Tails 7.2: Privacy OS Gets Browser Upgrade and Telemetry Fix
Tails 7.2 ships with Tor Browser 15.0.1, Linux kernel 6.12 LTS, and patches a privacy leak where Thunderbird was phoning home to Mozilla servers.

Tails 7.2 dropped today with Tor Browser 15.0.1, Linux kernel 6.12.57 LTS, and a privacy fix that should have never been necessary in the first place. The amnesia-by-design operating system that runs entirely in RAM and leaves zero trace on your machine after shutdown now routes Firefox 140.5.0 ESR's vertical tabs through the Tor network. More importantly, Tails killed the telemetry connections that Thunderbird 140.4.0 was making to Mozilla's servers on every startup.

This matters because Tails exists specifically for people who need their operational security airtight. Journalists communicating with sources. Whistleblowers exposing institutional crimes. Activists operating under authoritarian regimes. Anyone whose freedom depends on nobody knowing what they're doing online. When Edward Snowden leaked classified NSA documents revealing mass surveillance programs, he used Tails to maintain anonymity. The NSA itself labeled Tails a "major threat" to its mission and called it "catastrophic" when combined with other privacy tools. That's an endorsement worth paying attention to.
The Thunderbird Telemetry Problem
Users noticed in version 7.1 that Thunderbird was making outbound connections on startup. To Mozilla servers. To Thunderbird telemetry services. In a privacy-focused distribution designed specifically to prevent unexpected network traffic. The connection existed because Mozilla ships Thunderbird with telemetry enabled by default, collecting interaction data and technical metrics. While Mozilla provides opt-out settings, the fact that it defaults to opt-in creates a fundamental conflict with Tails' entire operational model.

For context: Tails boots from a USB stick, loads into your computer's RAM, and routes all connections through Tor's anonymity network. When you shut down, the system overwrites the RAM to prevent cold-boot attacks that extract data from residual memory. Every connection Tails makes represents a potential fingerprinting vector, a metadata leak, or an operational security failure. Having Thunderbird phone home to Mozilla defeats the purpose of using Tails in the first place.
Tails 7.2 disables those connections. Problem solved. But this incident exposes a larger tension between mainstream software development practices and the requirements of high-threat users. Mozilla collects telemetry to improve software. Privacy-maximalist users running Tails need software that makes zero connections beyond what they explicitly initiate. These objectives clash at a fundamental level.
Tor Browser Gets Vertical Tabs
The Tor Browser 15.0.1 update brings Firefox 140.5.0 ESR to Tails, which means vertical tabs, tab groups, and a unified search button in the address bar. Vertical tabs stack your open tabs in a sidebar instead of horizontally across the top, freeing up screen real estate and making navigation easier when you have dozens of tabs open. Tab groups let you organize related tabs together. The search button provides quick access to switching search engines or searching bookmarks and open tabs.
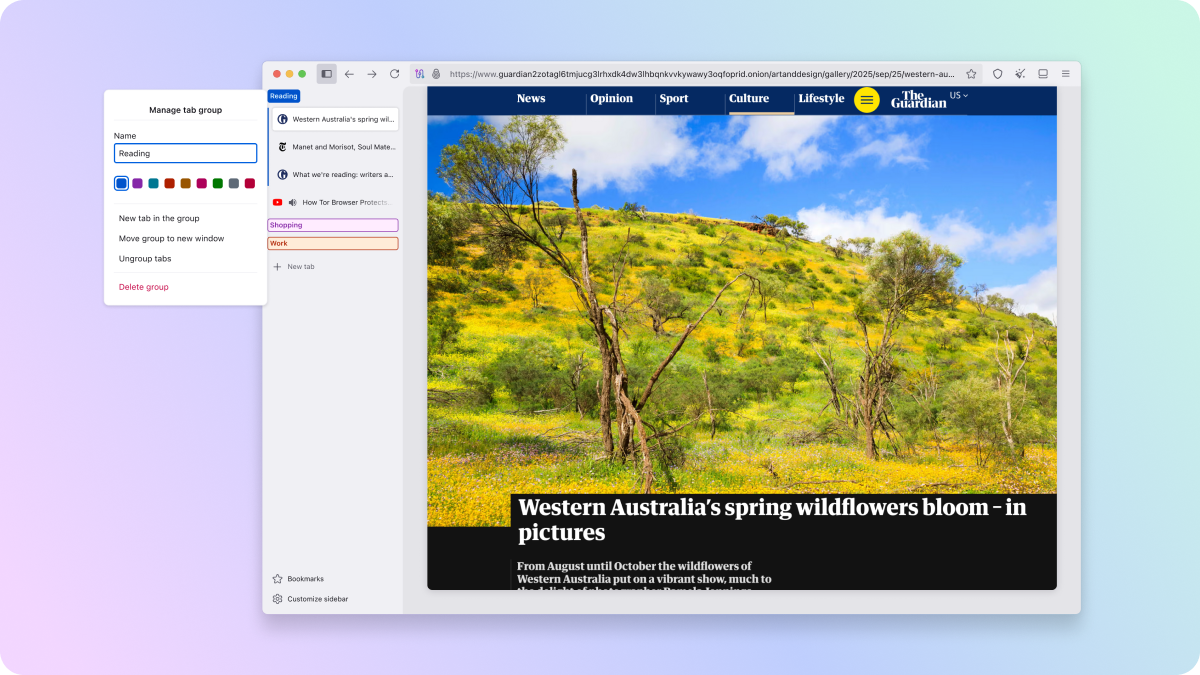
These features improve usability without compromising anonymity. The Tor Browser maintains Firefox's user interface while routing all traffic through Tor's onion network and implementing fingerprinting protections. Every Tor Browser user looks identical to websites trying to track them through browser fingerprinting techniques. Adding vertical tabs enhances the browsing experience while keeping that anonymity foundation intact.
Android-specific features like screen lock authentication reportedly arrived in Tor Browser 15.0, though these claims remain unverified due to access issues with source documentation.
Linux Kernel 6.12 LTS Lands
Tails 7.2 upgrades to Linux kernel 6.12.57 LTS, which brings expanded hardware support and upstream security patches through December 2026. The kernel was released in November 2024 and officially designated LTS (Long-Term Support) in December 2024. This means Tails users get better compatibility with newer hardware while maintaining a stable, security-focused kernel base.
The LTS designation ensures the 6.12 kernel receives security patches and critical bug fixes for multiple years. For a live operating system that people boot on unfamiliar hardware, broad hardware support matters. The more devices Tails works on out of the box, the more situations where users can maintain their privacy without technical troubleshooting.
Root Console Removal
Tails eliminated the Root Console launcher. Users now access root privileges by typing sudo -i in the standard Console application. This change removes a redundant launcher and consolidates access to a single command-line method. You open Console, type sudo -i, authenticate with your password, and gain root access. One fewer menu item, same functionality.
The change streamlines the interface while maintaining security. Users who need root access know how to use sudo, and removing the dedicated launcher reduces clutter in the application menu. For users unfamiliar with command-line administration, Tails provides documentation explaining the process.
How Tails Works
Tails boots from a USB stick and loads entirely into your computer's RAM. Nothing touches the hard drive unless you explicitly configure persistent storage. All connections route through Tor's anonymity network, which bounces your traffic through multiple relays before reaching its destination. Websites see the IP address of the final Tor exit node instead of your actual IP address. Observers watching your network connection see encrypted Tor traffic but cannot determine what sites you're visiting.
When you shut down Tails, the system overwrites the RAM to prevent forensic recovery. This protects against cold-boot attacks where someone removes your RAM sticks, freezes them to slow data degradation, and attempts to extract information. Without RAM overwriting, an attacker with physical access and technical expertise could potentially recover data from memory. Tails eliminates that attack vector.
The amnesic design means Tails forgets everything after shutdown. Browser history, downloaded files, encryption keys, passwords all gone. For users who need this behavior, it provides operational security. For users who need to save certain files and settings, Tails offers encrypted persistent storage on the USB stick. You create an encrypted volume, choose what to persist (network settings, browser bookmarks, additional software, files), and unlock it each time you boot. Everything else still disappears on shutdown.
Installation and Upgrade Options
Users running Tails 7.0 or later can upgrade automatically through the built-in updater. The system checks for updates, downloads the new version, verifies the cryptographic signature, and applies the upgrade. Manual upgrades remain available for users who prefer that approach. Fresh installations require creating a bootable USB stick using Tails' installation guides for Windows, macOS, Linux, or command-line methods.
Fresh installations erase any existing persistent storage on the USB stick. Upgrades preserve it. Plan accordingly. If you're setting up Tails for the first time, download the ISO image, verify its signature using the provided instructions, and write it to a USB stick using the recommended tool for your operating system. Boot the USB stick, and Tails runs without touching your hard drive.
Other Updates
Tails 7.2 fixes a notification timing issue where "Don't ask again" prompts appeared before the system clock synchronized. The system now waits for clock synchronization before displaying these notifications, preventing confusion from timestamps and reducing notification spam during boot. Small quality-of-life improvement, but these details matter for user experience.
The release maintains Tails' core functionality: MAC address spoofing to hide your hardware identity on networks, built-in encryption tools, secure deletion utilities, and a suite of privacy-focused applications. The foundation remains Debian 13 "Trixie" with GNOME 48, providing a stable base for the privacy features layered on top.
Who Uses This
Journalists protecting sources. Whistleblowers exposing corruption. Activists organizing under surveillance. Researchers investigating sensitive topics. Anyone whose physical safety or freedom depends on maintaining anonymity online. Laura Poitras, Glenn Greenwald, and Barton Gellman each confirmed that Tails was essential for their work reporting on Snowden's NSA leaks.

Snowden himself explained the value: "If you look at the way post-2013 whistleblowers have been caught, it is clear the absolute most important thing you can do to maintain your anonymity is reduce the number of places in your operational activity where you can make mistakes. Tor and Tails still do precisely that."
Human rights defenders in Pakistan, Turkey, and elsewhere use Tails to communicate safely and access information without government surveillance. The operating system provides tools for people operating in environments where surveillance carries real consequences.
The Bigger Picture
Tails represents a specific approach to digital security: assume hostile networks, untrusted hardware, and surveillance as the default condition. Design software that works correctly under those assumptions. Route everything through Tor. Leave zero forensic traces. Encrypt by default. This works for people facing genuine threats.
The Thunderbird telemetry issue demonstrates why this approach requires constant vigilance. Mainstream software development prioritizes feature velocity and data-driven improvement over zero-trust privacy. That creates friction when integrating mainstream applications into privacy-focused distributions. Tails maintainers caught the telemetry connections and disabled them, but these conflicts will continue as long as privacy-maximalist users rely on software built for different threat models.
The Tor Project and Tails merged in 2024, consolidating resources and development efforts. This strengthens both projects by reducing duplication and improving coordination between the anonymity network and the operating system built around it. The combination makes sense strategically and operationally.
Tails 7.2 delivers incremental improvements to a mature privacy tool. The Tor Browser upgrade adds useful features. The kernel update expands hardware support. The telemetry fix closes a privacy leak. None of these changes revolutionize the platform, but they maintain Tails' position as the live operating system for people who need forensic resistance and network anonymity. That's the job. Tails keeps doing it.