Why LibreWolf Destroys Chrome and Firefox for Operational Security
LibreWolf strips Firefox of corporate surveillance while implementing aggressive fingerprinting resistance and privacy hardening.

LibreWolf represents the antithesis of surveillance capitalism disguised as web browsing, stripping Mozilla's Firefox of its corporate tracking apparatus while hardening privacy protections that mainstream browsers deliberately weaken. This open-source browser fork demonstrates how community-driven development creates superior operational security compared to corporate products designed to harvest user data for profit.
Corporate Browser Surveillance Architecture and LibreWolf's Response
Chrome and Firefox implement comprehensive data collection systems that monitor browsing behavior, search queries, and user preferences while claiming to protect privacy through marketing theater.
Google Chrome operates as a surveillance platform first and browser second, transmitting detailed usage analytics, syncing browsing history to Google servers, and integrating with Google's advertising ecosystem to create comprehensive user profiles for targeted marketing and government cooperation. Mozilla Firefox, despite positioning itself as a privacy alternative, maintains telemetry collection, sponsored content injection, and partnerships with data brokers that compromise user privacy through default settings most users never modify.
Firefox's Studies system allows Mozilla to remotely execute code on user systems for research purposes, creating potential security vulnerabilities and privacy invasions that corporate oversight cannot adequately control.
Both browsers implement safe browsing features that send URL hashes to corporate servers, creating opportunities for traffic analysis and user tracking through seemingly beneficial security measures. LibreWolf eliminates this surveillance infrastructure entirely, removing Mozilla's telemetry collection, sponsored shortcuts, Pocket integration, and Studies functionality while implementing privacy-first defaults that assume users want protection rather than convenience.

The browser strips out Firefox's data collection mechanisms at the source code level through systematic source code modifications, ensuring that privacy cannot be compromised through configuration errors or software updates that reset user preferences to corporate-friendly defaults.
LibreWolf's development process involves auditing Firefox's codebase for privacy violations and systematically removing or disabling features that could compromise user anonymity, creating a browser that prioritizes operational security over corporate data collection requirements.
Technical Hardening and Fingerprinting Resistance Implementation
LibreWolf implements aggressive fingerprinting resistance through technical modifications that prevent websites from creating unique browser signatures used for tracking across different domains and browsing sessions.
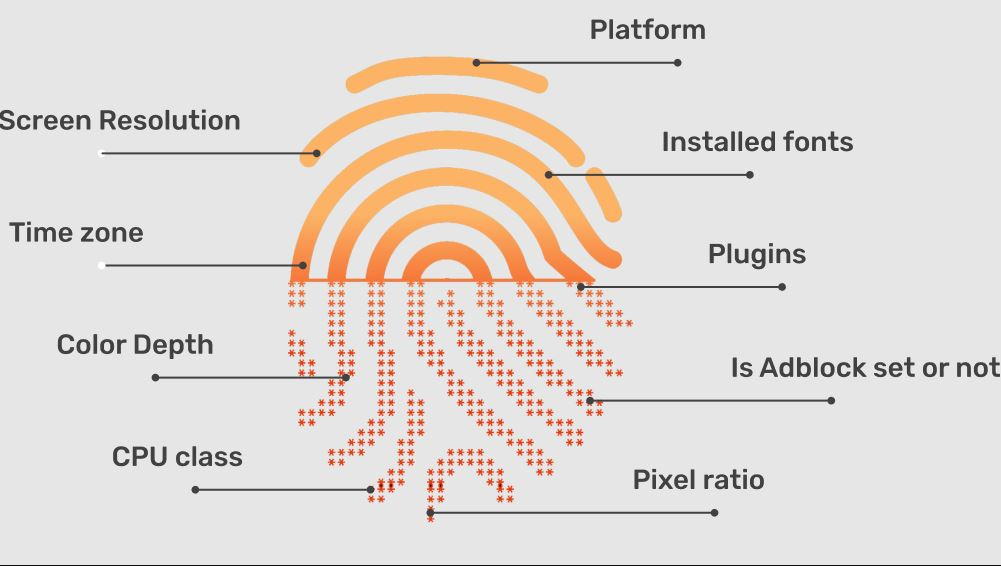
The browser spoofs user agent strings, standardizes screen resolution reporting, and randomizes canvas fingerprinting outputs to prevent websites from identifying individual users through hardware and software configuration details. WebRTC functionality gets disabled by default in LibreWolf, preventing websites from discovering real IP addresses behind VPN connections or proxy services through JavaScript-based network enumeration attacks that bypass traditional privacy protections.
The browser modifies JavaScript timing APIs to prevent high-resolution timing attacks that can fingerprint users through hardware performance characteristics, network latency measurements, and CPU execution timing that creates unique identifying signatures. LibreWolf disables WebGL by default, eliminating GPU fingerprinting vectors that websites use to identify users through graphics hardware specifications, driver versions, and rendering capabilities that remain consistent across browsing sessions and privacy tools.

The browser implements strict referrer policies that prevent websites from tracking user navigation patterns through HTTP referrer headers that reveal previous page visits and cross-site browsing behavior.
Font enumeration protections prevent websites from identifying users through installed font lists, while audio context fingerprinting gets blocked to stop websites from creating unique audio signatures through browser audio processing capabilities. LibreWolf's fingerprinting resistance operates at multiple levels, modifying both browser behavior and website interaction patterns to create a more uniform fingerprint that resists statistical analysis techniques used by tracking companies.
The browser's privacy protections extend to DNS over HTTPS configuration, secure connection preferences, and cookie handling policies that minimize data leakage through network-level monitoring and cross-site tracking mechanisms that corporate browsers enable by default.
Open Source Development Model and Security Transparency
LibreWolf's open source development model provides security advantages that proprietary browsers cannot match through community-driven code auditing, transparent development processes, and accountability mechanisms that prevent hidden surveillance features or backdoor implementations.
The browser's source code remains publicly available for security researchers to examine, identify vulnerabilities, and verify that privacy claims match actual implementation details rather than relying on corporate promises about data handling practices. Community development means that privacy-hostile features cannot be secretly introduced through opaque corporate decision-making processes, while security improvements get implemented based on user needs rather than business model requirements that prioritize data collection over user protection.
LibreWolf's development team maintains independence from corporate influence, advertising revenue, and government pressure that compromises mainstream browser development through conflicts of interest between user privacy and business profitability. The open source model enables rapid security response when vulnerabilities are discovered, with community contributors able to develop and deploy fixes without waiting for corporate approval processes that may prioritize business considerations over user security.
Fork-based development allows LibreWolf to inherit Firefox's security updates while rejecting privacy-hostile features, creating a browser that maintains compatibility with web standards while eliminating surveillance capabilities that Mozilla includes for revenue generation.
The browser's development process involves systematic removal of corporate tracking infrastructure, replacement of privacy-hostile defaults with security-focused configurations, and ongoing auditing of upstream Firefox changes for potential privacy violations. LibreWolf demonstrates how open source development can create superior privacy tools compared to corporate alternatives by eliminating conflicts of interest between user protection and business model requirements that inevitably compromise mainstream browser security.
Community-driven development ensures that browser features serve user interests rather than corporate surveillance objectives, while transparent development processes enable users to verify that privacy claims match actual implementation rather than trusting corporate marketing statements.




