GNUnet 0.26.1 Fixes Database Bugs After Breaking Crypto Update
The privacy-focused peer-to-peer network patched database issues less than a month after shipping breaking changes to protect users from cryptographic key misuse.

GNUnet shipped version 0.26.1 in November 2025, patching [database consistency errors](https://git.gnunet.org/gnunet.git/tree/NEWS?h=v0.26.1) that emerged in the same timeframe as the project's cryptographic key handling rewrite. The [bugfix release](https://www.gnunet.org/en/news/2025-11-0.26.1.html) specifically targets PostgreSQL operations, fixing consistency check failures that occurred in certain database queries. This maintenance update follows version 0.26.0's controversial decision to break backward compatibility with older network protocols in the name of hardening security against cryptographic misuse.
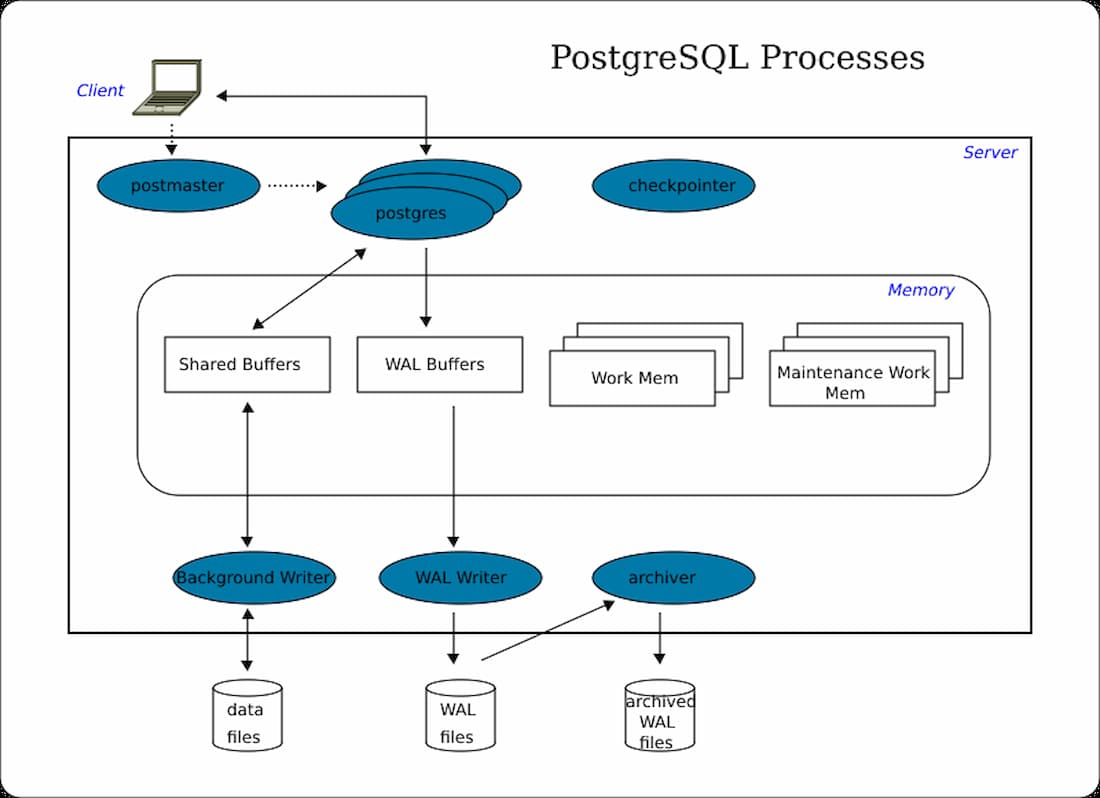
The parent release, 0.26.0, made [breaking changes to libgnunetutil's crypto API](https://www.gnunet.org/en/news/2025-11-0.26.0.html) that prevent developers from mishandling GNUnet's cryptographic key objects in ways that could compromise security. Those changes forced a major version bump because peers running 0.26.X cannot communicate with nodes on the 0.25.X network protocol incompatibility became the price of cryptographic safety. The development team warned that interactions between old and new peers produce undefined behavior and connection failures, making network-wide upgrades mandatory for anyone wanting to participate.
GNUnet functions as a [privacy-focused peer-to-peer framework](https://www.gnunet.org/) built to resist surveillance and censorship through cryptographic anonymity and decentralized architecture. Unlike Tor, which routes traffic through volunteer relays to obscure origin addresses, GNUnet embeds anonymity directly into its protocol by making messages originating from a node indistinguishable from messages merely passing through it at least against adversaries operating within the design's threat model boundaries, though sophisticated long-term traffic correlation remains an open research problem. The network aims for constant bandwidth streams between peers that carry both user requests and background noise like file replication traffic, frustrating attempts at traffic analysis or fingerprinting though achieving this consistently across the network depends on stable peer connectivity and sufficient user participation, challenges compounded by the 190 tracked bugs affecting transport and core communication layers. This architecture trades some performance for resistance against global active attackers who monitor network-wide traffic patterns.
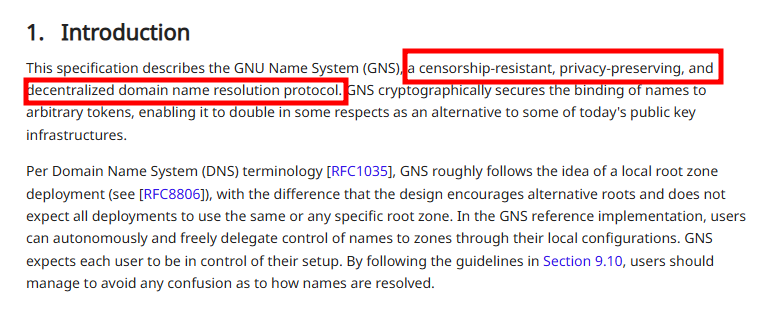
The project maintains several applications on top of its privacy-preserving foundation, including anonymous file sharing, decentralized messaging, VPN capabilities, and the [GNU Name System](https://www.rfc-editor.org/rfc/rfc9498.html) a censorship-resistant DNS alternative standardized as RFC 9498 in November 2023. GNS binds domain names to cryptographic tokens without centralized root servers or trusted certificate authorities, reducing the centralized chokepoints that plague traditional DNS infrastructure. The system takes a different approach to DNSSEC's problems around end-to-end security, query privacy, and centralization by cryptographically securing name resolution through peer verification rather than hierarchical trust.
Version 0.26.1's PostgreSQL fixes arrive while GNUnet remains firmly in alpha development status, carrying [approximately 190 known bugs](https://www.gnunet.org/en/news/2025-11-0.26.0.html) across multiple subsystems. The development team openly acknowledges "major issues" in the TRANSPORT subsystem responsible for peer connections, regressions affecting the CORE communication layer, performance limitations in CADET's mesh networking implementation, and security concerns in the SET subsystem. The project documentation describes the software as "only suitable for early adopters with some reasonable pain tolerance," warning prospective users about usability and privacy issues still under active development.
The [commit history](https://git.gnunet.org/gnunet.git/log/?h=v0.26.1) for 0.26.1 reveals Martin Schanzenbach's broader refactoring work beyond the PostgreSQL fix, including clarifications to HPKE usage and GNS integration within the util/crypto/identity modules. Christian Grothoff added time-related utilities to libgnunetutil, introducing functions like GNUNET_TIME_round_interval2s and JSON parsing helpers for time rounding operations. The team also addressed compiler warnings across namecache, datastore, and messenger modules while fixing key derivation issues in transport layer communicators.
Infrastructure changes show GNUnet completing its migration from Autotools to the Meson build system, with version detection improvements for dependencies like cURL, libsodium, and SQLite. The project fixed parallel test execution failures in core and transport modules, though some problematic tests remain disabled. These technical updates suggest ongoing work to stabilize the codebase even as fundamental architecture decisions like the crypto API refactoring introduce temporary instability.
The crypto API changes forcing version 0.26.0's protocol break reflect tensions inherent in maintaining security-critical software during active development. Hardening cryptographic key handling prevents subtle implementation errors that could expose user traffic or compromise anonymity guarantees, but backward-incompatible changes fragment the network between users who upgrade and those who delay. Projects operating in adversarial threat models face sharper consequences for security mistakes than conventional software, making prevention through API design preferable to hoping developers use dangerous primitives correctly.
GNUnet positions itself [differently from Tor and I2P](https://www.gnunet.org/en/faq.html) by prioritizing distributed many-to-many communication over low-latency one-to-one connections. Where Tor optimizes for real-time web browsing and I2P excels at hidden services, GNUnet trades immediacy for resistance against traffic analysis through its constant-bandwidth cover traffic approach. The protocol delivers strong anonymity for peer-to-peer file sharing and messaging where latency matters less than preventing traffic correlation but this same design philosophy sacrifices the real-time responsiveness required for interactive web browsing. The project's FAQ recommends using Tor for anonymous browsing since GNUnet currently lacks this capability, acknowledging each tool serves distinct use cases within the privacy ecosystem.
The RFC 9498 standardization of GNS in 2023 marked GNUnet's most significant recognition outside activist privacy circles, giving the decentralized naming system formal specification status despite developing outside IETF consensus processes. The RFC publication serves dual purposes documenting GNS for implementers seeking interoperability while establishing the technical foundation for alternative naming systems operating under the .alt top-level domain reserved for non-DNS resolution. This standardization work progressed independently of the core network's alpha stability issues, suggesting GNUnet's component technologies mature at different rates.
Users running GNUnet 0.26.0 who experienced PostgreSQL consistency check failures should upgrade to 0.26.1, though the underlying network compatibility break with 0.25.X remains unchanged. The maintenance release represents iterative stabilization atop architectural changes rather than reversing decisions about cryptographic API design. Early adopters tolerating alpha-quality software gain access to privacy-preserving infrastructure that prioritizes censorship resistance over polish, accepting bugs and breaking changes as costs of participating in adversarial networking research still finding its footing.