protection (RASP) mechanisms that resist memory dumping and reverse engineering attempts.
Mobile client deployment faces additional challenges including application backgrounding, device lock integration, and biometric authentication that must maintain security while providing usable access to encrypted content. iOS and Android implementations utilize secure enclave hardware, trusted execution environments, and hardware-backed key storage where available to prevent key extraction through device compromise or malware infection.
Folder encryption setup involves migration procedures for existing unencrypted content. Your client applications provide atomic encryption operations that ensure data integrity during the conversion process. This means your files get converted safely without risk of corruption. Performance analysis shows about 10-15% storage overhead for encryption metadata and initialization vectors, plus computational overhead of 5-10% for real-time encryption and decryption operations on modern hardware platforms. For most users, this performance impact is barely noticeable.
Performance Impact of Encryption
Storage Overhead
CPU Performance
Certificate validation mechanisms prevent man-in-the-middle attacks during initial key exchange through certificate fingerprint verification, out-of-band authentication channels, and optional integration with external public key infrastructure. Trust establishment procedures balance security requirements against usability concerns, with configurable policies enabling strict certificate validation for high-security environments or simplified trust-on-first-use for general deployment scenarios.
Security Hardening and Threat Mitigation
Server-side security configuration eliminates potential attack vectors through disabled server-side encryption, restricted administrative access to encrypted folders, and comprehensive audit logging of all cryptographic operations. Nextcloud security hardening provides detailed hardening procedures including filesystem permissions, database security, and network access controls that prevent unauthorized access to encrypted data stores and cryptographic material.
Audit logging captures comprehensive records of encryption operations, key access events, and recovery procedures through structured logging formats compatible with security information and event management (SIEM) systems. Log analysis capabilities enable detection of potential security incidents including unusual access patterns, failed authentication attempts, and suspicious key recovery operations that might indicate compromise or insider threats.
Attack surface reduction involves disabling unnecessary Nextcloud applications, restricting network access to essential services, and implementing defense-in-depth security controls including web application firewalls, intrusion detection systems, and endpoint protection platforms. OWASP security guidelines provides comprehensive security guidelines for web application hardening applicable to Nextcloud deployments in security-sensitive environments.
Integration with external authentication systems enables centralized access control while maintaining end-to-end encryption guarantees through careful separation of authentication credentials and encryption keys. LDAP, Active Directory, and SAML integration preserves zero-knowledge architecture by ensuring that external authentication systems cannot access encryption keys or decrypt file contents even with full authentication database compromise.
Enterprise Deployment and Operational Scalability
Enterprise E2EE Deployment
• Bulk key provisioning
• Policy enforcement
• HIPAA support
• Audit logging
• Key escrow options
• 4-8 hour RTO
Large-scale deployment strategies address user onboarding, policy enforcement, and key management complexity through automated provisioning, centralized configuration management, and scalable key distribution mechanisms. Nextcloud enterprise features documents enterprise features including bulk user import, policy templates, and compliance reporting that enable organizations to deploy E2EE across thousands of users while maintaining security and operational efficiency.
Compliance monitoring ensures adherence to regulatory requirements including GDPR, HIPAA, and industry-specific data protection standards through comprehensive audit trails, data retention policies, and automated compliance reporting. Policy management capabilities enable administrators to enforce encryption requirements, key rotation schedules, and access control policies while maintaining user autonomy over personal encryption keys.
Backup and disaster recovery procedures ensure business continuity while preserving encryption security through geographically distributed backup storage, encrypted backup verification, and automated recovery testing. Recovery time objectives typically range from 4-8 hours for complete service restoration including encrypted data verification, key material recovery, and client reconfiguration across enterprise user populations.
Performance optimization strategies address scalability challenges through client-side caching, efficient key derivation algorithms, and optimized network protocols that minimize encryption overhead during collaborative editing and large file synchronization. Nextcloud source code contains implementation details for cryptographic optimizations, parallel processing techniques, and hardware acceleration that enable E2EE deployment at enterprise scale without significant performance degradation.




