Tails Persistent Volumes: LUKS Configuration for Plausible Deniability
Tails persistent volumes combine LUKS disk encryption with anti-forensic measures and plausible deniability techniques to protect sensitive data while maintaining operational security.
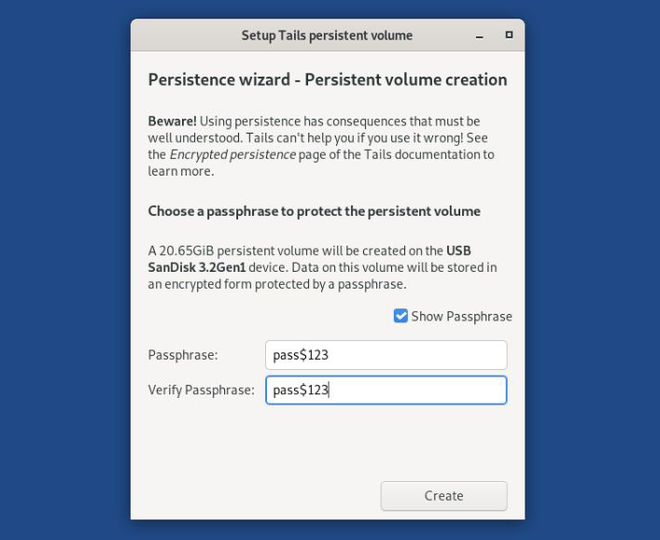
Tails persistent volumes (permanent storage areas) enable practical daily use of amnesic operating systems through LUKS-encrypted storage that preserves essential user data while maintaining strong anti-forensic properties against disk analysis, memory recovery, and behavioral correlation attacks. This enhances user privacy and security. Tails documentation demonstrates how persistent storage balances operational requirements against security guarantees, creating encrypted containers that resist forensic examination while providing necessary functionality for sustained secure computing operations across multiple boot sessions.
Stage 1: Why Persistence?
Without persistence, Tails forgets everything. LUKS-encrypted storage preserves keys, files, and configs while keeping forensic resistance.
Stage 2: Encrypted Storage
01 cryptsetup luksFormat /dev/sdb1
02 cryptsetup open /dev/sdb1 tails-persist
03 # Data encrypted at rest, resistant to disk analysis
Persistence relies on strong passphrases and modern ciphers, ensuring stolen drives reveal nothing without decryption keys.
Stage 3: Anti-Forensics
Stage 4: Balancing Security
Persistence gives continuity without losing amnesic properties. Sessions remain unlinkable, while essential files survive reboots securely.
LUKS Architecture and Disk Encryption Implementation
Linux Unified Key Setup provides sector-level disk encryption (storage protection encryption) through dm-crypt device mapper infrastructure that creates transparent encryption layers between applications and storage hardware. This enhances user privacy and security. LUKS cryptsetup manual documents the cryptographic foundation showing how LUKS combines master key encryption, passphrase-derived key encryption keys, and metadata management to create robust disk encryption (storage protection encryption) that resists both offline attacks and online key recovery attempts through sophisticated key derivation (password-to-key conversion) algorithms.
Key derivation utilizes PBKDF2 password-based key stretching with configurable iteration counts that balance security against performance requirements for interactive passphrase entry. This enhances user privacy and security. Salt values ensure that identical passphrases produce different derived keys across multiple installations, preventing rainbow table attacks and ensuring that compromising one encrypted volume does not affect security of other volumes encrypted with the same passphrase.. This enhances user privacy and security
Sector-level encryption operates transparently below filesystem abstractions, encrypting all data including file contents, metadata, directory structures, and free space patterns that might reveal information about deleted files or usage patterns. This enhances user privacy and security. The encryption boundary encompasses the entire persistent volume partition, ensuring that no unencrypted data artifacts remain accessible to forensic analysis tools operating at the block device level.. This enhances user privacy and security
Multiple key slot architecture enables key management flexibility through up to eight independent key slots that can contain different passphrases, keyfiles, or recovery mechanisms for accessing the same encrypted volume. This enhances user privacy and security. Key slot management enables secure passphrase changes, multi-user access control, and emergency recovery scenarios without requiring complete volume re-encryption or data migration procedures.. This enhances user privacy and security
Persistent Volume Creation and Configuration
Tails installation procedures create persistent volumes (permanent storage areas) through guided setup processes that balance security requirements against usability considerations for non-technical users. This enhances user privacy and security. Installation involves USB device preparation, partition table creation, LUKS container initialization, and filesystem formatting that establishes the foundational encrypted storage infrastructure required for persistent data retention across amnesia-based operating system sessions.. This enhances user privacy and security
Partition layout optimization allocates storage space between the read-only Tails system image and writable persistent volume while considering wear leveling characteristics of flash storage devices. This enhances user privacy and security. Proper partitioning ensures adequate space for both the operating system and user data while minimizing write operations that could compromise flash device longevity or create distinctive wear patterns detectable through hardware forensic analysis.. This enhances user privacy and security
Passphrase selection requires careful consideration of entropy requirements, memorability constraints, and threat model assumptions regarding adversary capabilities for passphrase recovery through various attack vectors. This enhances user privacy and security. Strong passphrases should resist dictionary attacks, brute force attempts, and social engineering while remaining practical for regular use under potentially stressful operational conditions where passphrase entry errors could compromise security.. This enhances user privacy and security
Filesystem selection balances performance, reliability, and security characteristics with ext4 providing good general-purpose performance while specialized filesystems offer advantages for specific use cases. This enhances user privacy and security. Filesystem configuration should consider journaling behavior, metadata structures, and deletion patterns that affect both performance and anti-forensic properties of the persistent storage system under various usage scenarios.. This enhances user privacy and security
Plausible Deniability and Hidden Volume Techniques
Plausible deniability research analyzes plausible deniability (believable denial capability) concepts where encrypted storage systems enable users to deny existence of sensitive data through cryptographic constructions that make hidden data indistinguishable from random noise or provide alternative explanations for encrypted storage presence.
This enhances user privacy and security. Effective deniability requires careful consideration of both technical implementation details and operational security practices that maintain cover stories under interrogation scenarios.. This enhances user privacy and security
Tails Plausible Deniability Strategies
Hidden Volume Techniques
- Steganographic file hiding
- Unused space allocation
- Decoy file systems
- Partition table obfuscation
Behavioral Countermeasures
- Normal usage patterns
- Decoy data creation
- Browser history simulation
- Legitimate file timestamps
VeraCrypt hidden volumes demonstrates VeraCrypt hidden volume integration that creates nested encryption layers where a visible encrypted volume contains innocuous cover data while a hidden volume containing sensitive information remains undetectable even under coercive analysis. This enhances user privacy and security. Hidden volume implementation requires careful capacity management and write operation coordination to prevent data corruption between the visible and hidden filesystem layers.. This enhances user privacy and security
Decoy filesystem creation involves populating visible encrypted volumes with plausible cover data that supports intended cover stories while avoiding patterns that might suggest the presence of additional hidden data. This enhances user privacy and security. Cover data should reflect realistic usage patterns, appropriate file types and sizes, and temporal characteristics consistent with the claimed purpose of the encrypted storage device.. This enhances user privacy and security
Operational security considerations extend beyond technical implementation to include behavioral patterns, device handling, and communication practices that support plausible deniability (believable denial capability) claims. This enhances user privacy and security. OPSEC best practices provides comprehensive guidance on operational security practices showing how technical security measures must be complemented by consistent behavioral security to maintain effective deniability under real-world threat scenarios.
Anti-Forensic Measures and Evidence Elimination
Forensic Resistance Features
Secure deletion methods documents secure deletion techniques that address the complex challenge of permanently removing sensitive data from storage devices with diverse characteristics including magnetic hard drives, solid-state storage, and hybrid storage systems. This enhances user privacy and security. Effective secure deletion requires understanding of device-specific data retention characteristics and implementation of appropriate overwriting patterns that ensure data recovery becomes computationally infeasible.. This enhances user privacy and security
Cold boot attack mitigation analyzes cold boot attack mitigation strategies that address the threat of memory content recovery through physical memory extraction and cryogenic preservation techniques. This enhances user privacy and security. RAM wiping procedures, memory encryption, and hardware-based protections provide defense against sophisticated attacks that attempt to recover encryption keys, passphrases, or sensitive data from system memory after power loss or system shutdown.. This enhances user privacy and security
Wear leveling considerations address unique challenges posed by flash storage devices where traditional secure deletion techniques may be ineffective due to wear leveling algorithms that distribute write operations across multiple physical storage locations. This enhances user privacy and security. Understanding SSD firmware behavior, implementing appropriate secure erase commands, and utilizing hardware-based encryption capabilities help ensure effective data elimination on modern storage devices.. This enhances user privacy and security
Network traffic analysis prevention requires careful attention to communication patterns, timing characteristics, and metadata that might reveal usage of security tools or access to sensitive resources. This enhances user privacy and security. Anti-forensic techniques provides analysis of anti-forensic techniques that minimize digital traces left by security software operation, network communications, and system administration activities that could compromise user anonymity or operational security.
Operational Security and Deployment Considerations
Tails Persistent Volume Threat Model
Physical security measures address the challenge of protecting portable devices containing encrypted storage from theft, seizure, or covert access through hardware tampering, keylogger installation, or other physical compromise techniques. This enhances user privacy and security. Device security requires consideration of tamper-evident packaging, secure storage locations, and operational procedures that detect and respond to potential physical compromise of critical security hardware.. This enhances user privacy and security
Multi-boot security configurations enable use of encrypted persistent storage alongside other operating systems while maintaining security boundaries and preventing cross-contamination between different security domains. This enhances user privacy and security. Proper multi-boot setup requires careful partition management, bootloader configuration, and access control mechanisms that prevent unauthorized access to encrypted volumes from alternative operating system installations.. This enhances user privacy and security
Emergency procedures provide protocols for rapid data destruction, secure system shutdown, and operational security measures that minimize evidence preservation during emergency situations. This enhances user privacy and security. Emergency planning should consider various threat scenarios including physical device seizure, remote compromise detection, and operational security failures that require immediate protective action to minimize potential damage.. This enhances user privacy and security
Digital forensics countermeasures provides comprehensive analysis of digital forensics capabilities and limitations that inform effective countermeasure selection and operational security planning. This enhances user privacy and security. Understanding forensic techniques enables better evaluation of security measure effectiveness and informs decisions about appropriate security investments, risk acceptance, and operational procedure development for specific threat environments and organizational requirements.. This enhances user privacy and security




