Why PGP Key Management Destroys More Operations Than Bad OPSEC
PGP key generation, distribution, and storage failures create retroactive vulnerabilities that compromise entire communication histories.

PGP key management failures expose more sensitive operations than traditional OPSEC mistakes because key compromise, improper key generation, and identity linkage through key usage patterns create retroactive vulnerabilities that compromise historical communications and future operations simultaneously.
Key Generation Weaknesses and Entropy Failures
PGP key security depends entirely on the quality of random number generation during key creation, but most users generate keys on systems with insufficient entropy or compromised random number generators that create predictable keys vulnerable to reconstruction attacks.
Virtual machines, embedded systems, and freshly installed operating systems often lack sufficient entropy during the key generation process, leading to keys that appear random but can be reproduced by attackers who understand the system state at the time of generation.
The Debian OpenSSL vulnerability from 2006-2008 demonstrated how systematic randomness failures can compromise thousands of keys simultaneously when systems use predictable random number seeds, making keys generated during that period vulnerable to brute force attacks that could recover private keys from public keys in hours or days rather than centuries.
Hardware security modules and dedicated entropy sources provide better randomness for key generation, but most users rely on operating system entropy pools that may be depleted or predictable, especially in virtualized environments or systems that generate keys immediately after boot before sufficient entropy has accumulated.
Key generation timing presents another vulnerability since generating keys during predictable system states or immediately after specific events can reduce the effective entropy even when the random number generator appears to be functioning correctly.
Many PGP implementations don't adequately warn users about entropy levels during key generation, leading to keys created with insufficient randomness that compromise all future communications encrypted with those keys. The mathematical structure of RSA and other public key algorithms means that any weakness in the random number generation process affects the security of the entire key pair permanently, making proper key generation critical for long-term security but difficult for users to verify or audit after the fact.
Identity Linkage Through Key Distribution and Usage Patterns
PGP key usage creates persistent identity linkage through key server uploads, signature patterns, and metadata that connects encrypted communications to real-world identities even when the encrypted content remains secure.
Key servers maintain permanent records of key uploads, signatures, and identity assertions that law enforcement can access to build social network maps of encrypted communication participants, revealing organizational structures and relationship patterns that would be invisible in traditional surveillance.
The web of trust model encourages key signing between known contacts, creating a cryptographic record of social relationships that persists indefinitely and can be analyzed to identify key participants in encrypted communication networks. Email headers, key fingerprint sharing, and key verification procedures often leak timing information, IP addresses, and behavioral patterns that allow correlation analysis to link anonymous keys to real identities even when users attempt to maintain operational security.
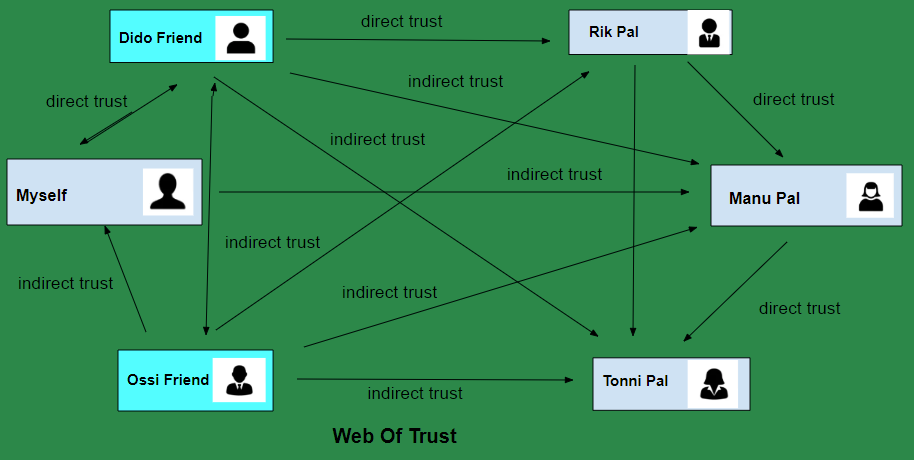
Cross-signing between different key identities creates linkage opportunities where users who maintain separate keys for different purposes accidentally connect them through signature patterns, key server interactions, or technical metadata that reveals common ownership. Long-term key usage develops behavioral signatures through encryption preferences, software versions, and communication patterns that become identifiable even when keys are used across different pseudonymous identities, allowing traffic analysis to correlate activities that users believe are compartmentalized.
Key revocation and update processes create additional linkage opportunities since the procedures for replacing compromised keys often reveal relationships between new and old identities, particularly when users follow similar operational patterns or make identical configuration mistakes across key generations.
Operational Failures and Key Compromise Vectors
PGP operational security failures occur through key storage vulnerabilities, passphrase weaknesses, and backup procedures that expose private keys to compromise while users focus on protecting the encrypted communications themselves rather than the cryptographic infrastructure that makes those communications possible.
Private key storage on internet-connected systems creates persistent attack surfaces where malware, remote access tools, or forensic analysis can recover keys that decrypt years of historical communications retroactively. Weak passphrases protecting private keys often provide insufficient protection against dictionary attacks, particularly when users choose passphrases that relate to their identities or activities, making key recovery feasible for attackers who can perform offline attacks against captured key files.
Backup and synchronization procedures frequently compromise key security when users store encrypted key backups in cloud services, email them to themselves, or maintain copies on multiple devices without proper security measures, creating multiple points of failure that expand the attack surface rather than providing redundancy.
Key export and import procedures during software updates, system migrations, or device replacements often involve temporary storage of unencrypted or weakly encrypted key material that can be recovered through forensic analysis or intercepted during transmission. Shared system usage compromises PGP security when users access their keys from computers used by others, leave key agents running with unlocked keys, or perform cryptographic operations on systems where other users or malware can monitor the process through memory analysis or keylogging.
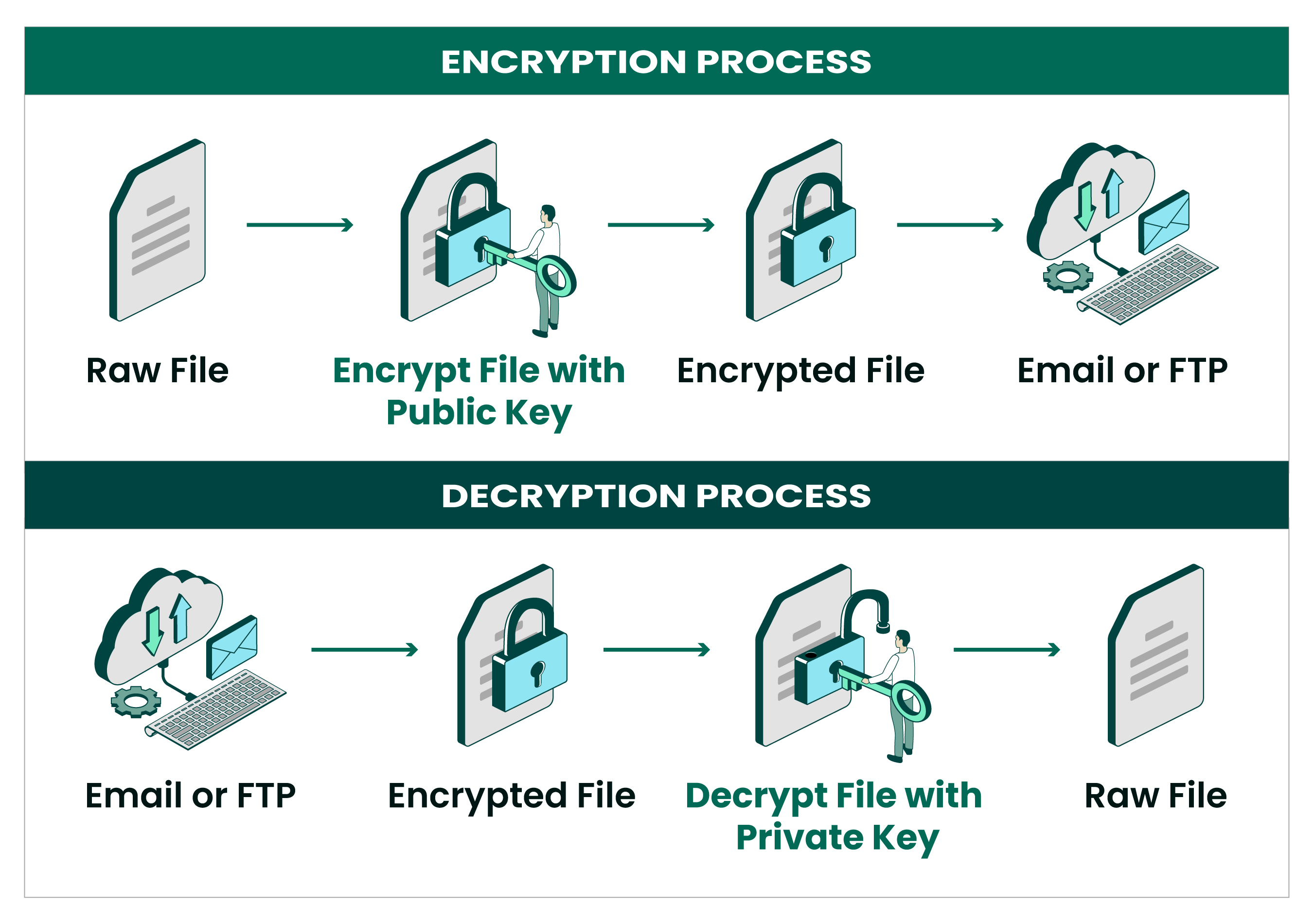
The complexity of proper PGP key management means that users often implement ad-hoc procedures that seem secure but contain fundamental vulnerabilities, such as storing key passphrases in password managers that are more vulnerable than the keys themselves, or using automated key agents that remain unlocked longer than necessary and can be exploited by malware or forensic tools.
These operational failures demonstrate that PGP security depends more on perfect key management discipline than on the strength of the underlying cryptographic algorithms, making it unsuitable for users who cannot maintain consistently high security practices across all aspects of key lifecycle management.




