Qubes OS 4.3: Faster Disposables, Better Device Control
The latest Qubes release eliminates disposable VM boot delays while introducing self-identity device assignment for hardware you actually control.
The Qubes team released version 4.3.0 on December 21, 2025, marking the first stable release after four release candidates that began in August. The update touches every layer of the security-focused operating system, from the Xen hypervisor running underneath to the templates users interact with daily.
The headline feature for daily users is preloaded disposables. Qubes has always offered disposable VMs temporary instances that vanish after use, leaving no trace of your browsing session or document editing. The problem was waiting for them to boot. Version 4.3 solves this by queuing unnamed disposables in the background, so when you need one, it appears instantly while another quietly preloads behind the scenes. You configure it through the Qubes Global Config or by running qvm-features dom0 preload-dispvm-max 2 from the command line. The workflow stays the same, but the friction disappears.
Under the hood, Xen 4.19 replaces the previous hypervisor version. The Xen Project released 4.19 in July 2024, billing it as a significant security milestone. This version incorporates fixes for 13 security advisories, advances MISRA-C compliance for safer code development, and no longer exposes pIRQ support to HVM guests by default a hardening measure that reduces attack surface. The hypervisor now scales to 16,383 CPUs, quadrupling the previous limit, though most Qubes users care more about the security patches than enterprise scalability.
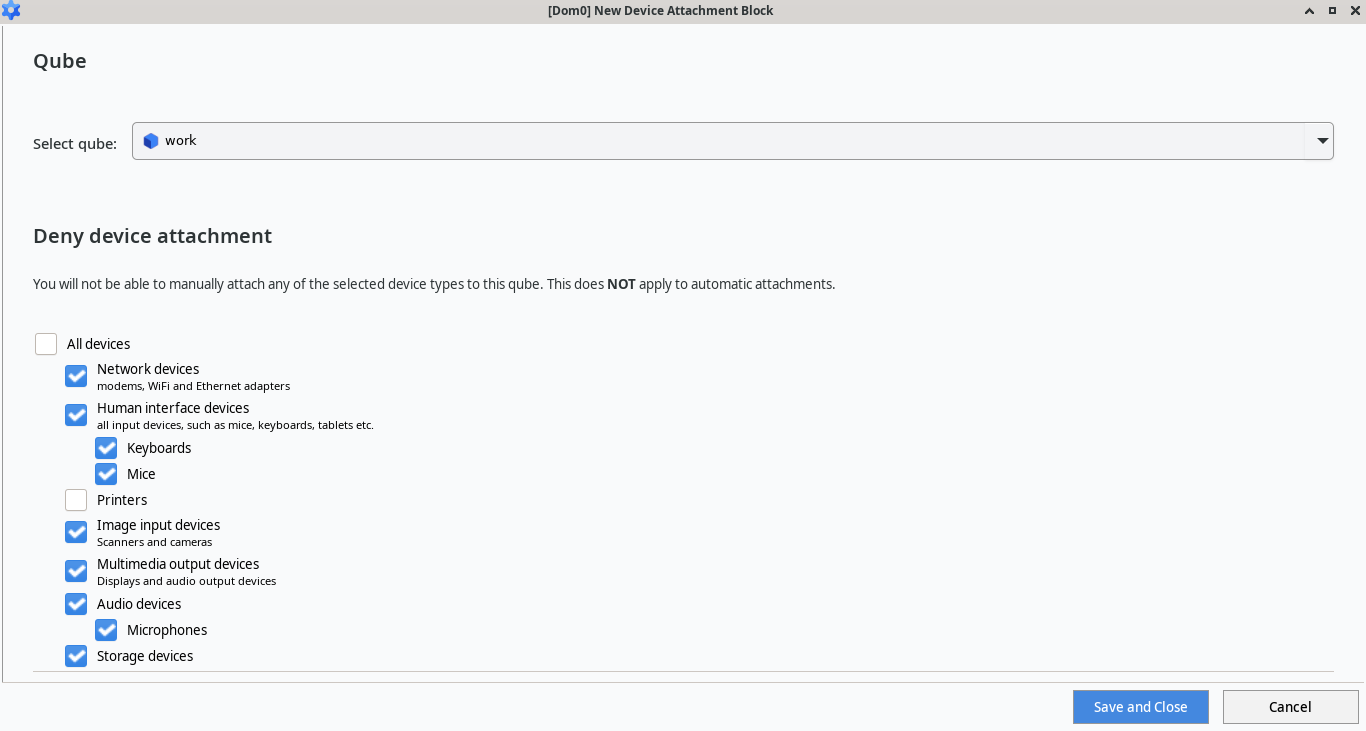
Device management gets a complete overhaul through the New Devices API. The previous system assigned devices by bus, slot, and function technical identifiers that could change when you plugged hardware into different ports or rebooted. The 4.3 approach uses "self-identity oriented" assignment, letting you attach devices based on what they are rather than where they happen to be connected. A redesigned Qubes Devices widget and dedicated Device Assignments page in Global Config make this usable for normal humans. You can also filter input devices with udev rules, blocking suspicious peripherals before they reach any qube.
The default templates jump to current releases: Fedora 42, Debian 13, and Whonix 18. Templates from Qubes 4.2 backups still work but may reference outdated repositories, requiring distribution upgrade commands to fix. Fresh installations and in-place upgrades handle this automatically. The administrative domain, Dom0, now runs Fedora 41 with an updated kernel and GRUB2 security patches.
Qubes Windows Tools return after a period of unavailability, now supporting Windows 11 in HVMs with improved file management between Windows qubes and the rest of your system. Windows 7 support gets dropped Microsoft ended extended support for it in January 2023, and maintaining compatibility with abandoned operating systems creates more security risk than convenience. If you need Windows in Qubes, you need a supported version.
Privacy-focused additions include kloak, a keystroke anonymization tool that defeats typing pattern fingerprinting. Every person types with a unique rhythm key press duration, intervals between characters, patterns in common words that can identify you across sessions even when other tracking fails. Kloak randomizes these timing patterns, though full system-wide protection requires installation in dom0 rather than individual VMs due to Qubes' virtualized input architecture. The release also prevents Whonix-Workstation applications from accidentally opening in non-Whonix disposables, closing a potential anonymity leak where Tor traffic could mix with clearnet activity.
Policy enforcement gains UUID-based addressing, and private repositories can now use SSL certificates for authentication. Custom kernel command-line parameters work in templates for users who need specific boot configurations. Performance improvements include direct volume access without snapshots, retired RPC multiplexing in favor of direct command execution, and qrexec policy evaluation caching.
Experimental features point toward the future. Initial Wayland session support in GUIVM signals eventual X11 replacement, though the implementation remains incomplete. Ansible support and Qubes Air compatibility expand automation and remote management possibilities for advanced deployments.
Users running Qubes 4.2 have three upgrade paths: fresh installation from the 4.3.0 ISO, in-place upgrade, or updating from release candidate versions. The Qubes team "strongly recommends making a full backup beforehand" standard advice that becomes critical when your entire digital life runs in isolated VMs. Qubes 4.2 continues receiving security updates and bug fixes until June 21, 2026, giving everyone six months to migrate.
The timing matters for anyone relying on Qubes for operational security. Running an unsupported version means missing patches for vulnerabilities that attackers specifically target in security-focused systems. When your threat model includes sophisticated adversaries, falling behind on updates undermines the entire point of compartmentalization. Version 4.3 brings enough improvements to justify the migration effort, and the support deadline provides a clear window to plan the transition.




