Hackers Exploit Zimbra Zero-Day via iCalendar Files
Attackers exploited a zero-day vulnerability in Zimbra Collaboration Suite by hiding malicious code within seemingly harmless calendar invitation (.ICS) files to bypass security defenses and gain access to corporate networks.
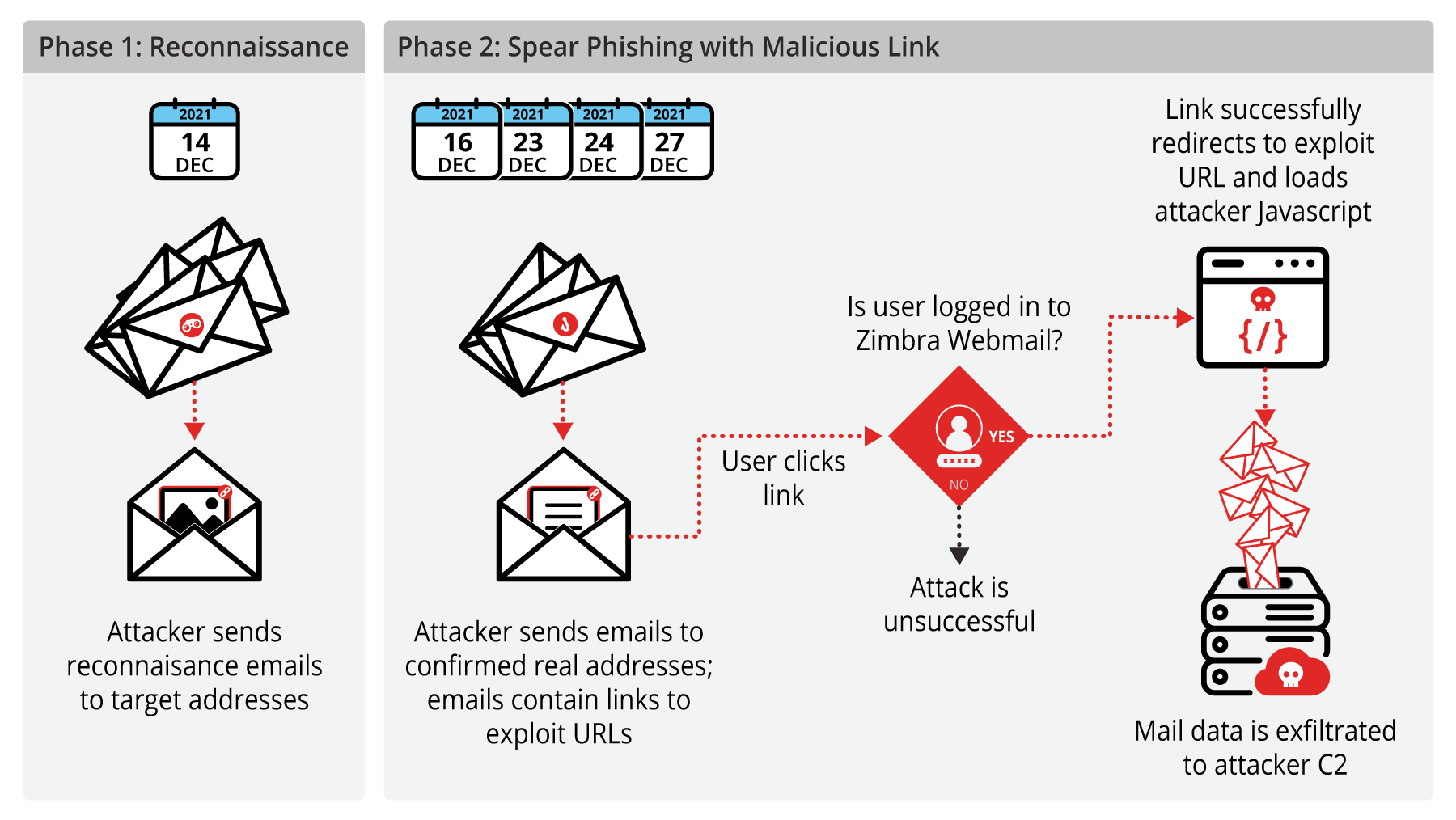
Security researchers who track new types of cyberattacks discovered a serious security weakness in a popular business email and collaboration system called Zimbra Collaboration Suite (ZCS). This weakness, known as a zero-day vulnerability, was actively exploited by attackers in the first part of the year. A zero-day vulnerability means the software's creators, Zimbra, were unaware of the flaw, giving them zero days to create a fix before criminals started using it.
The attackers used a clever trick to hide their malicious software. They sent emails with a special type of file attached known as an .ICS file. To most people, an .ICS file looks like a simple calendar invitation, similar to what you might receive for a meeting or event. Because these files are commonly used in legitimate business communications, email security systems and employees are less suspicious of them. However, in this case, the attackers manipulated the data inside these calendar files to carry out their attack on the Zimbra system.
The core of the problem was a security flaw within Zimbra's code. The system did not properly check or "sanitize" the information contained within these .ICS files. Sanitizing data is a crucial security step where software carefully examines incoming information and removes any potentially harmful instructions before processing it. Because Zimbra skipped this step for certain data in the calendar files, attackers could embed malicious code. When the Zimbra server processed the tampered invitation, it would accidentally execute that code, giving the attacker a foothold inside the organization's network.
This method of attack is particularly effective because it bypasses many common defenses. People are generally trained to be cautious of executable files or documents, but a calendar invite appears harmless. This makes it a powerful tool for what security professionals call "social engineering," which is the practice of manipulating people into performing actions or divulging information. By exploiting a trusted type of file, the attackers increased their chances of success.
For organizations using Zimbra Collaboration Suite, it is critical to ensure that their systems have been updated to the latest version. The Zimbra development team has since released security patches that fix this specific vulnerability. Applying these updates is the most important step in protecting against this particular threat. System administrators should also maintain a general policy of caution, even towards seemingly safe file types, and employ layered security measures to detect unusual activity on their networks.




