Omerta Market Lasted 15 Days Before IP Leak Exposure
A darknet market that claimed two years of development leaked its server IP within approximately two weeks of launch.

Omerta Market launched on November 21, 2025 at 22:15 UTC with a manifesto promising "stability over hype, security over flash." Approximately two weeks later, the market went dark after security researcher valor98 publicly exposed its real server IP address the kind of operational security failure that hands law enforcement everything they need to seize infrastructure and arrest operators.

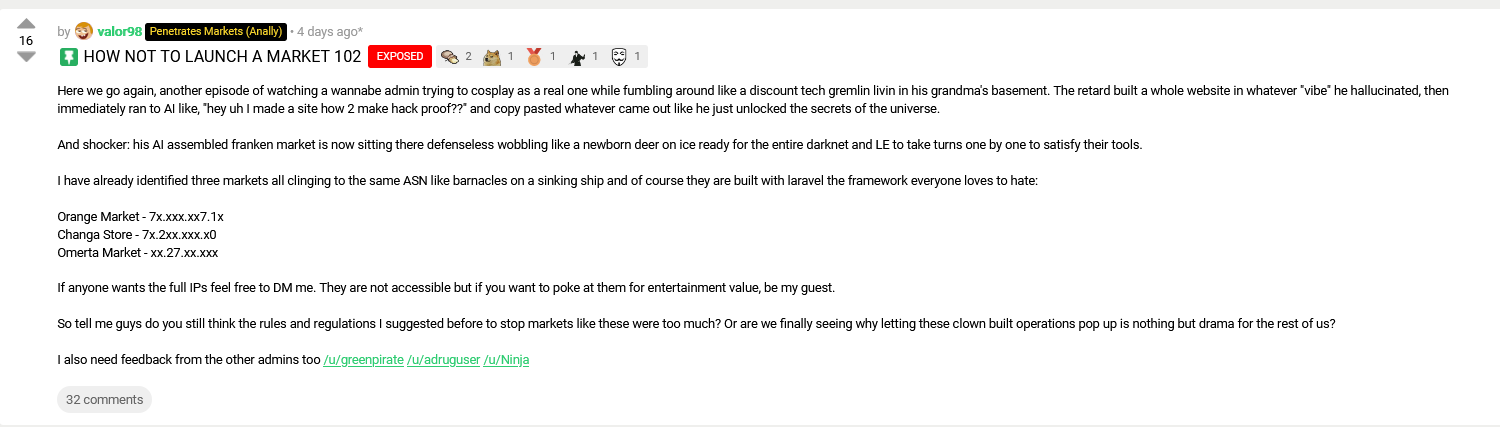
The exposure came via a post titled "HOW NOT TO LAUNCH A MARKET 102 EXPOSED" on darknet forums. valor98 documented three markets all sitting on the same ASN (Autonomous System Number, meaning the same network provider): Omerta Market, Orange Market, and Changa Store. The clustering pattern suggested amateur operators possibly using similar hosting arrangements or shared infrastructure.
valor98's assessment landed with the subtlety of a sledgehammer: "another episode of watching a wannabe admin trying to cosplay as a real one while fumbling around like a discount tech gremlin living in his grandma's basement. The retard built a whole website in whatever 'vibe' he hallucinated, then immediately ran to AI like, 'hey uh I made a site how 2 make hack proof??' and copy pasted whatever came out like he just unlocked the secrets of the universe."
The term "vibe coded" describes a growing phenomenon where people use AI language models to generate application code without understanding the underlying architecture or security implications. When your codebase consists of copy-pasted ChatGPT outputs assembled by someone who asks "how 2 make hack proof" after building the site, the results tend toward the catastrophic. Omerta's IP leak represents what happens when operators treat security as an afterthought whether through AI-generated advice or simple incompetence.
Community researcher Scarab provided additional technical analysis, noting that Orange Market (one of the other exposed sites on the same ASN) actually ran Flask or Django with jinja2 templating and a gunicorn server rather than Laravel as initially claimed. The /static/ directory structure and server signatures gave it away. These details matter because they reveal operators who fundamentally misunderstand their own infrastructure people running code they can barely identify, let alone secure.
Scarab also identified a more damning pattern, alleging "they stole a lot of features from /d/BlackOps and /d/PrimeMarket and /d/MarsMarket and /d/DarkMatterMarket without even giving any of these marketplaces credits of inspiration or anything." The combination of allegedly copied features, AI-assisted code, and shared hosting that leaked IPs created architecture vulnerable to exactly this kind of exposure.
The contrast between Omerta's launch announcement and the reality of their security posture borders on comedy. Their November 21 post claimed "two years of development" and promised features including automatic withdrawals at custom thresholds, batch order management, a casino system with lottery and battleships games, auto-response templates, and a $5,000 giveaway scheduled for January 1, 2026. They emphasized that their codebase was built entirely in-house: "We don't rely on prebuilt codebases or external dependencies, what runs Omertà is ours, from infrastructure to interface."
Approximately two weeks of operation proved otherwise. When your "in-house infrastructure" leaks the server IP to anyone looking, the grandiose feature list becomes irrelevant. All those casino games and withdrawal automation features mean nothing when law enforcement can trace requests back to your physical server location.
Omerta's response to getting burned demonstrates the special kind of delusion that amateur operators bring to the space. After valor98's exposure, the market reached out via their /u/OmertaPR account: "We have messaged /u/valor98 from /u/OmertaPR as our inbox limit was reached. We would obviously like to resolve this, move servers and work with /u/valor98 on a paid basis for a full on test so this doesn't happen again."
valor98 shared this message with the community, adding: "I got business guys!!!!!"
Other community members highlighted the absurdity of the offer. User Paracelcus responded: "What were you going to do if it was the police who found your IP? Just bribe them and move to a new server to keep going? Work with them on a paid basis so this doesn't happen again?"
The question cuts to the core of the issue. Paying for a penetration test after your IP leaks resembles buying a fire extinguisher after your house burns down. The operational security failure already happened. Any competent adversary law enforcement, competitors, or researchers now possesses the information needed to identify hosting providers, trace financial flows, and potentially identify operators. Moving servers changes nothing about the historical exposure.
Forum moderator greenpirate weighed in on the systemic problem these launches represent: "i believe also that without approval this subdread will get lots of action and comedy and will grow faster, otherwise it gets a bit boring here. also i believe that when markets get burned hard that market admins will think twice before launching because they have only one chance and they are in front of some clever people who by sure will have a look at it."
The community enforcement model works precisely because 3,000+ subscribers with technical knowledge can identify the tells of amateur operations: shared ASNs, vibe-coded interfaces, plagiarized features, and the distinctive smell of operators who built their security model by asking AI how to make things "hack proof." When a market launches without proper operational security, the community burns it fast enough that users can avoid depositing funds into systems destined for seizure or exit scam.
Scarab delivered the consensus verdict: "Your marketplace is fucked. It is better to just reskin your existing marketplace and launch a new one, you guys are new anyway, so just launch under a new name."
The Omerta brand now carries the stigma of incompetence. Any continued operation under that name signals to the community that the operators either missed the lesson or remain too stubborn to acknowledge the failure. Even other markets with questionable histories maintain enough credibility to keep operating; Omerta managed to destroy theirs in approximately two weeks flat.
For users who interacted with Omerta Market during its brief existence, the IP exposure means your activity occurred on a deanonymized server. Whether law enforcement obtained that IP before or after the public disclosure remains unknown, but the possibility exists that transaction logs and communication records tied to a real server location are now in someone's hands. Rotating credentials, evaluating cryptocurrency trail exposure, and assuming the worst represents the appropriate response.
The broader lesson extends beyond one failed market. AI-assisted development without security expertise produces code that works until someone actually tests it against adversarial conditions. The darknet market space attracts operators who see the potential revenue without understanding the operational security requirements that keep them alive. Approximately two weeks of operation before IP exposure suggests Omerta never had proper security they just lacked anyone motivated to look until valor98 decided to check.
The next vibe-coded market is already being built somewhere. Whether it lasts three weeks or three months depends entirely on how quickly someone competent decides to poke at it.




