Nextcloud Talk Deployment: TURN/STUN Configuration and Self-Hosted Video Calling
Nextcloud Talk deployment enables enterprise-grade self-hosted video calling through sophisticated WebRTC implementation, TURN/STUN server configuration, and privacy-preserving communication.

Nextcloud Talk deployment enables enterprise-grade self-hosted video calling through sophisticated WebRTC implementation, TURN/STUN server configuration, and privacy-preserving communication infrastructure that provides complete control over organizational communications while maintaining professional quality and security standards.
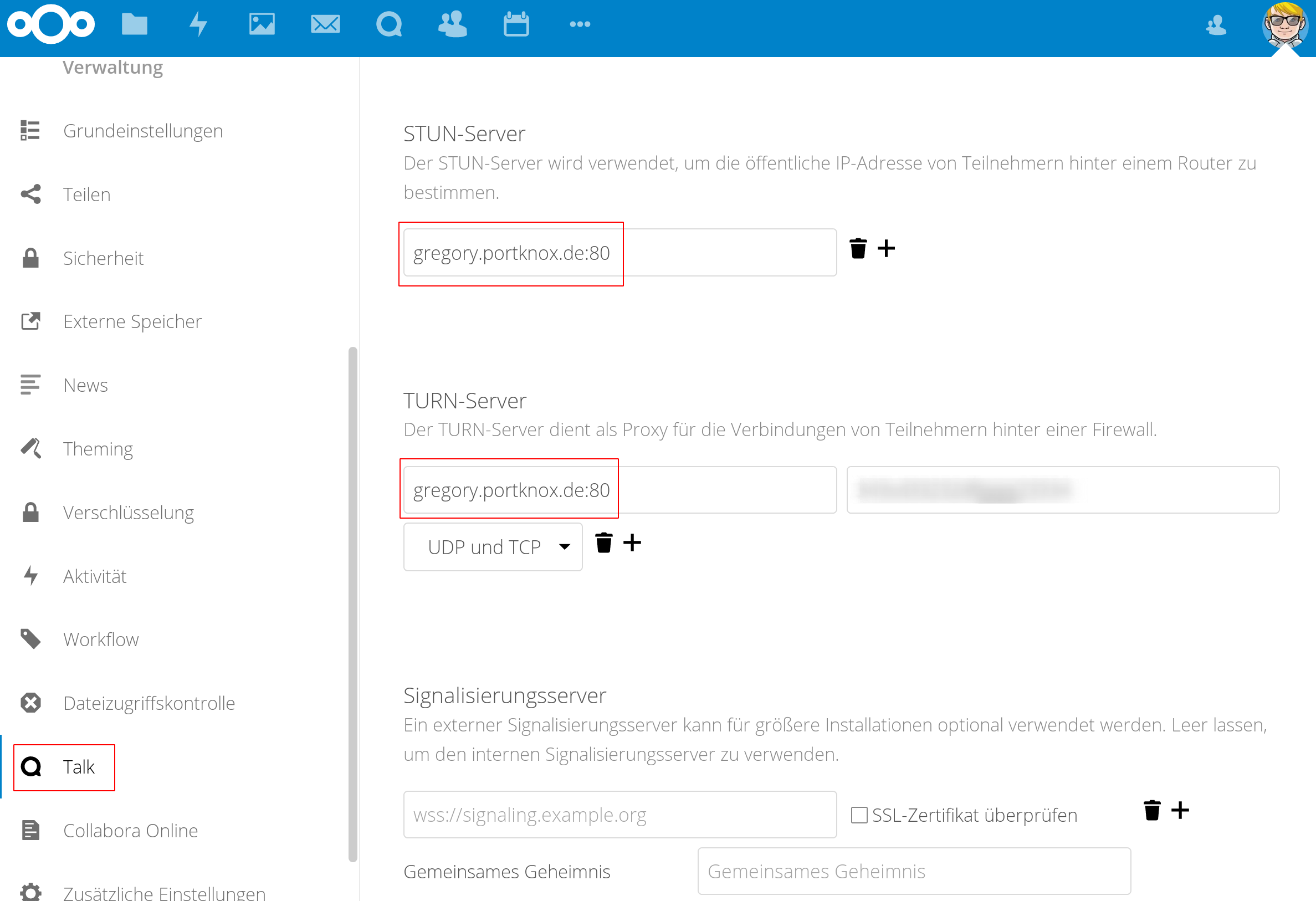
Nextcloud Talk documentation demonstrates how proper Talk deployment combines NAT traversal optimization, bandwidth management, and end-to-end encryption to create secure video conferencing solutions that protect privacy while delivering reliable real-time communication across diverse network environments and organizational requirements.
WebRTC Protocol Architecture and NAT Traversal Foundation
WebRTC specifications provides WebRTC specifications showing how peer-to-peer communication protocols enable direct browser-to-browser connectivity through sophisticated signaling, media negotiation, and connection establishment procedures. WebRTC architecture includes Session Description Protocol negotiation, Interactive Connectivity Establishment, and Datagram Transport Layer Security that create secure real-time communication channels while addressing network topology challenges and firewall traversal requirements.
NAT traversal mechanisms address network connectivity challenges through STUN and TURN protocols that enable WebRTC connections across firewalls, NAT devices, and complex network topologies. NAT traversal techniques analyzes NAT traversal techniques showing how ICE candidate gathering, connectivity checking, and relay mechanisms ensure reliable connection establishment while optimizing for direct peer-to-peer communication when possible and fallback relay when necessary.
Connection establishment implements sophisticated negotiation procedures that test multiple connectivity options including direct connections, STUN-assisted connections, and TURN relay connections to identify optimal communication paths. Connection optimization includes candidate prioritization, connectivity testing, and bandwidth assessment that ensure reliable communication establishment while minimizing latency and resource consumption for optimal user experience.
Media stream management handles audio and video transmission through codec negotiation, quality adaptation, and error recovery mechanisms that maintain communication quality despite network variations and bandwidth constraints. Stream management includes adaptive bitrate control, codec selection, and error concealment that optimize media quality while ensuring communication continuity across diverse network conditions and device capabilities.
TURN/STUN Server Configuration and Infrastructure Deployment
Coturn server documentation documents Coturn server implementation showing how TURN/STUN server deployment provides essential NAT traversal infrastructure through relay services, authentication management, and bandwidth optimization. Coturn configuration includes authentication mechanisms, network interface management, and resource allocation that enable reliable WebRTC connectivity while protecting against abuse and ensuring service availability for legitimate users.
Authentication and security implementation protect TURN/STUN services through credential management, access controls, and abuse prevention mechanisms that ensure service availability while preventing unauthorized usage. Security measures include shared secret authentication, time-limited credentials, and rate limiting that balance service accessibility against resource protection while maintaining compatibility with WebRTC client requirements.
- Time-limited credentials enable WebRTC client access without long-term secret storage
- REST API generates ephemeral credentials dynamically per session
- Credentials safe to embed in JavaScript without permanent compromise risk
- Compatible with standard TURN protocol and WebRTC client libraries
- Rate limiting prevents brute force authentication attempts and allocation flooding
- Bandwidth caps protect server capacity from relay traffic abuse
- Allocation timeouts and refresh requirements prevent resource starvation
- Credential expiration limits window for compromised credential misuse
Network configuration addresses firewall rules, port management, and traffic routing requirements that enable TURN/STUN server operation while maintaining network security and performance. Network setup includes UDP/TCP port configuration, firewall exception management, and traffic prioritization that optimize real-time communication while maintaining security boundaries and network performance for other services.
High availability and load balancing implement redundant TURN/STUN infrastructure through multiple server deployment, health monitoring, and traffic distribution that ensure service continuity despite hardware failures or maintenance requirements. Availability includes server clustering, health checking, and automatic failover that maintain communication capability while supporting scalable deployment across geographically distributed infrastructure.
Nextcloud Talk Integration and Performance Optimization
Talk application configuration integrates TURN/STUN servers through proper credential management, server selection, and connectivity optimization that enable reliable video calling within Nextcloud environments. Integration includes server endpoint configuration, authentication setup, and connection testing that ensure Talk applications can successfully establish WebRTC connections across diverse network environments and user scenarios.
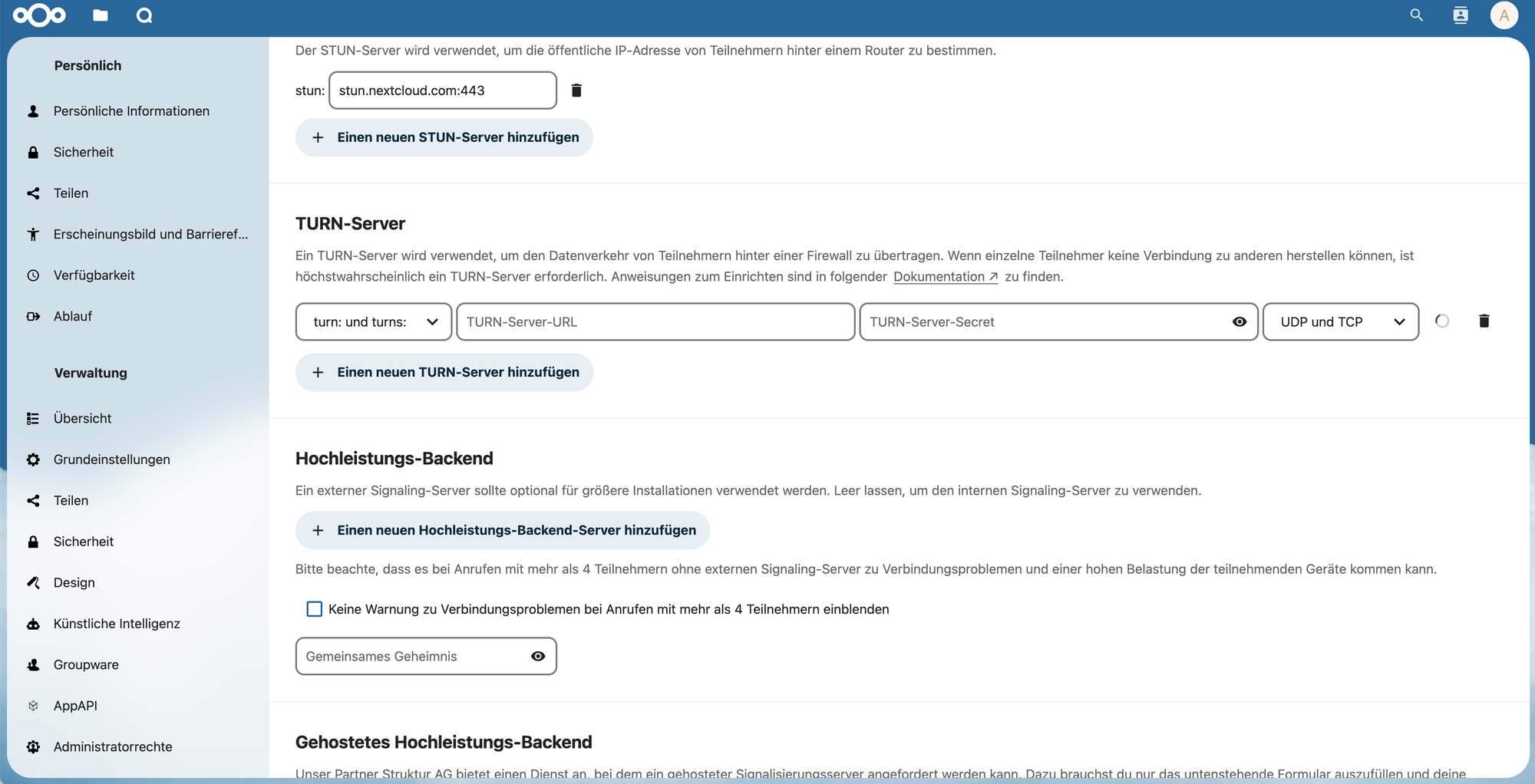
WebRTC optimization provides WebRTC optimization guidance showing how codec selection, bandwidth management, and quality adaptation enhance communication quality while managing resource consumption and network utilization. Optimization includes audio/video codec configuration, bitrate adaptation, and quality scaling that balance communication quality against bandwidth constraints while ensuring optimal user experience across diverse device and network conditions.
Performance tuning addresses server resource utilization, database optimization, and caching strategies that enable scalable Talk deployment supporting hundreds of concurrent users and multiple simultaneous video conferences. Performance optimization includes PHP configuration, database indexing, and reverse proxy optimization that ensure responsive Talk operation while maintaining system stability and resource efficiency.
Cross-platform compatibility ensures consistent Talk functionality across desktop browsers, mobile applications, and diverse operating systems through configuration optimization and feature management. Compatibility includes browser-specific optimization, mobile client configuration, and feature detection that provide reliable communication capability while adapting to device limitations and platform-specific requirements.
Security Implementation and Privacy Protection
Privacy engineering analyzes privacy engineering principles showing how self-hosted communication protects user privacy through data localization, access controls, and minimal data collection that ensure organizational control over sensitive communications. Privacy implementation includes data residency compliance, access logging, and retention policies that protect user privacy while meeting organizational requirements and regulatory obligations.
End-to-end encryption provides communication confidentiality through WebRTC's built-in DTLS encryption combined with additional application-layer protection that ensures message privacy even from infrastructure administrators. Encryption includes key management, session security, and metadata protection that create comprehensive privacy protection while maintaining functionality for features including screen sharing and file transmission.
Network security implements comprehensive protection through SSL/TLS encryption, access controls, and intrusion detection that protect Talk infrastructure against various attacks while maintaining service availability. Security measures include certificate management, access restriction, and security monitoring that protect against unauthorized access while ensuring legitimate users can access communication services reliably.
Compliance and data protection address regulatory requirements through audit logging, data retention policies, and privacy controls that ensure Talk deployment meets organizational and legal requirements. Compliance includes GDPR compliance, audit trail generation, and data subject rights that ensure privacy regulation compliance while maintaining operational functionality and user experience.
Enterprise Deployment and Operational Management
Enterprise deployment provides enterprise deployment guidance showing how Talk integration with organizational infrastructure requires identity management, resource planning, and operational procedures that ensure reliable service delivery. Enterprise deployment includes LDAP integration, capacity planning, and backup procedures that enable professional communication services while maintaining security and operational requirements.
Monitoring and maintenance implement comprehensive system oversight through performance monitoring, log analysis, and health checking that ensure ongoing Talk service reliability and performance. Monitoring includes resource utilization tracking, error detection, and performance analysis that enable proactive maintenance while supporting troubleshooting and capacity planning for growing communication demands.
Real-time communication analyzes real-time communication requirements showing how Talk deployment must address latency optimization, bandwidth management, and quality assurance through systematic performance optimization and network engineering. Communication optimization includes traffic prioritization, network path optimization, and quality monitoring that ensure professional-grade communication quality while managing resource consumption and infrastructure costs.
Operational procedures enable systematic Talk management through automated deployment, configuration management, and incident response that ensure reliable service operation while minimizing administrative overhead. Operations include infrastructure automation, configuration version control, and standardized procedures that support scalable Talk deployment while maintaining security and performance standards across diverse organizational environments.




