SimpleX Chat's X Account Hijacked for Crypto Scam
Hackers blocked the company founder from his own brand's account while promoting wallet-draining scam links.

The @SimpleXChat X account fell to attackers on December 6, 2025, becoming the latest high-profile casualty in a year defined by OAuth token exploitation and social media hijacking for crypto fraud.
I was made aware of this by Triple Max ( https://x.com/Yashraj__ ) when he tagged me.
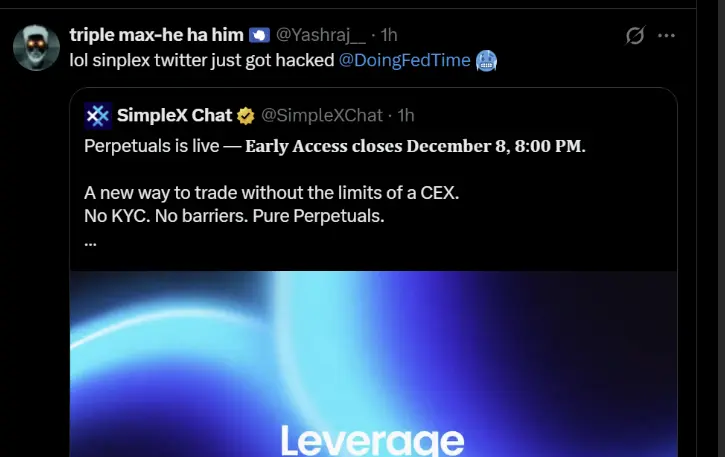
At 21:27 GMT, the compromised account posted a promotional message for "Perpetuals," described as a no-KYC decentralized trading platform for perpetual futures. The attackers pinned the post to the profile, included a 14-second video showcasing supposed AI-powered trading features, and linked to simplexspot.com a domain designed to look affiliated with SimpleX Chat but completely unrelated to the legitimate privacy messenger.
Nine minutes later, Evgeny Poberezkin, founder of SimpleX Chat, posted from his personal account: ".@SimpleXChat account access is compromised!!! The last post is not ours." In a follow-up, he identified the attack vector as "a scam via some delegate account compromise" and shared screenshots showing the scam post pinned to the profile. The attackers had blocked Poberezkin from the @SimpleXChat account entirely, a calculated move to buy themselves time before anyone with authority could intervene.
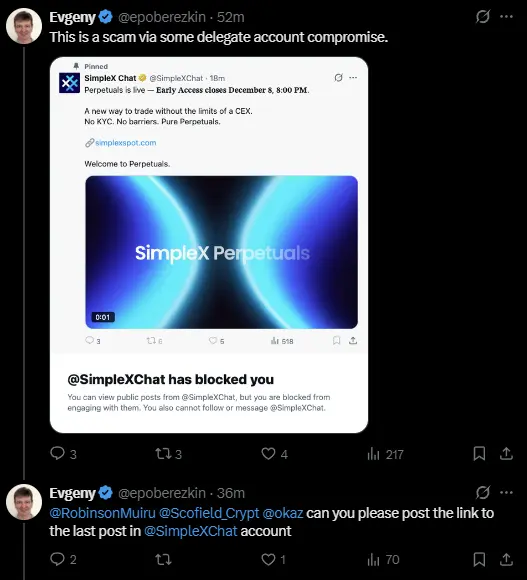
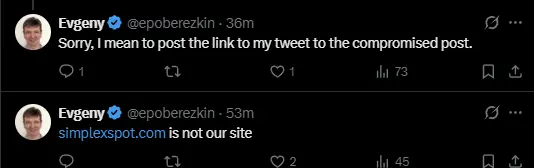
Community members started flagging the scam within half an hour. User Michael Scofield (@Scofield_Crypt) replied directly to the fraudulent post calling it out as a hack, while others quoted Poberezkin's warning to amplify the alert. But the attackers had anticipated resistance: bot accounts flooded the replies with testimonials like "Just tested it everything works smoothly" and "Verified. It works," lending artificial credibility to the scam in the critical early minutes when real users might be deciding whether to click.
The scam site itself represents a classic misdirection move. Simplexspot.com presents itself as a "perpetual communication network" connected to SimpleX Chat, mixing legitimate-sounding privacy language with crypto incentives. Visitors see promises of decentralization, data ownership, and "Community Vouchers" for funding servers all wrapped around invitations to connect crypto wallets and download desktop applications. The bait-and-switch blends messaging app aesthetics with DeFi trading hooks, designed to confuse users about what they're signing up for.
This confusion serves the attackers' purpose. Once a victim connects a wallet to a malicious site, the site can request approval for smart contracts that drain funds. The "no-KYC perpetuals trading" angle appeals to the demographic most likely to follow a privacy-focused messaging app: people who value financial anonymity and might let their guard down when a trusted account promotes something that aligns with their values.
The attack method delegate account compromise exploits how X handles third-party application permissions. When users authorize apps to post on their behalf through OAuth tokens, those tokens often persist long after anyone remembers granting access. If an attacker compromises the third-party service, or obtains tokens through phishing, they can post as the account holder without ever knowing the password. OAuth tokens can survive password changes and remain valid until manually revoked, making them ideal persistence mechanisms for attackers.
SimpleX Chat joins a growing list of 2025 victims. BBC broadcaster Nick Robinson's account was hijacked in February to promote a fake Solana cryptocurrency. Kylian Mbappé's account was compromised in August 2024 to push a fraudulent memecoin that briefly hit $460 million market cap before collapsing. The X account of deceased antivirus founder John McAfee was reactivated in January to hawk yet another scam token. SentinelOne documented an active phishing campaign targeting U.S. political figures, international journalists, and cryptocurrency organizations specifically for account takeover.
The August 2025 Salesloft breach demonstrated just how catastrophic OAuth token theft can become. Attackers who infiltrated Salesloft's systems obtained tokens affecting multiple major security companies, including Cloudflare, Palo Alto Networks, ZScaler, and Proofpoint. When your OAuth infrastructure becomes a single point of failure, a compromise anywhere in the chain ripples outward.
What makes the SimpleX incident particularly ironic is the messenger's entire design philosophy. SimpleX Chat operates without user identifiers of any kind no phone numbers, usernames, random IDs. In short it's an impressive app.
The protocol achieves metadata protection through unidirectional message queues, meaning even relay server operators see nothing useful. Trail of Bits audited the system in both 2022 and 2024. No evidence suggests the SimpleX Chat messaging application was affected.
But social media accounts run on different infrastructure with different trust assumptions. The same person that engineered a messenger resistant to server compromise chose to maintain a presence on a platform where a single leaked OAuth token can hand over the keys. That tension between building private-by-design systems and participating in surveillance-economy platforms to reach users defines modern privacy tech.
For anyone who saw the scam post before Poberezkin's warning: assume simplexspot.com captured any data you entered and revoke any wallet permissions you granted. If you downloaded software from the fake site, treat your device as compromised and scan accordingly. The scam video's promises of "55% Earn Free" and AI-powered trading were fabrications designed to create urgency and bypass skepticism.
The SimpleX team's nine-minute response time from compromise to public warning represents effective incident response. Whether they've regained full control of the account remains unclear. Monitoring Poberezkin's personal account or the official simplex.chat website for updates makes more sense than trusting anything from @SimpleXChat until the situation resolves.
Considering he is the only employee.
Every connected third-party app on your X account represents an attack surface. The Twitter OAuth feature that enables convenience also enables abuse. Reviewing and revoking unused app permissions should be routine maintenance, not something you think about only after watching someone else get burned. The more doors you leave open, the easier attackers can walk through one.




