[URGENT] DEF CON Researcher Exposes How Password Managers Betray Your Trust
Czech security researcher Marek Tóth demonstrated at DEF CON 33 how a single click on any malicious website can steal passwords, credit cards, and 2FA codes from 40 million users of major password managers, with vendors like 1Password and LastPass refusing to fix the vulnerabilities.
![[URGENT] DEF CON Researcher Exposes How Password Managers Betray Your Trust](/content/images/size/w1200/2025/08/password-manager-issue.jpg)
Original article credit: The Hacker News reported on Marek Tóth's DEF CON 33 research into DOM-based extension clickjacking affecting 11 password managers, but the coverage lacks critical technical depth and vendor accountability context.
Attack Architecture and Technical Reality
Tóth's technique manipulates UI elements that browser extensions inject into the DOM by making them invisible using JavaScript, specifically using opacity:0 to various elements or overlay UI components. Unlike traditional iframe-based clickjacking that web applications can mitigate with X-Frame-Options or CSP headers, DOM-based attacks require more comprehensive defensive measures at the extension level.
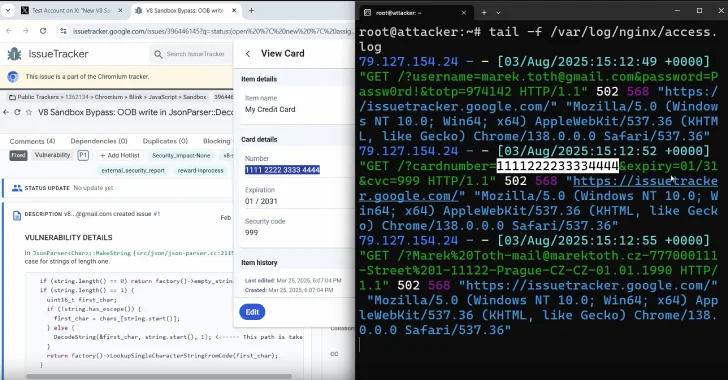
The attack exploits fundamental browser extension architecture. Password manager extensions inject interactive elements into web pages through content scripts. A malicious script can manipulate these injected elements by applying CSS properties like opacity: 0, making autofill prompts invisible while remaining clickable. Attackers overlay invisible HTML elements over the password manager interface while users believe they are interacting with harmless clickable elements.
Tóth documented multiple attack methods: extension element manipulation applying opacity: 0 directly, parent element manipulation making elements transparent while rendering fake interfaces, and overlay attacks inserting layers with pointer-events: none so clicks pass through to autofill components underneath.
The subdomain attack vector presents the most serious threat. All password managers autofill credentials not only to the main domain but also to all subdomains, meaning attackers can exploit XSS vulnerabilities or subdomain takeovers to steal stored credentials with a single click. An attacker finding XSS on any subdomain can potentially steal a user's primary account credentials through clickjacking techniques.
Vendor Responses Expose Industry Negligence
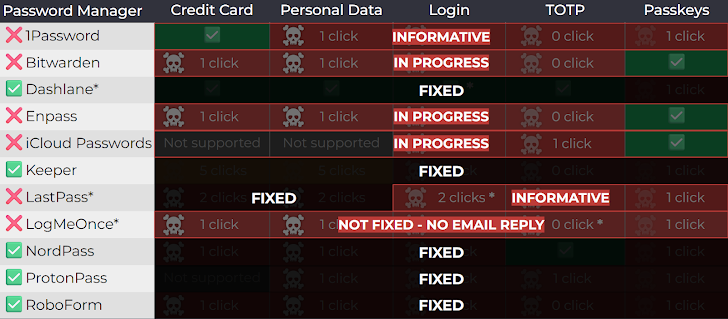
The vendor response pattern reveals systematic security negligence across the password manager industry. 1Password and LastPass flagged these vulnerabilities as "informative," practically speaking making these vulnerabilities unlikely to be patched without pressure from customers. 1Password and LastPass have argued that defending against clickjacking is outside their control, placing responsibility on users to avoid malicious websites.
This position is dishonest. 1Password's HackerOne team stated "Clickjacking the autofill action for the personal identification item has also already been reported in previous programs, and will not be reconsidered at this time," indicating researchers had reported this bug so many times that 1Password added it as explicitly out-of-scope for their bounty program.
As of August 19, 2025, six password managers remain vulnerable: Bitwarden, 1Password, iCloud Passwords, Enpass, LastPass, and LogMeOnce, representing approximately 32.7 million active installations still at risk. LogMeOnce never responded to any communication attempts by either Tóth or Socket Security.
Bitwarden sent a statement claiming fixes in version 2025.8.0 rolling out this week, but Tóth's latest status shows Bitwarden version 2025.7.0 remains vulnerable to Parent Element attacks.
Browser Extension Security Architecture Failures
The research exposes fundamental weaknesses in how browser extensions interact with web page DOM structures. Shadow DOM provides style and JavaScript encapsulation preventing styles and scripts from the parent document interfering with extensions, but most password managers fail to implement proper Shadow DOM isolation.
When exposing HTML or script files that enable extension interaction, developers should restrict access using the matches parameter to limit loading to specific trusted domains and implement X-Frame-Options: DENY headers or Content-Security-Policy: frame-ancestors 'none'. The affected password managers failed these basic defensive measures.
Some managers' UI elements remain manipulable via Shadow DOM or fail to detect high-risk overlay conditions. This indicates either incompetent implementation or willful negligence in security design.
Passkey Authentication Compromised
Tóth demonstrated successful attacks against sites using popular passkey solutions such as Hanko, NokNok, and Authsignal, all of which failed to implement session-bound challenges, an essential security measure to prevent replay attacks. In some scenarios, passkey authentication could also be exploited in 8 out of 11 tested password managers.
This destroys the security narrative around passkeys as a phishing-resistant authentication method. Passkey implementations without proper session binding are vulnerable to replay through DOM manipulation.
OPSEC and Privacy Implications
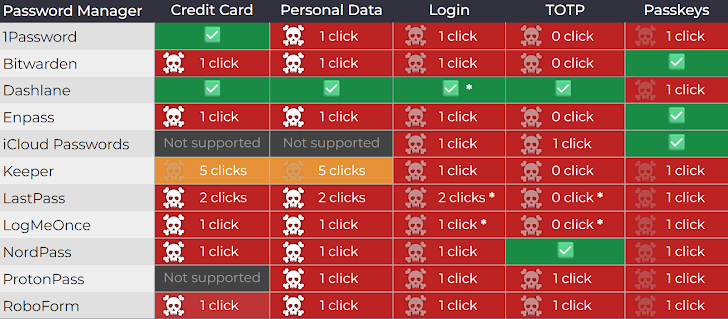
The attack surface extends beyond direct credential theft. Six out of nine tested password managers were vulnerable to credit card detail extraction, while eight out of ten could be exploited to exfiltrate stored personal information. This includes names, addresses, phone numbers, and security codes.
Ten out of eleven password managers were susceptible to credential theft, including Time-based One-Time Password (TOTP) codes used for two-factor authentication. TOTP compromise breaks the security model of hardware tokens and authenticator apps.
For operational security, the subdomain attack vector means any website you trust becomes a potential attack surface. Password managers typically autofill credentials not only on the exact domain where they were saved but also on all subdomains, significantly expanding the attack surface.
Mitigation Strategies
For Chromium-based browser users, configure site access to "on click" in extension settings rather than automatic access, giving users manual control over autofill functionality. This prevents automatic DOM injection that attackers can manipulate.
Until fixes are available,
disable the auto-fill function in password managers and
only use copy/paste.
Set only exact URL match for autofill credentials, though this can still be exploitable for credit card/personal data and attackers can still find vulnerabilities on exactly the same domain.
Or, even better: stop using browser extension password managers entirely. Switch to standalone password manager applications that don't inject DOM elements into web pages. This eliminates the attack surface completely.
This research validates the fundamental OPSEC principle: never trust browser extensions with sensitive data. The convenience of browser-based password managers comes at the cost of expanded attack surfaces that vendors refuse to properly secure.




