The Technical Reality of VPN Kill Switches and DNS Leaks
VPN kill switches fail during timing windows while DNS leaks occur through multiple system-level bypass mechanisms.

VPN kill switches and DNS leak protection fail to provide reliable security due to implementation weaknesses, timing vulnerabilities, and fundamental architectural limitations that create exposure windows during normal operation.
Kill Switch Implementation Failures and Timing Attacks
VPN kill switches work by monitoring the VPN connection status and blocking internet traffic when the VPN disconnects, but implementation flaws create windows of vulnerability during connection establishment, reconnection attempts, and software updates that expose user traffic to surveillance.
Most kill switch implementations use firewall rules or routing table modifications that take time to activate after a VPN disconnection is detected, creating brief periods where traffic flows through the regular internet connection before the kill switch blocks it. These timing windows can last several seconds during which applications continue sending unprotected traffic, including DNS queries, web requests, and background application data that reveals user identity and activity to network observers.
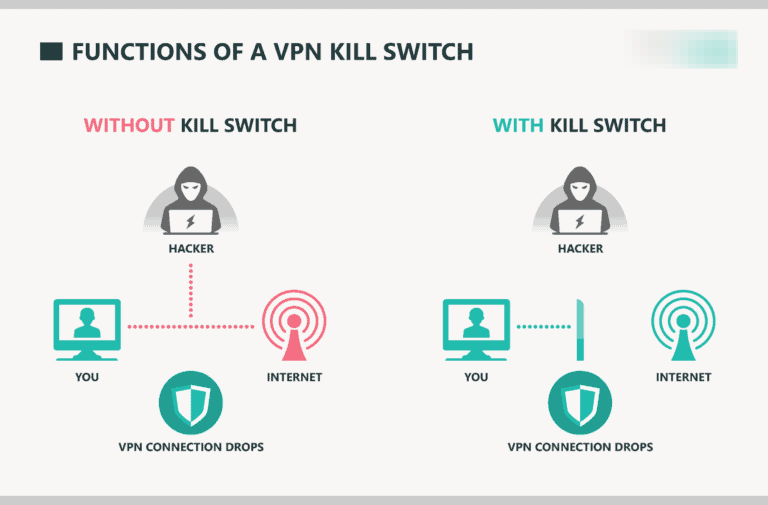
Windows-based VPN clients face particular challenges because the Windows firewall system allows certain types of traffic to bypass firewall rules during the brief period when rules are being updated, creating opportunities for data leakage that sophisticated network monitoring can detect and exploit. The kill switch detection mechanism itself creates vulnerabilities since it relies on monitoring VPN connection status through methods that can be spoofed or manipulated by malware, network attacks, or even legitimate software updates that temporarily disable VPN functionality without triggering proper kill switch activation.
Many VPN applications implement kill switches through application-level controls rather than system-level network filtering, meaning that if the VPN application crashes, becomes unresponsive, or gets terminated by system management tools, the kill switch protection disappears entirely while other applications continue normal internet connectivity. Split tunneling features, which allow certain applications to bypass the VPN connection, create additional complexity for kill switch implementations since the system must distinguish between authorized bypass traffic and unauthorized leakage, often leading to configuration errors that compromise the intended protection.
DNS Leak Vectors and Resolution Bypasses
DNS leaks occur when domain name resolution requests bypass VPN encryption and travel directly to ISP or public DNS servers, revealing browsing destinations even when web traffic remains encrypted through the VPN connection. Operating systems implement multiple DNS resolution mechanisms including system-level resolvers, application-specific DNS handling, and cached DNS responses that can all create leakage paths independent of VPN configuration settings.
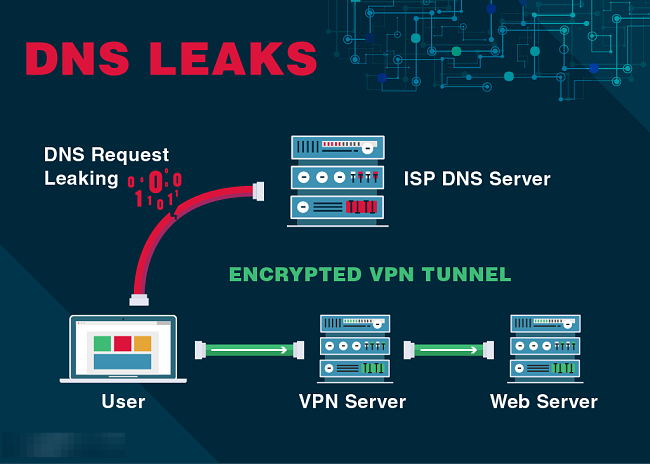
Windows systems are particularly vulnerable to DNS leaks through the Smart Multi-Homed Name Resolution feature that sends DNS queries to all available network interfaces simultaneously, choosing the fastest response regardless of whether it comes from the VPN's DNS servers or the local ISP's servers.
Browser-based DNS-over-HTTPS implementations create another leakage vector since browsers may perform DNS resolution independently of system settings, connecting directly to services like Cloudflare or Google's DNS servers even when the VPN is configured to use different DNS servers for privacy protection.
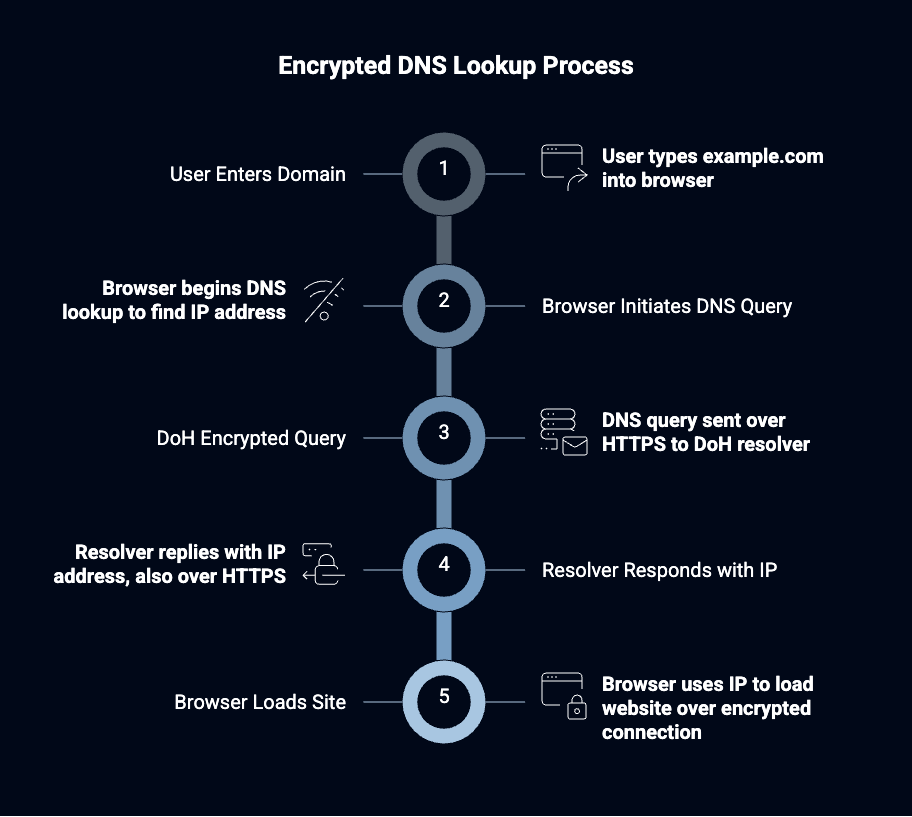
IPv6 DNS resolution often bypasses VPN DNS settings entirely since many VPN providers only configure IPv4 DNS redirection while leaving IPv6 DNS requests to be handled by the system's default resolvers, which typically point to ISP-provided servers that log all queries. Application-specific DNS behavior creates additional leakage opportunities since many applications implement their own DNS resolution logic that ignores system-wide VPN DNS settings, connecting directly to hardcoded DNS servers or using DNS resolution libraries that don't respect VPN routing configuration.
DNS caching mechanisms at both the system and application level can cause previously resolved domain names to be served from cache even after VPN connection, but new DNS queries for uncached domains may leak through the regular internet connection if the VPN's DNS configuration isn't properly applied across all system components.
Network Stack Bypasses and Application-Level Leaks
VPN protection operates at the network layer but faces bypass attempts from applications that implement their own networking stacks, use alternative protocols, or exploit system-level networking features that circumvent VPN routing rules.
WebRTC implementations in web browsers can establish direct peer-to-peer connections that bypass VPN routing entirely, revealing users' real IP addresses to websites through JavaScript APIs that enumerate local network interfaces and attempt direct connections to remote servers.
Background system services including automatic updates, telemetry reporting, and network time synchronization often use privileged network access that bypasses user-level VPN configurations, sending identifying information through the regular internet connection even when user applications appear to be protected by VPN encryption.
Mobile applications frequently implement network libraries that don't respect system-wide VPN settings, particularly applications that use native networking code or third-party SDKs that establish their own connections independent of the operating system's network routing configuration.
Captive portal detection mechanisms built into modern operating systems actively attempt to bypass VPN connections during the initial connection process to determine whether internet access is available, sending identifying information to detection servers that can log user locations and device characteristics. Network interface binding problems cause applications to continue using the original network interface even after VPN connection establishment, particularly on systems with multiple network adapters where applications may bind to specific interfaces rather than using the system's default routing table.
Protocol-specific bypasses affect traffic that doesn't route properly through VPN tunnels, including certain types of ICMP traffic, multicast packets, and broadcast traffic that may leak device information or network topology details that help identify users despite VPN usage.
The fundamental limitation is that VPN clients must trust the host operating system to route all traffic through the VPN tunnel, but operating systems prioritize network connectivity and performance over privacy, creating multiple mechanisms through which traffic can bypass VPN protection during normal operation.




