Qubes OS Dodges Three Xen Security Flaws
The Xen Project dropped three security advisories on September 9, 2025, and Qubes OS published same-day confirmation that none of them threaten the platform's security architecture.

On September 9, 2025, the Xen Project released three security advisories: XSA-472, XSA-473, and XSA-474. Six CVE identifiers covering vulnerabilities from denial-of-service to potential privilege escalation. Within hours, Qubes OS published confirmation that none of these flaws affect Qubes installations. No patches, no updates, no action required.
This outcome stems from architectural decisions made years before these vulnerabilities existed. Qubes OS runs on the Xen hypervisor, but it doesn't enable every Xen feature. The project's security-by-isolation model needs strong VM separation and lightweight management, not enterprise pooling or Windows performance optimization. By running only essential Xen components, Qubes dodges entire vulnerability classes that plague full-featured deployments.
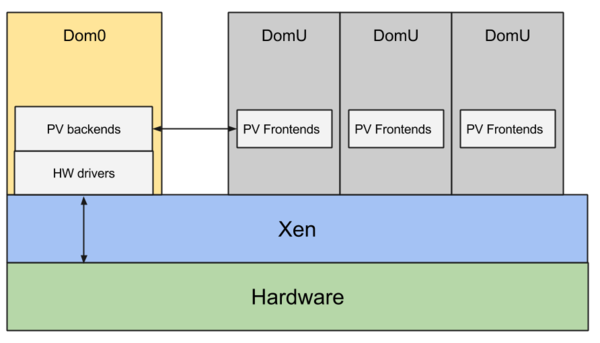
XSA-472 targets Viridian extensions with three CVEs (CVE-2025-27466, CVE-2025-58142, CVE-2025-58143). Viridian is Microsoft's codename for Hyper-V enlightenments—paravirtualization interfaces that tell Windows guests they're virtualized and optimize performance accordingly. The vulnerabilities involve NULL pointer dereferences and race conditions in how Xen handles guest memory pages. Attackers could crash the host, leak information, or escalate privileges. Only x86 HVM guests with reference_tsc or stimer extensions enabled are vulnerable, and Windows VMs typically enable these by default for performance gains. Roger Pau Monné of XenServer discovered the bugs, and patches exist for Xen versions unstable through 4.17.x.
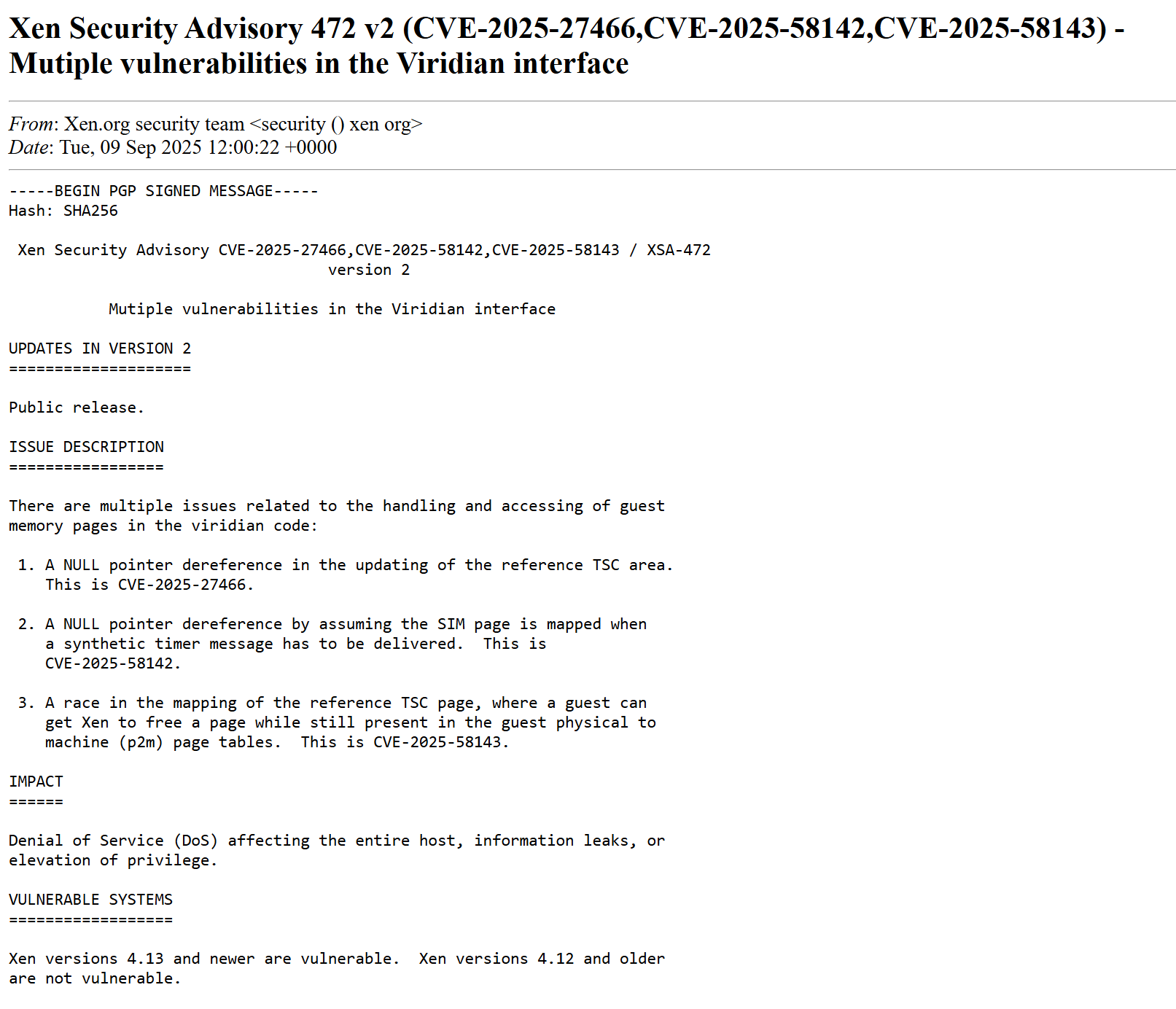
Qubes config files include Viridian settings, but a libvirt bug prevents them from activating. Libvirt converts the XML config to xl format and appears to respect Viridian during conversion, but ignores the setting when creating VMs. Advanced users can verify with sudo xl list -l <NAME_OF_HVM> in dom0. The extensions stay disabled despite what config files suggest. Whether by design or accident, XSA-472 can't exploit code that never runs.
XSA-473 affects ARM page reference counting (CVE-2025-58144, CVE-2025-58145). Qubes runs exclusively on x86-64 hardware. The architecture docs specify x86-64 processors, and ARM support would require rewriting dom0 initialization, driver integration, and hardware compatibility layers. The x86-64 ecosystem provides mature virtualization extensions like Intel VT-x and AMD-V. ARM vulnerabilities don't threaten x86 systems.
XSA-474 exposes denial-of-service bugs in XAPI's UTF-8 string handling (CVE-2025-58146). XAPI is the Xen Project management API—an enterprise toolstack providing domain lifecycle management, pool awareness across multiple hosts, and advanced storage features for XenServer and XCP-ng datacenters. The vulnerability stems from mismatched Unicode specification versions and missing input sanitization. Malicious inputs from authenticated users or privileged guest code can crash the host. XCP-ng patched it by updating Xen to 4.17.5-15.3.
Qubes doesn't use XAPI. The project uses libxl, a small, stateless C library providing basic VM management through the xl command-line tool. XAPI maintains state across databases and manages multiple hosts. libxl stays lightweight and stateless, delegating state management to clients. This makes libxl simpler and immune to XAPI's database and string-handling bugs. XSA-474's vulnerable code never executes in Qubes.
The pattern matters more than individual bugs. When the Xen Project issues a Xen Security Advisory, not every deployment faces the same risk. Different configurations enable different features. ARM bugs don't affect x86 systems. Enterprise management API flaws don't touch systems using different toolstacks. Qubes maintains a comprehensive XSA tracker documenting every publicly disclosed XSA and whether it affects Qubes security.
When XSAs drop, Qubes publishes same-day notices explaining which ones matter and which don't. When vulnerabilities do affect Qubes, the project issues Qubes Security Bulletins with patches. When they don't apply, users get explicit confirmation with technical explanations of why. Security-conscious users make decisions based on understanding, not authority. "Here's the vulnerable component, here's what we use instead, here's how to verify it" beats "trust us, you're safe."
The architectural choices that neutralized these XSAs predate the vulnerabilities. Qubes chose libxl years ago because stateless VM management aligned with security-by-isolation. Qubes never pursued ARM because x86-64 met requirements. Viridian stays disabled through a libvirt bug, but users could manually disable it anyway if they prioritize security over Windows VM performance.
Defense in depth means eliminating unnecessary complexity and reducing trusted code. Every enabled feature runs with elevated privileges. Every optional component adds attack surface. Qubes runs only Xen components required for VM isolation and dom0 management. Most Xen vulnerabilities affect code Qubes never executes. When the isolation boundary itself has flaws, Qubes faces real risk and patches quickly. When vulnerabilities hit unused components, the limited attack surface becomes structural advantage.
September 9, 2025 brought three XSAs and six CVEs. Qubes users need zero action—no patches, no restarts, no configuration changes. The vulnerable code never ran. The broader lesson: when evaluating security platforms, ask not "what features does it have" but "what unnecessary features can I avoid running." More features mean more code, more code means more bugs, and more bugs mean more vulnerabilities.
Xen will release more XSAs. Some will affect Qubes and get patched through QSBs. Others will target features Qubes doesn't enable or platforms Qubes doesn't support. The XSA tracker keeps documenting both because transparency about what doesn't affect you matters as much as warnings about what does. That's what good architecture looks like when it meets real-world security disclosures.




