
carding
Godman666 at Defcon 33: Carding, Sabotage & Survival: A Darknet Market Veteran’s Story
For over 10 years, he's operated at every level of darknet markets - from carding forums to multi-million dollar platforms.

carding
For over 10 years, he's operated at every level of darknet markets - from carding forums to multi-million dollar platforms.
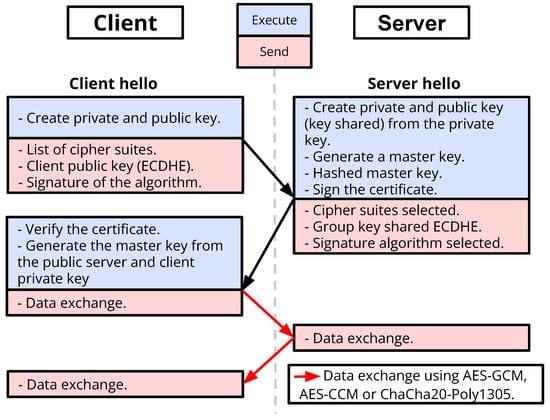
ChaCha20
ChaCha20-Poly1305 AEAD combines stream cipher encryption with universal hash authentication, delivering 2-4x performance over AES-GCM on mobile processors while resisting timing attacks through constant-time implementation.
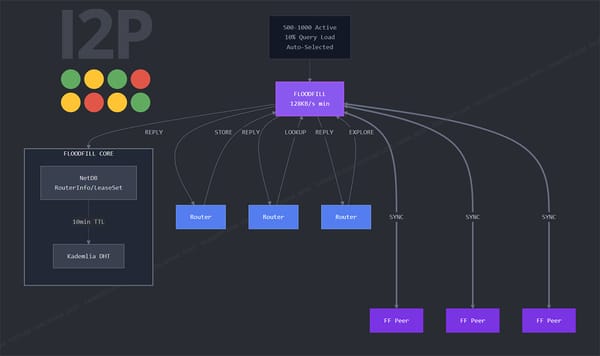
I2P
I2P floodfill routers implement distributed hash table protocols adapted for anonymous networking, handling 20-40% hourly churn rates while maintaining network database consistency and peer discovery.

Monero
Bulletproofs+ delivers logarithmic proof sizes and 40% verification speedups in Monero RingCT through mathematical optimizations that reduce bandwidth and improve transaction processing performance.

IPFS
IPFS mesh networking creates peer-to-peer content distribution where cryptographic hashes replace server locations, enabling decentralized data storage and retrieval without centralized infrastructure dependencies.
Darknet-Markets
Darknet market escrow uses multisig cryptocurrency addresses and automated timers but remains vulnerable to administrator exit scams.

PGP
PGP key generation, distribution, and storage failures create retroactive vulnerabilities that compromise entire communication histories.

VPN
VPN kill switches fail during timing windows while DNS leaks occur through multiple system-level bypass mechanisms.

Bitcoin-Mixers
ChipMixer, Tornado Cash, and Samourai Wallet failures show that Bitcoin mixing services create surveillance databases and legal liability.

Threat-Models
Effective threat models assess specific adversary capabilities and attack surfaces rather than implementing random security measures.

I2P
I2P's garlic routing provides superior anonymity through bidirectional tunnels and distributed architecture without central authorities.

npm malware
The package literally advertised itself as an 'enhanced stealth wallet drainer' in its own source code, and npm still served it up for days.