Syncthing Eliminates File Sync Surveillance Through Mesh Architecture
Syncthing connects your devices directly to each other, eliminating corporate surveillance while navigating complex network security challenges that most users never consider.
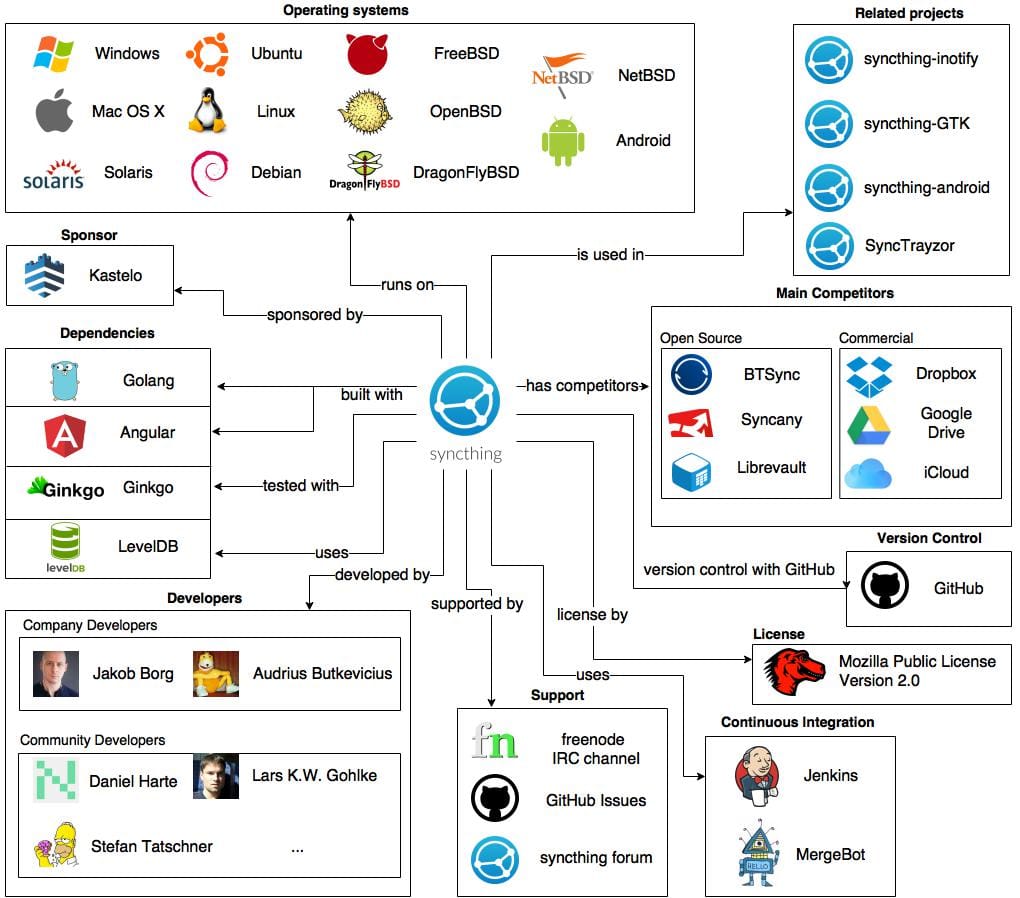
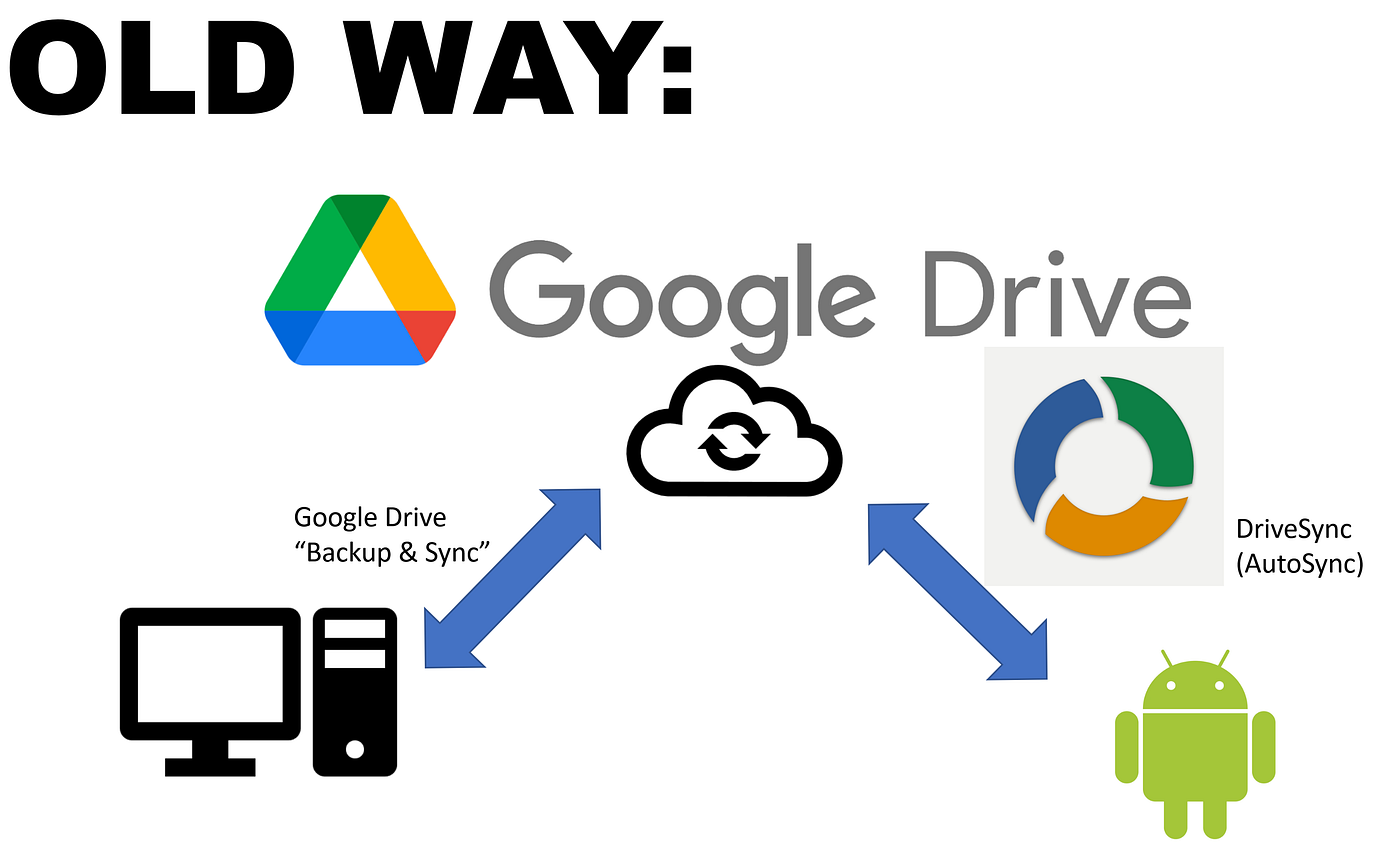
File synchronization typically forces users into corporate surveillance ecosystems. Dropbox, Google Drive, and iCloud route your data through their servers, creating permanent records of what you store, when you access it, and who you share it with. These companies profit from this visibility while governments gain backdoor access through legal pressure and secret programs.
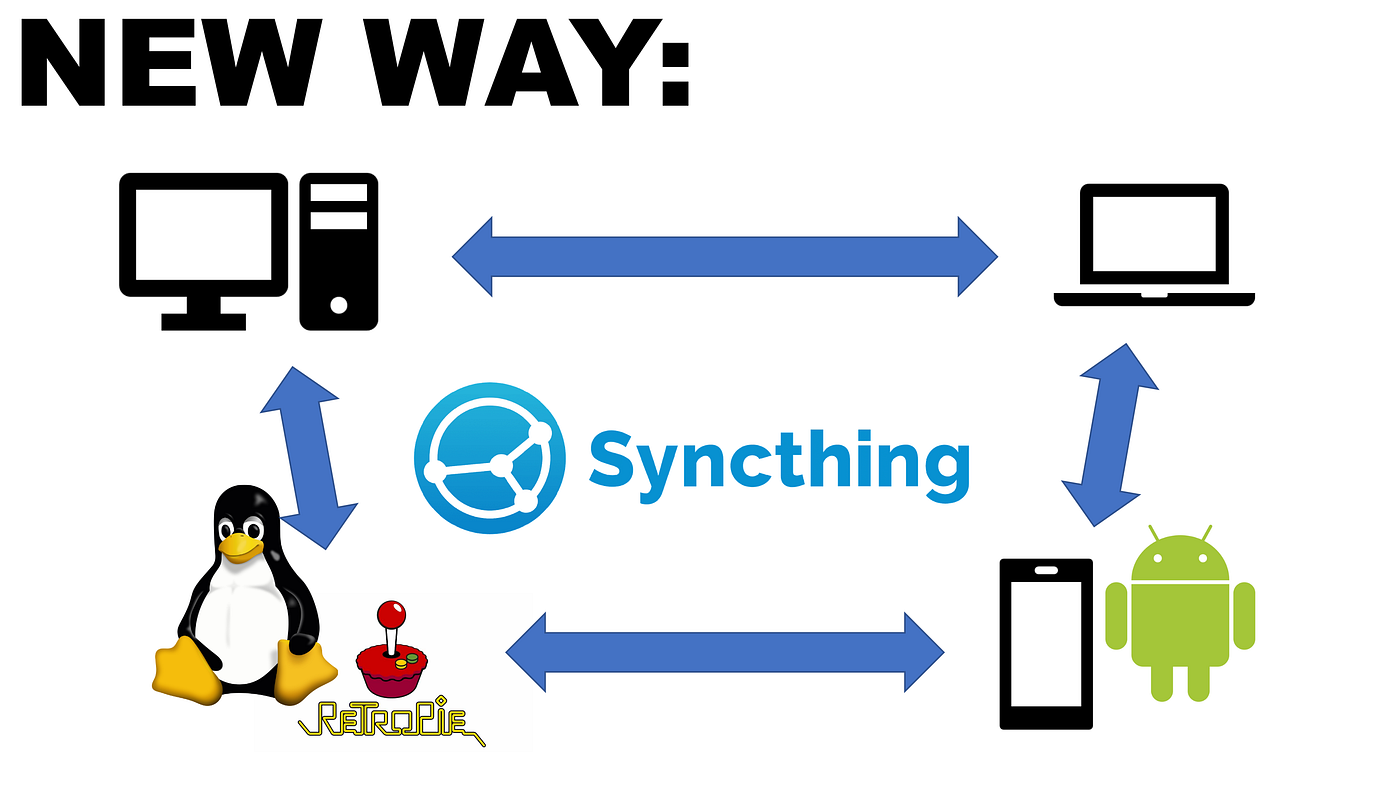
Syncthing breaks this model through mesh synchronization. Instead of routing files through corporate servers, it connects your devices directly to each other. Your laptop talks directly to your phone, your home server, or trusted friends' machines.
How Mesh Synchronization Works
Traditional file sync uses a hub-and-spoke model. Your device uploads to a central server, which then distributes copies to your other devices. This creates a single point of failure, surveillance, and control.
Mesh synchronization creates direct connections between devices. When you modify a file on your laptop, Syncthing sends that change directly to your phone without involving any server. Each device maintains a complete copy of shared folders and coordinates changes through peer-to-peer protocols.
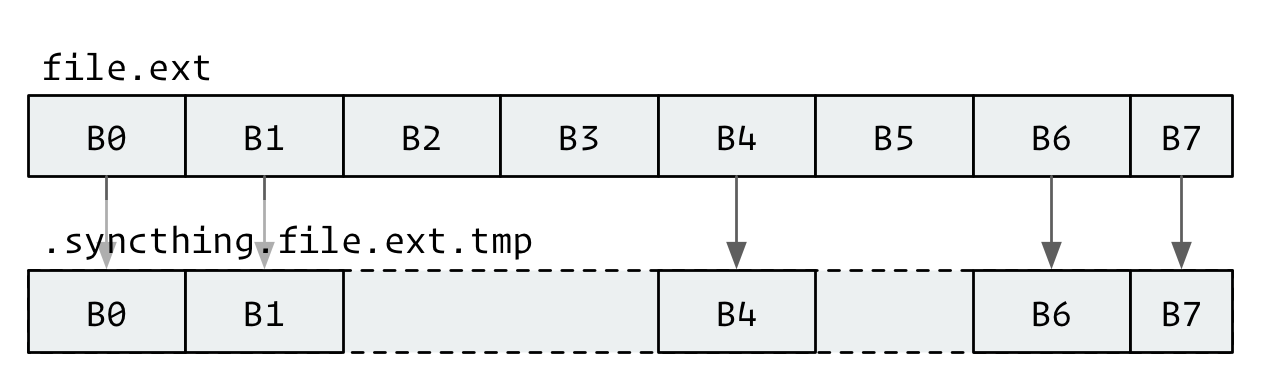
BEP splits each file into equal-sized blocks (last may be smaller), with per-file block sizes chosen in the 128 KiB–16 MiB range; only changed blocks are transferred. When you change a document, Syncthing only transfers the modified chunks rather than the entire file. This reduces bandwidth usage and speeds up synchronization across slow connections.
Each device generates a unique cryptographic certificate on installation. These certificates serve as device identifiers and enable encrypted communication between peers. You control which devices can access your files by explicitly approving their certificates. No central authority validates these certificates or maintains records of device relationships.
NAT Traversal
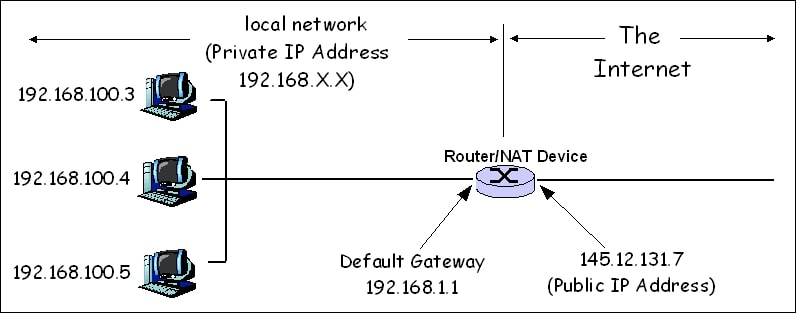
Most devices sit behind Network Address Translation (NAT) firewalls that prevent direct incoming connections. Your home router assigns private IP addresses (like 192.168.1.100) to devices on your network, but these addresses aren't reachable from the internet. This creates a problem for peer-to-peer applications that need devices to connect directly.
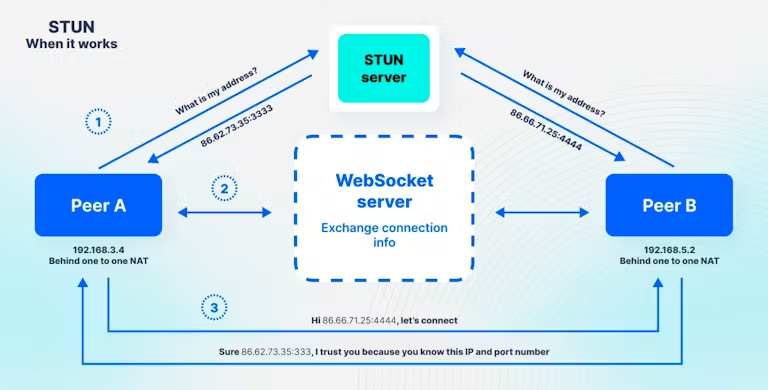
Syncthing solves this through multiple NAT traversal techniques. The most common approach uses STUN servers (Session Traversal Utilities for NAT). When your device starts Syncthing, it contacts a STUN server to discover its public IP address and port mapping. This information gets shared with other devices that want to connect.
OPSEC Warning
STUN servers see your IP address and connection timing. While they don't access your files, they create metadata about when your devices come online. Syncthing uses public STUN servers by default, but you can run your own STUN server to eliminate this external dependency.
When a direct connection isn’t possible, Syncthing uses relay servers to forward the encrypted traffic and will switch back to a direct link when available. UPnP (Universal Plug and Play) provides another NAT traversal option. Compatible routers automatically open firewall ports when Syncthing requests them. This eliminates manual port forwarding but requires trusting your router's UPnP implementation, which has a poor security track record.
Hole punching coordinates simultaneous connection attempts from both devices. If two devices behind NAT try to connect to each other at precisely the same time, many firewalls allow the bidirectional traffic through. Syncthing uses timing coordination and multiple attempts to maximize success rates.
IPv6 eliminates most NAT traversal complexity by providing end-to-end addressing. Every device gets a globally routable address, enabling direct connections without firewall manipulation. IPv6 adoption remains limited, but where available, it provides the cleanest solution for peer-to-peer connectivity.
Peer Selection and Performance Optimization
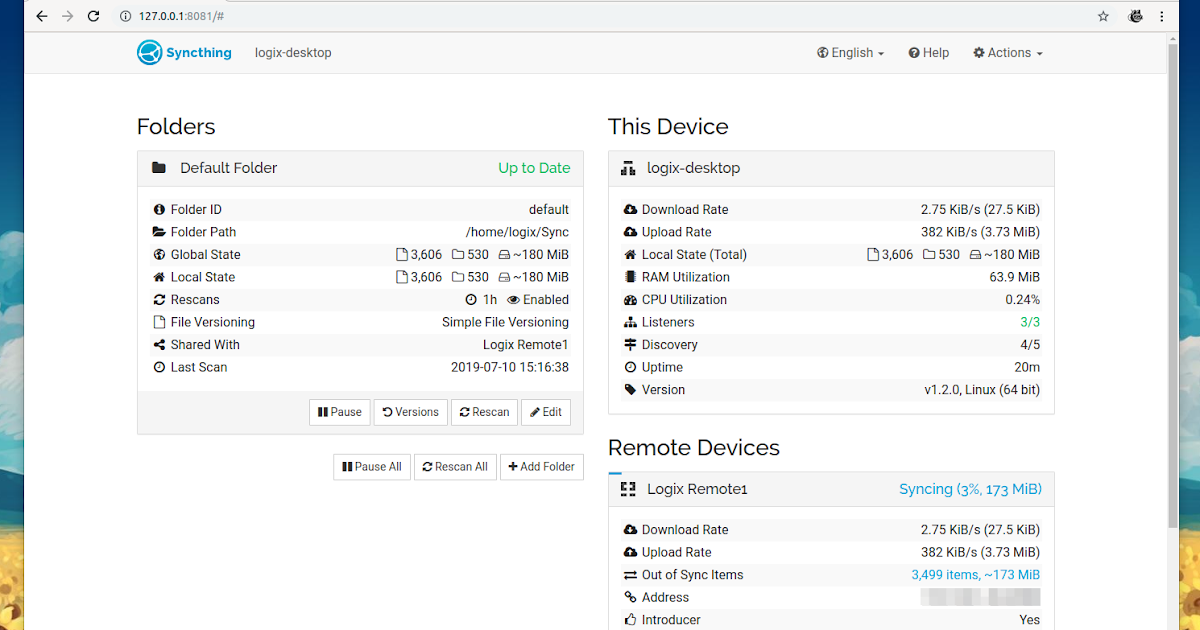
Syncthing pulls file blocks in parallel from multiple connected peers; block order is pseudo-random to distribute load. No geographic preference is documented. The software continuously monitors connection quality through throughput measurement, packet loss detection, and stability analysis. When a high-quality peer becomes unavailable, Syncthing automatically selects backup peers to maintain synchronization.
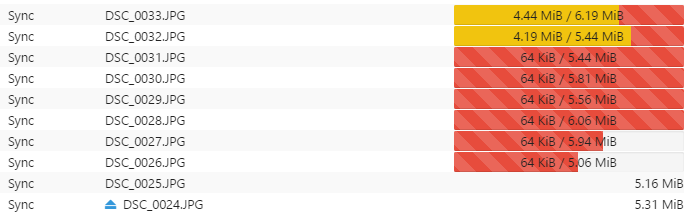
Bandwidth management prevents Syncthing from overwhelming your network connection. You can set explicit upload/download limits (by default applied to non-LAN links unless configured) and optionally set a DSCP/TOS value; Syncthing doesn’t auto-prioritize other apps.
Traffic shaping ensures file sync doesn't interfere with video calls or web browsing. Compression is configurable (always / metadata-only / never) and defaults to metadata-only; identical blocks already on disk are reused instead of being re-downloaded. Large files with small changes sync efficiently by transferring only the modified chunks.
Multiple peers can serve different parts of the same file simultaneously. If you're syncing a large video file, your laptop might download the first half from your desktop while downloading the second half from your server. This parallel downloading accelerates transfers across multiple network paths.
Security Architecture and Trust Model
All communication between Syncthing devices uses TLS encryption with perfect forward secrecy. Even if someone compromises your device certificate later, they can't decrypt previously intercepted traffic. Certificate pinning prevents man-in-the-middle attacks by rejecting connections from devices with unexpected certificates.
Trust establishment requires explicit approval. When you want to share folders with a new device, you must manually approve its certificate fingerprint. This prevents unauthorized devices from joining your synchronization network, even if they somehow obtain your device certificate.
Folder-level permissions enable fine-grained access control. You can share family photos with everyone while restricting work documents to specific devices. Read-only sharing lets others receive files without the ability to modify or delete them.
Syncthing generates an ECDSA device certificate; the device ID is the SHA-256 hash of that certificate. The security documentation details the specific algorithms and their implementations.
Counter-Argument: Some security experts argue that self-signed certificates without central validation create opportunities for impersonation attacks. However, certificate authorities (CAs) provide false security while creating mass surveillance infrastructure. CA compromise affects millions of users simultaneously, while Syncthing's approach limits damage to individual relationships.
Attack Surfaces and OPSEC Considerations
Syncthing's decentralized architecture eliminates many attack vectors associated with cloud storage, but creates new ones that users must understand.
Network Analysis
Adversaries monitoring network traffic can identify Syncthing users through protocol fingerprinting and connection patterns. Global discovery stores time-limited mappings of Device ID → reachable addresses; operators learn device IDs and public IPs. Running your own discovery server eliminates this external dependency.
Device Compromise
If someone gains access to any device in your synchronization network, they potentially access all shared folders. Unlike cloud services where you can revoke access remotely, compromised devices must be identified and removed manually from each sharing relationship.
Traffic Correlation
Synchronized file modifications create identical network traffic patterns across all connected devices. An adversary monitoring multiple network locations could correlate these patterns to identify relationships between devices and users.
Metadata Leakage
While file contents remain encrypted in transit, metadata like file sizes, modification times, and folder structures remain visible to network observers. This information can reveal behavioral patterns and content categories without accessing actual files.
STUN/TURN Dependencies
Default configurations rely on public STUN servers operated by third parties. These servers log IP addresses and connection times, creating opportunities for traffic analysis and user correlation. Self-hosting these services eliminates external dependencies but requires additional infrastructure.
UPnP Attack Surface
Automatic port forwarding through UPnP exposes devices to internet attacks if router security fails. Many UPnP implementations contain vulnerabilities that allow remote exploitation. Manual port forwarding provides better security control at the cost of configuration complexity.
Discovery Server Surveillance
Global discovery indexes device announcements (Device ID, addresses); peer relationships aren’t explicitly recorded. While encrypted, this metadata enables analysis of user networks and synchronization patterns. Local discovery through LAN broadcasting avoids this issue but limits connectivity options.
Deployment Considerations
Enterprise deployment requires addressing compliance and audit requirements while maintaining the security benefits of decentralized architecture. Centralized logging and monitoring can be implemented without compromising end-to-end encryption through local log aggregation and encrypted storage.
Backup integration presents unique challenges since traditional backup systems expect centralized file storage. Syncthing's distributed model requires backing up from multiple devices or implementing dedicated backup peers that receive all synchronized content.
Recommended OPSEC Configuration:
- Run your own discovery server to eliminate external metadata leakage
- Disable UPnP and configure manual port forwarding for better security control
- Use local network discovery when possible to avoid internet-based peer location
- Deploy dedicated backup devices that don't sync back to avoid creating additional attack surfaces
- Monitor synchronization logs for unexpected device connections or access patterns
- Implement network segmentation to isolate Syncthing traffic from other applications
Syncthing provides a viable alternative to surveillance-based file synchronization, but requires understanding its attack surfaces and implementing appropriate operational security measures. The elimination of corporate intermediaries significantly improves privacy, but shifts responsibility for security configuration to individual users and organizations.




