Why MyMonero Killing Their Wallet Is Good for Monero Privacy
MyMonero's shutdown of there wallet forces thousands of users off a surveillance architecture where keys lived on central servers, an upgrade whether they wanted it or not.
(member quiz at bottom)
MyMonero announced on January 6, 2026 that it will terminate its light wallet service and destroy all server data by February 6, 2026. The company is steering users toward Cake Wallet and positioning this as a graceful handoff to a "trusted successor."
Here's what actually happened: a light wallet service that held user view keys on central servers finally admitted its architecture was incompatible with privacy. This shutdown forces thousands of users into better operational security whether they realize it or not.
View Keys: The Surveillance Primitive
Monero wallets use two cryptographic keys. The spend key allows you to move funds. The view key allows you to see incoming transactions and usually identify outgoing ones through change outputs. View keys cannot steal your money, but they expose your entire financial history to whoever holds them.
MyMonero's architecture required users to upload their private view keys to MyMonero's servers. This created a centralized database of user transaction histories. The server scanned the blockchain on behalf of users to identify their transactions fast and convenient, but fundamentally compromised.
Anyone with physical access to MyMonero's servers could extract those view keys. Anyone with hypervisor control over MyMonero's virtualized infrastructure could do the same. A government subpoena could compel MyMonero to hand over view keys for specific users or entire user cohorts. A data breach would leak view keys permanently. An exit scam or hostile acquisition would weaponize the entire database.
The attack surface extended beyond individual users. Light wallet servers holding large numbers of view keys enable blockchain analysis at scale. Researchers pointed this out years ago in Monero GitHub issue #5145. When a server knows which outputs belong to thousands of users, it can correlate spending patterns, timing analysis, and common input ownership across the network. This degrades Monero's untraceability promise for everyone, not just MyMonero's users.
MyMonero claimed to keep no logs and use strong encryption. These are process claims, not architectural guarantees. Encryption on the server means whoever controls the server controls the keys. "No logs" is a promise, not a proof. The only reliable defense is to never upload the view key in the first place.
Cake Wallet: Better
Cake Wallet improves on MyMonero's model significantly. Your private keys both view and spend never leave your device. The wallet runs client-side. When you create or restore a wallet in Cake, all cryptographic operations happen on your phone or computer. Cake's servers never see your keys.

Cake Wallet is also fully open source, which means the code is auditable. You can verify that keys stay local. MyMonero was partially open source, but its server-side components were proprietary. Cake removed that opacity.
However, Cake Wallet still connects to remote nodes by default (YOU CAN change this to your own). A Monero node is a computer running monerod (the Monero daemon) that maintains a copy of the blockchain. Light wallets like Cake request blockchain data from these nodes over RPC (Remote Procedure Call). Cake has a curated list of high-performance nodes run by trusted community members, and it rotates between them automatically.

Remote nodes cannot see your keys, but they can observe metadata. If you connect over clearnet without Tor, the node operator sees your IP address and correlates it with your wallet's blockchain queries. If your wallet hasn't synced in weeks and suddenly requests a large batch of blocks, the node infers a pattern. If you request blocks starting from a specific restore height, the node learns roughly when your wallet was created. Cake routes transactions over Tor by default, which mitigates some risks, but synchronization traffic still leaks information. (Correction from Tuxsudo: "this part is only true if you are connected to a Tor node.")

This is a massive improvement over holding view keys server-side, but it's not zero-trust. You're trusting the node operator not to log, correlate, or sell your metadata. You're trusting them not to run a malicious node that manipulates transaction data or performs timing analysis. You're outsourcing your blockchain access to a third party.
Self-Hosting: The Only Defensible Posture
Running your own Monero node eliminates third-party trust. You download the entire blockchain to your own hardware. Your wallet queries your own node. No remote server sees your IP address, your sync patterns, or your transaction timing.
A full Monero node requires around 200GB of storage as of late 2025 (the blockchain grows continuously). You can run a pruned node, which retains only recent blockchain data and uses roughly 60-80GB, or a full archival node. Either option gives you sovereignty over your blockchain access.
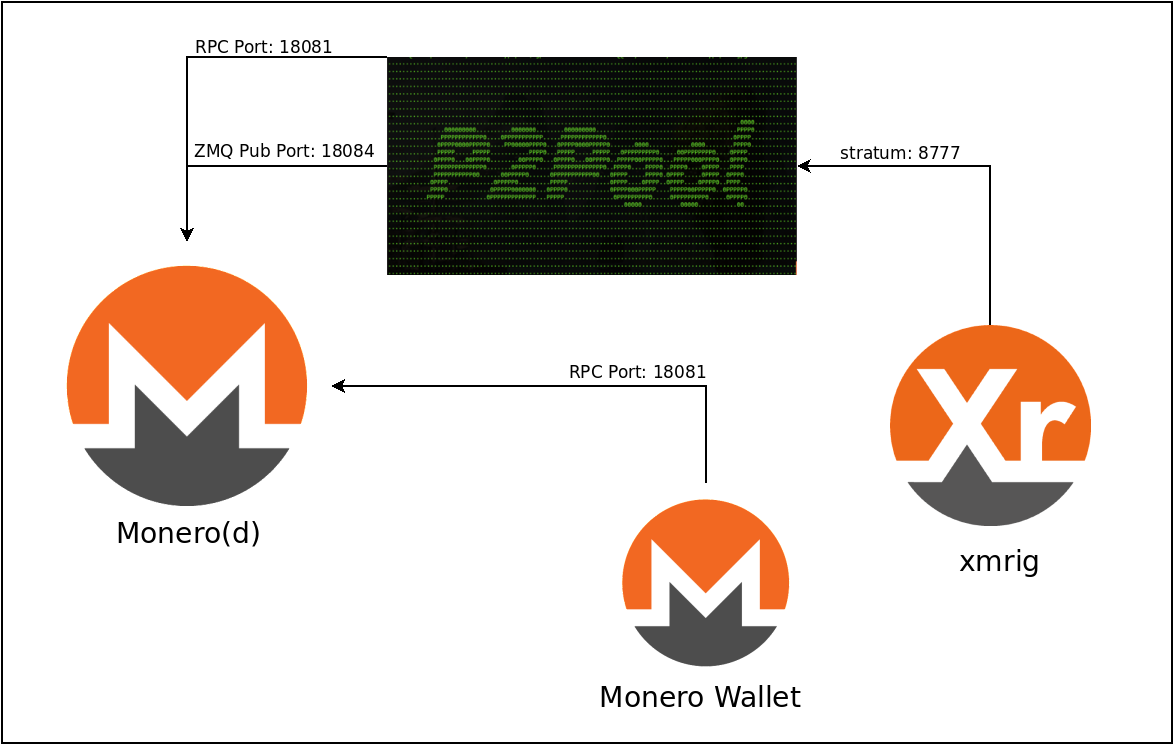
Feather Wallet is a lightweight desktop wallet that supports connecting to your own node. Feather is open source, supports Tor by default, and can connect to either remote nodes or your local monerod instance. When configured to use your own node, Feather provides maximum privacy: client-side key management plus self-hosted blockchain access.

The official Monero GUI and CLI wallets also support running your own node. The GUI can launch monerod automatically in the background, or you can run monerod separately as a system service. Running your own node adds operational complexity you need to maintain the software, monitor disk usage, and ensure the node stays synchronized but it removes the entire category of remote node surveillance.
Guides for setting up a Monero node are available at CoinCashew and Monero Guides. The process involves downloading monerod, configuring ports, and optionally setting up Tor or I2P for additional privacy. Once running, you can connect any Monero wallet to your node via local RPC at 127.0.0.1:18081 (the default port).
If you can't self-host due to hardware limitations, the next best option is connecting to a node you control remotely for example, a VPS you rent and configure yourself, or a Raspberry Pi at home exposed through Tor. This maintains custody of your node's logs and query patterns.
Migration Mechanics and Risk Management
MyMonero users have until January 6, 2026 to migrate. The company offers three paths:
- Restore your existing wallet in Cake. Export your 25-word legacy seed from MyMonero, import it into Cake. The wallet syncs by scanning the blockchain from your restore height forward. This preserves your existing address and transaction history.
- Create a new Polyseed wallet in Cake and transfer funds. Polyseed is a newer 16-word mnemonic format that Monero supports. This generates a fresh wallet with no link to your old address. Sending funds from MyMonero to a new Cake wallet breaks address linkage but costs a transaction fee.
- Create a BIP39 multi-currency wallet in Cake. BIP39 is a standard 12-word mnemonic used by Bitcoin and most other cryptocurrencies. Cake supports using BIP39 for Monero alongside other coins. This allows one seed phrase for multiple currencies but is less common in Monero-specific contexts.
All three options work. Option 1 is fastest. Option 2 offers a clean break from your old address. Option 3 consolidates multiple currencies under one seed.
If you used MyMonero and took no action by January 6, your seed phrase still works. Monero seeds are blockchain-agnostic. You can restore your wallet in any Monero client months or years later. MyMonero's shutdown only terminates their server infrastructure. Your funds remain on the blockchain, accessible via your seed.
MyMonero claims it will permanently destroy all server data view keys, transaction caches, logs within 30 days of shutdown. They state their data center partner will decommission the servers in a way that prevents recovery. This is process again, not proof. Treat MyMonero's view key database as compromised until proven destroyed, which is impossible to verify externally.
If you want to nuke the address linkage entirely, generate a new wallet after migrating from MyMonero and send your funds to the new address. This breaks the connection between any historical surveillance of your old view key and your future activity. It costs a transaction fee but restores full privacy going forward.
Operational Takeaways
Light wallets that require view key disclosure are architecturally hostile to privacy. MyMonero's shutdown acknowledges this. The forced migration is a net positive for users, even if inconvenient.
Cake Wallet is a significant upgrade: client-side keys, open source code, Tor support. It's a good intermediary option for users who can't or won't run their own node. But reliance on remote nodes still leaks metadata.
Self-hosting a Monero node is the only fully defensible posture. Feather Wallet connected to your own monerod instance, or the official Monero GUI/CLI with a self-hosted node, eliminates third-party dependencies. The operational cost is higher storage, bandwidth, maintenance but the attack surface shrinks to your own hardware and network configuration.
If you're serious about operational security, treat light wallets as a temporary convenience and plan your migration to self-hosted infrastructure. The more users run their own nodes, the more resilient and decentralized the Monero network becomes. MyMonero's shutdown is one more step in that direction.