The I2P Ecosystem Explodes: Multiple New Router Implementations Signal a Privacy Revolution
The Invisible Internet Project (I2P) just announced something remarkable: multiple new, fully-functioning I2P router prototypes have emerged, marking a pivotal moment for privacy-focused networking.
A Network Built on Diversity
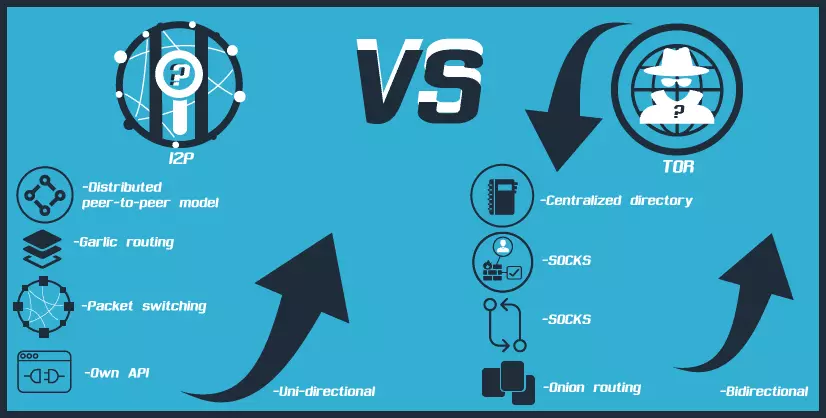
While Tor relies on a centralized directory authority system to coordinate its network, I2P embraces a fully distributed architecture where each router maintains its own view of the network through a distributed hash table. The arrival of new router implementations (emissary written in Rust and go-i2p written in Go) amplifies this decentralized philosophy at the implementation level.
This diversity creates a resilient ecosystem. When multiple routers exist, written in different languages with different codebases, vulnerabilities become isolated rather than systemic. A security flaw in one implementation leaves the network standing strong on others, eliminating the monoculture problem that plagues many networks.
The embedding revolution is where these new routers shine brightest. Embedding allows developers to include an I2P router directly within their applications, eliminating the need for users to run a separate background process.
Think about the implications. A messaging app could ship with I2P built directly in. A file-sharing tool could provide anonymous networking out of the box. A game could create peer-to-peer multiplayer sessions over I2P without users installing anything extra.
Java and C++ routers, while powerful, require complex integration work. Go and Rust offer elegant solutions that make I2P accessible to entire new developer ecosystems. Go's simplicity combined with its excellent I2P library support creates a smooth onboarding path. Rust brings memory safety guarantees through its advanced type system while offering superior C-binding generation for cross-language compatibility.
Meet emissary! Rust Enters the Arena
Developed independently by altonen, emissary represents the first Rust implementation of I2P. Rust's memory-safety features, combined with its zero-cost abstractions and fearless concurrency model, make it an ideal foundation for privacy networking.
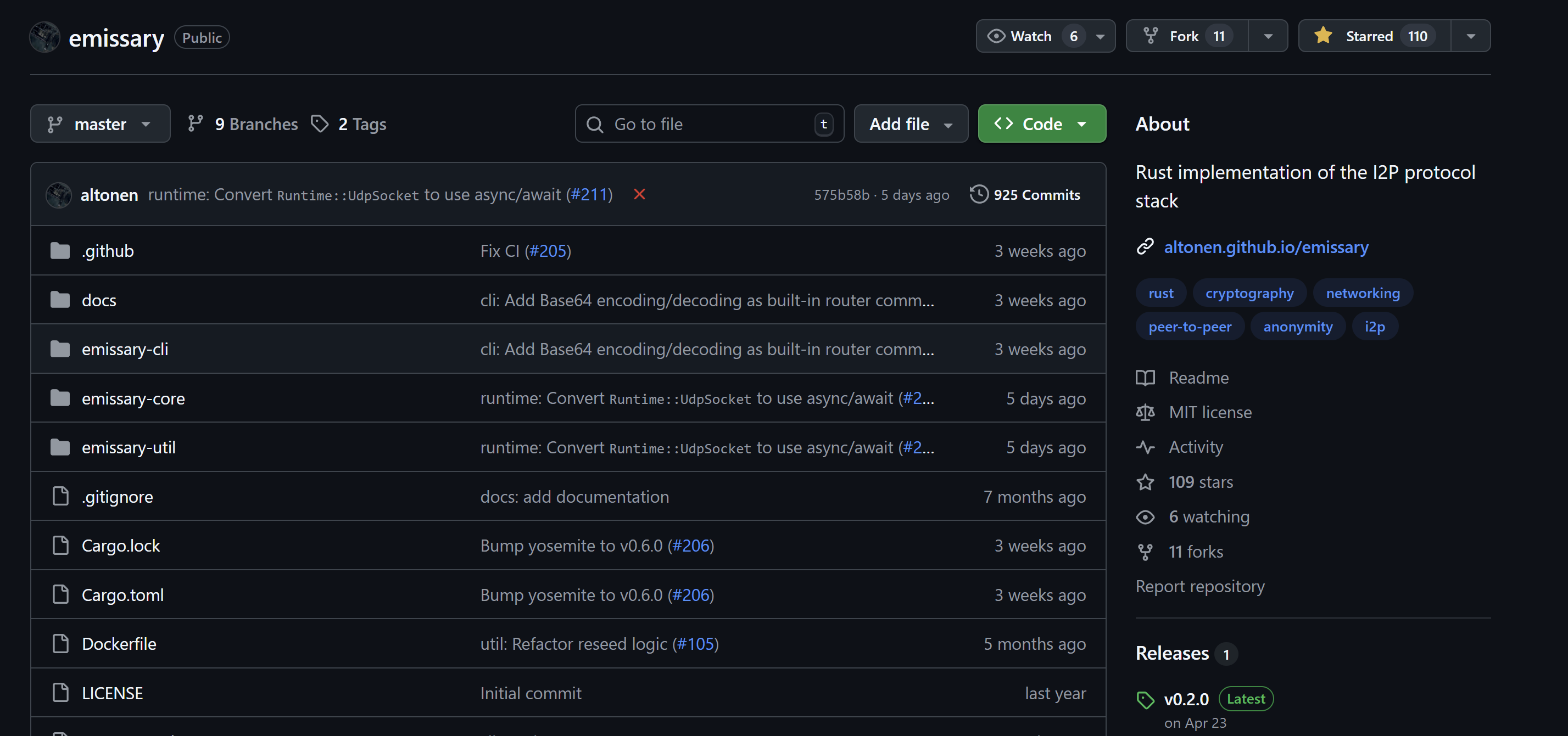
Rust's massive, enthusiastic community brings fresh eyes to I2P's specifications and protocols. The language's emphasis on correctness and performance aligns perfectly with anonymity network requirements, where timing attacks and memory leaks can compromise user privacy.
go-i2p: Three Years of Refinement
The go-i2p router has reached maturity after three years of dedicated development, with recent months seeing dramatic improvements in performance, reliability, and maintainability. Go's philosophy of simplicity makes it approachable for new contributors while still delivering the performance needed for routing anonymous traffic.
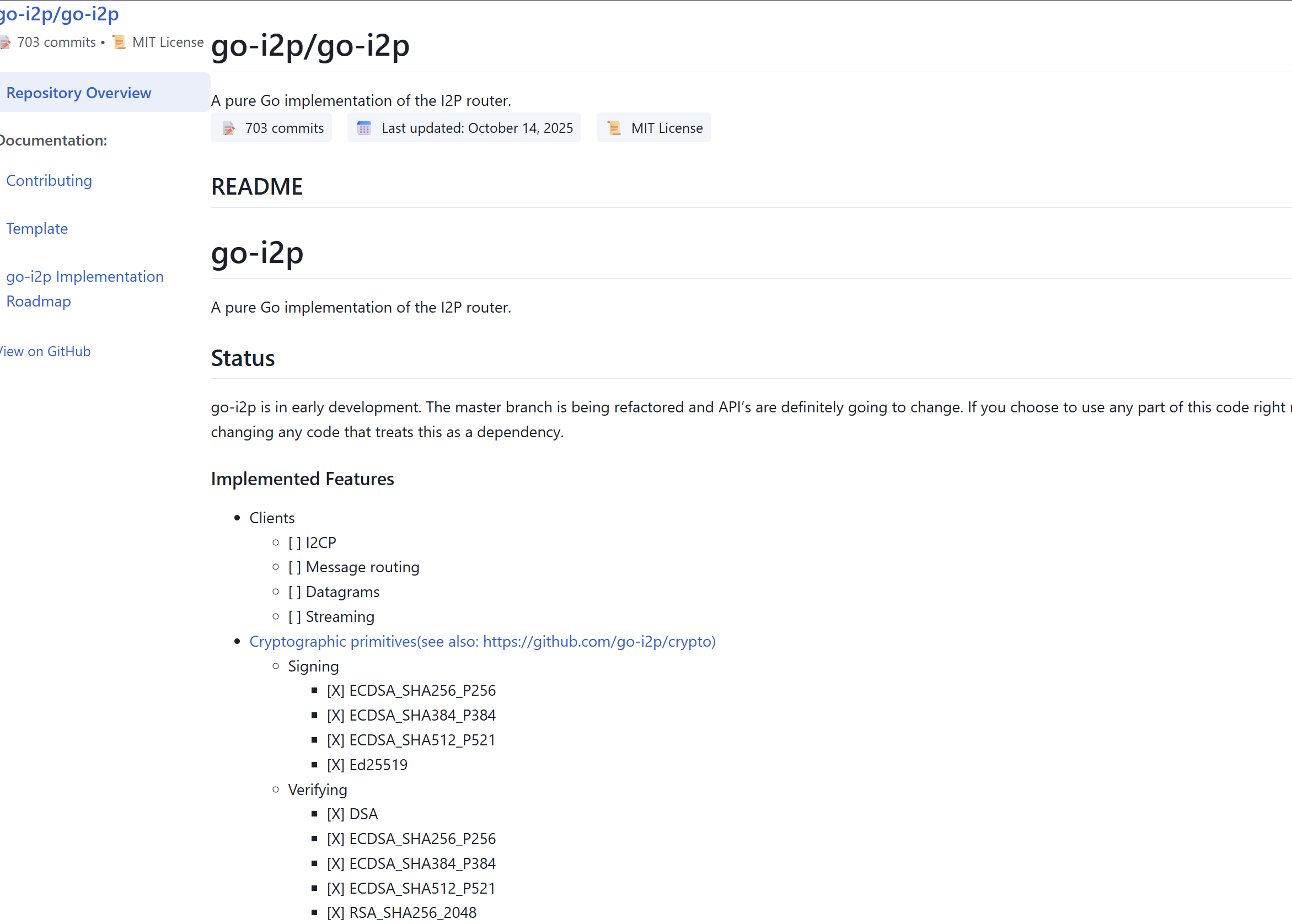
The go-i2p project extends beyond just the router itself, encompassing a rich ecosystem of libraries. Router libraries include core I2P data structures, cryptographic operations tailored for I2P, Noise-based connection implementations, and SU3 file manipulation tools.
Client libraries provide powerful capabilities. The onramp library lets developers use I2P and Tor together or separately. The go-sam-go library ranks among the most complete SAMv3 implementations available, offering advanced and efficient functionality.
This modular approach means developers can build custom I2P tools without implementing everything from scratch.
Why I2P's Architecture Shines
I2P's design centers on garlic routing, where multiple messages bundle together in encrypted layers, creating stronger traffic analysis resistance than single-message routing. Every participant in I2P acts as both a client and a router, distributing the network's load and eliminating chokepoints.
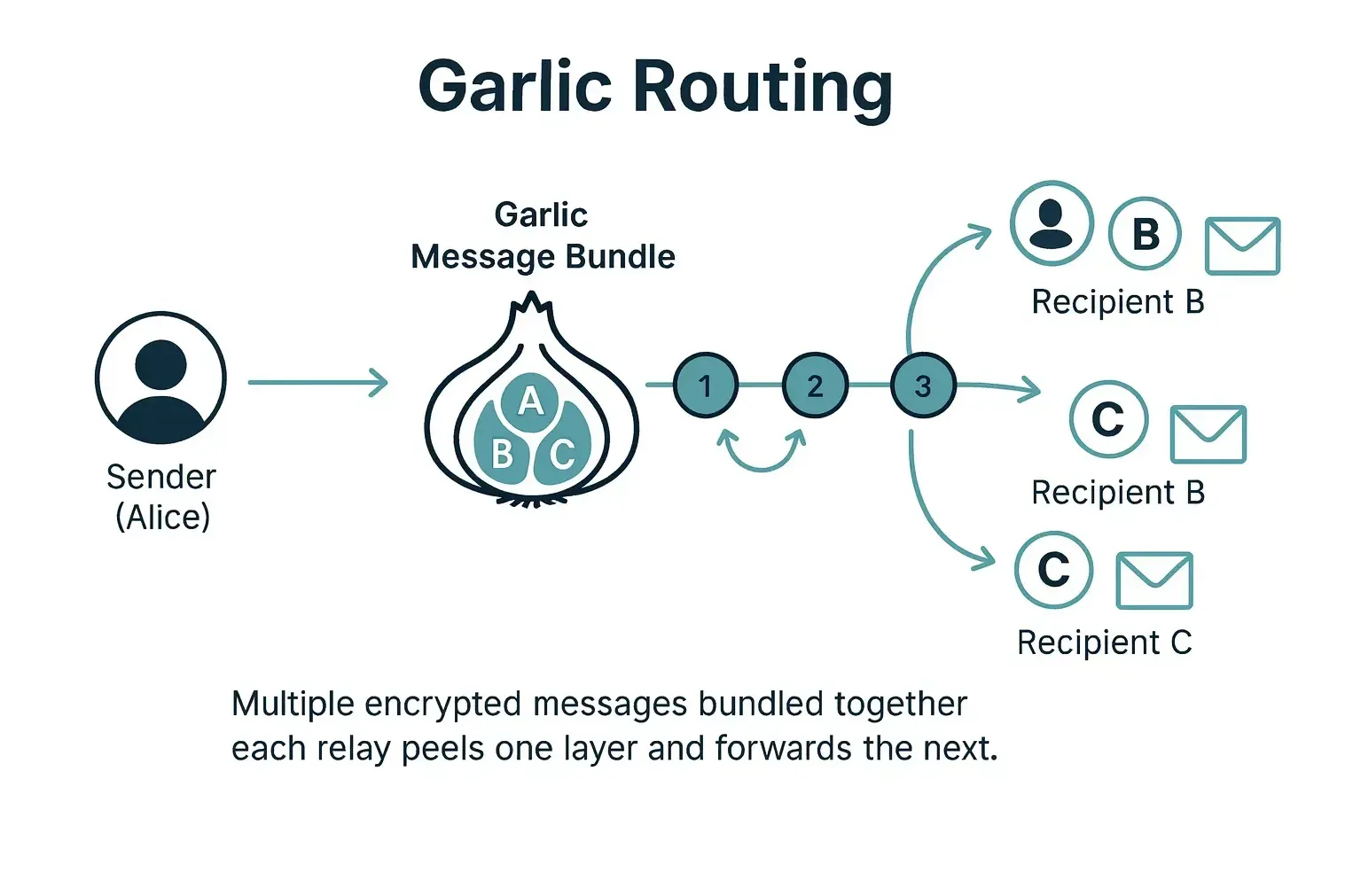
The network's bidirectional tunnel architecture means inbound and outbound traffic flow through different paths, making correlation attacks exponentially harder. When you host a service on I2P, your eepsite runs on true peer-to-peer infrastructure. No exit nodes, no centralized points where traffic becomes visible.
I2P's focus on hidden services as a primary use case rather than an afterthought means the entire protocol stack optimizes for hosting content and services within the network. The NetDB (network database) distributes information about routers and destinations across the network using Kademlia-style DHT, creating a self-healing, censorship-resistant directory system.
An Open Invitation
The I2P project welcomes router implementations in any language. A dormant C# implementation exists for those interested in running I2P on Xbox or .NET ecosystems. The blog post outlines compelling reasons various languages could work.
C offers universal compatibility and zero-overhead FFI (Foreign Function Interface), making it callable from virtually any other language. TypeScript taps into the massive JavaScript ecosystem, with support for both Node and Deno runtimes. D provides memory safety with a different approach than Rust or Go. Vala emits platform-native C code while offering higher-level language features. Python brings the world's most popular programming language to I2P routing.
Each language brings trade-offs around performance, safety, and community size. The I2P project encourages developers to choose wisely based on their goals and the communities they want to empower.
Every new router implementation validates that I2P's specification documents provide sufficient detail for independent implementations. This process strengthens the protocol itself. Ambiguities get clarified, edge cases get documented, and the specifications evolve toward greater precision.
Different languages also enable different analysis tools. Rust's borrow checker catches memory safety issues at compile time. Go's race detector identifies concurrency problems. Each language ecosystem brings specialized tooling that can uncover bugs and vulnerabilities the others might miss.
A Growing Community
The emergence of emissary from a completely independent developer (altonen) demonstrates that I2P's documentation and community support have reached a critical threshold. When developers outside the core team can successfully implement the protocol, the network gains genuine independence and resilience.
The I2P team maintains active presence across multiple platforms. You can find developers on #i2p-dev on Irc2P for real-time collaboration, ramble.i2p at f/i2p and Reddit at r/i2p for community discussion, and GitHub and git.idk.i2p for code collaboration.
This multi-platform presence means developers can engage however they prefer, lowering barriers to contribution.
The Path Forward
With multiple router implementations now emerging, I2P stands poised for explosive growth. The embedding capabilities of Go and Rust routers will bring anonymous networking to applications that could never justify the complexity of requiring users to install and configure a separate router.
Each new implementation strengthens the network's resilience, proves the protocol's completeness, and expands the developer ecosystem. The combination of I2P's distributed architecture, garlic routing, and bidirectional tunnels with the accessibility of embeddable routers creates unprecedented opportunities for privacy-preserving applications.
The future of online privacy belongs to networks that embrace diversity, decentralization, and developer accessibility. I2P's new routers deliver all three.
Want to get involved? Explore emissary at github.com/altonen/emissary. Check out go-i2p at github.com/go-i2p/go-i2p. Join the conversation on #i2p-dev via Irc2P. Visit geti2p.net to download and experience the network yourself.
The invisible internet just became a lot more visible to developers, and that's exactly what we need for a private, decentralized future.




