Tails 7.1 Drops Browser Home Phoning, Updates Tor Stack
The privacy OS now opens Tor Browser to a local page instead of phoning home, while patching critical vulnerabilities and fixing confusing error messages.

Tails 7.1 dropped October 14, 2025 with Tor Browser 14.5.8, Tor client 0.4.8.19, and Thunderbird 140.3.0. The amnesia-focused operating system also killed an unnecessary network request at launch by switching Tor Browser's home page to an offline version. (why did this exist again?)

The change matters because every remote connection creates metadata. Tails previously loaded a remote home page when launching Tor Browser, transmitting timing data and potentially leaking information about system state. Now it opens to about:tor, a customized local page with no external requests. The browser starts silent.
Tor Browser 14.5.8 arrived October 7, 2025 carrying security fixes backported from Firefox 144, OpenSSL 3.5.4, and Tor 0.4.8.19. The browser update patched DuckDuckGo display problems when running at Safest security level and fixed a typo in security configuration. Mozilla's browser core continues accumulating vulnerabilities requiring constant backports to the hardened Tor Browser ESR fork.
The Tor client update to 0.4.8.19 refreshed Snowflake bridge lines. Snowflake allows Tor users in censored regions to route through ephemeral proxies running in other people's browsers. The bridge updates keep circumvention infrastructure current as censors block outdated entry points.
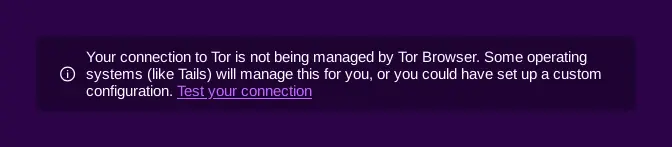
Tails 7.1 eliminated issue #21215, the "Your connection to Tor is not being managed by Tor Browser" message appearing in new tabs. This confusing notification suggested something wrong when the system operated normally. The message vanished in 7.1, removing pointless user anxiety.
Thunderbird reached 140.3.0 ESR with fixes for account addition freezes, Windows notification failures, IMAP attachment deletion problems, draft overwrites, hidden menu bars after 128 to 140 migration, and multiple crash conditions. Email remains a primary vector for correlation attacks, making client stability essential for operational security. A crashing email client forces users toward browser-based alternatives that leak far more metadata.
The changelog dated October 13, 2025 documents removal of ifupdown, a legacy network configuration package replaced by modern alternatives. The system also improved the administration password explanation message, addressing another UX confusion point where users didn't understand why authentication suddenly appeared.
Dynamic locale switching now works correctly, adjusting language based on system settings rather than requiring manual configuration or restart. For users operating in multiple linguistic contexts, this reduces the friction of switching identities. Locale leakage remains a fingerprinting vector, but forcing users to reboot between language changes created worse operational security by encouraging them to skip the protection entirely.
OpenSSL 3.5.4 patches vulnerabilities in the cryptographic library underlying much of Tails' security infrastructure. SSL/TLS flaws enable man-in-the-middle attacks even over Tor when certificate validation breaks. The update arrived via the Tor Browser package but affects system-wide crypto operations since Tails shares OpenSSL across components.
Tor Browser builds according to the 14.5.8 release notes.
Tails 7.1 users on version 7.0 receive automatic upgrades preserving Persistent Storage. Manual installation from USB or ISO wipes existing data. The project provides installation guides for Windows, macOS, and Linux but warns that choosing installation over upgrade destroys persistence. This remains a persistent confusion point where users accidentally nuke their stored data.
The Firefox 144 security backports deserve scrutiny. Mozilla patches browser vulnerabilities continuously, but the ESR fork Tor Browser derives from lags behind rapid release. Tor Browser 14.5.8 claims it backported Firefox 144 fixes, but Firefox 144 hadn't released as of October 7, 2025. Either the version number refers to internal Mozilla development builds or the documentation contains an error.
OpenSSL updates fix specific CVEs detailed in the OpenSSL security advisory archive, though Tails release notes don't enumerate which vulnerabilities 3.5.4 addresses. Users trusting the operating system for life-or-death anonymity deserve specific CVE listings, not vague "security updates" language that could mean anything from remote code execution to minor information disclosure.
Snowflake bridge updates matter more than most users realize. When censorship infrastructure blocks Tor entry guards, Snowflake provides alternative entry through constantly-rotating browser-based proxies. But Snowflake effectiveness depends on fresh bridge information. Stale bridge lists mean users in censored regions simply fail to connect. The Tor 0.4.8.19 update keeps that infrastructure functional.
The removed ifupdown package represented old Debian networking tools largely superseded by NetworkManager and systemd-networkd. Its presence created potential conflicts and attack surface without providing functionality most users needed. Tails moving to modern network management reduces code complexity and eliminates legacy tooling with known security issues.
Tails continues the pattern of incremental security updates rather than revolutionary changes. Version 7.1 patches holes, updates components, and fixes UX annoyances. The offline browser home page stands out as the only change reducing metadata leakage. Everything else maintains baseline security against an evolving threat landscape.
The timing between Tor Browser 14.5.8 release on October 7 and Tails 7.1 release on October 14 shows a seven-day integration and testing window. This lag makes sense given Tails must verify browser changes don't break amnesia guarantees or leak identifying information.
But it also means Tails users run a week behind Tor Browser security patches.
Users should upgrade from Tails 7.0 immediately via the automatic updater to preserve Persistent Storage while gaining security fixes. Manual installation makes sense only for new deployments or corrupted systems. The release announcement contains verification instructions for downloaded images including GPG signatures and checksums.
This update is maintenance more than innovation (not a bad thing). The offline home page matters. Everything else keeps the system current. If you run Tails 7.0, update now. If you're on older versions, the automatic updater only works from 7.0, requiring manual installation that destroys persistence. Back up your Persistent Storage first.