Building Anti-Surveillance Infrastructure: Brave's Technical Evolution
Brave Browser handles 94 million users monthly with zero dependency on Google or Microsoft servers, and Big Tech should be terrified of what this proves.

Brave Browser launched in 2016 with a simple promise: block ads and trackers by default. Eight years later, it delivers something far more dangerous to surveillance capitalism, a complete alternative to Big Tech's data extraction infrastructure.
The numbers expose why Google and Microsoft should be nervous.
Brave now serves 94 million monthly users with zero dependency on their search indexes, zero reliance on their ad networks, and zero tolerance for their tracking schemes. Most browsers still route through Google or Microsoft servers. Brave routes around them entirely.
The Core Infrastructure: Shields
Brave Shields operate at the network request level within Chromium's multi-process architecture, intercepting resource loading before HTTP connections get established. The filtering engine consumes blocklists from EasyList, EasyPrivacy, uBlock Origin, and Brave's own crowdsourced filters, then compiles these rules into optimized data structures that can evaluate thousands of URL patterns in microseconds.
The technical implementation matters because timing determines effectiveness. Chrome extensions receive network requests after the browser has already initiated TCP connections and DNS lookups. Even when extensions block responses, the initial handshake reveals your IP address to tracking servers and logs the attempted connection in their access logs. Brave's integrated blocking kills requests at Chromium's network service layer, tracking domains never see connection attempts because the browser aborts them before socket creation.
Request classification happens through multi-stage filtering that examines URL patterns, HTTP headers, and DOM context simultaneously. A single tracking pixel might match multiple filter rules: its domain appears in tracking lists, its URL contains fingerprinting parameters, and its placement suggests cross-site data collection. Brave's engine combines these signals to make blocking decisions that individual filter rules might miss.
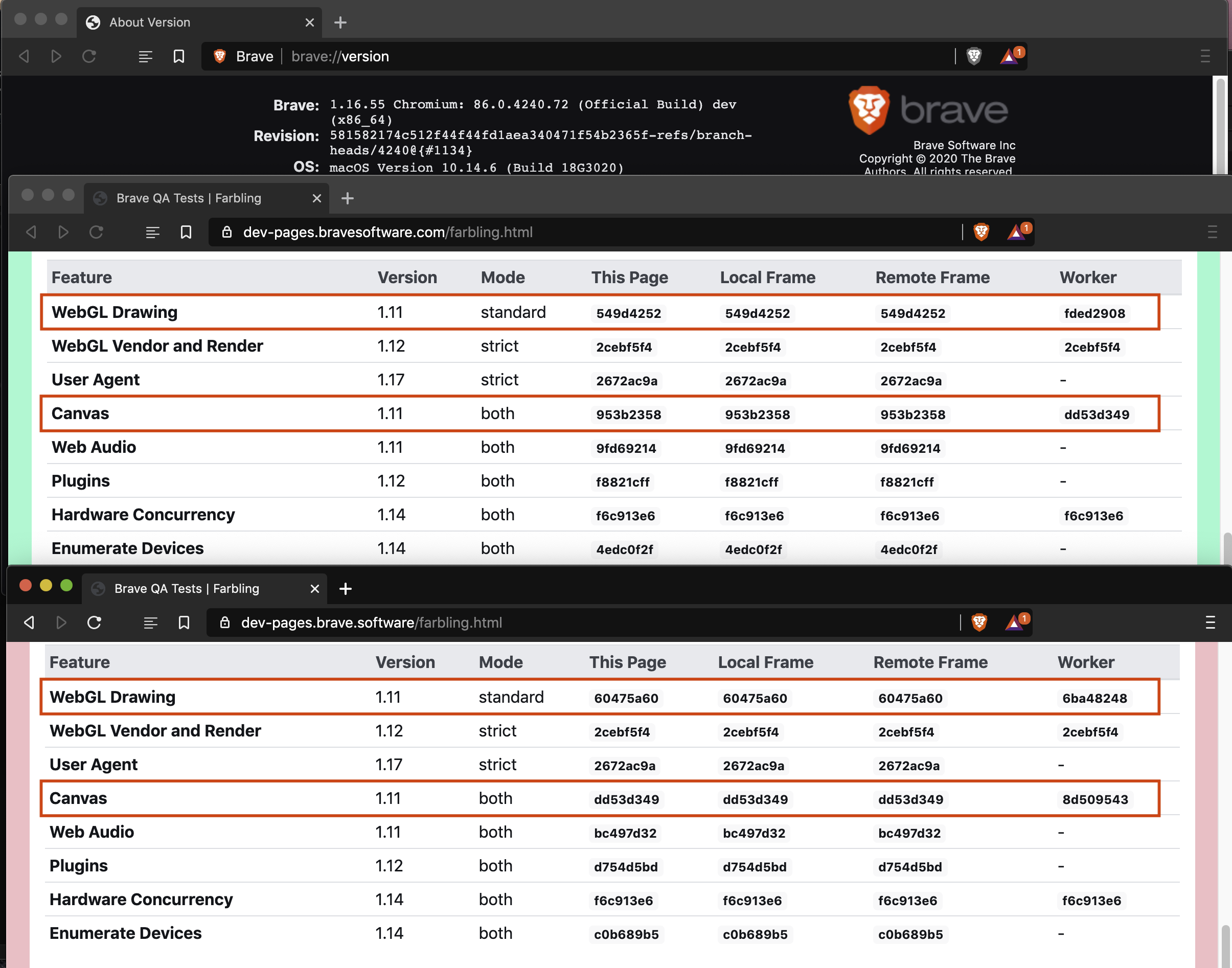
Fingerprinting protection uses "farbling", controlled randomization of browser APIs that websites probe for device identification. The algorithm doesn't return random values that would break sites, but instead applies mathematically consistent perturbations based on your session and the requesting domain. Your screen resolution might appear as 1919x1079 instead of 1920x1080, but the same site will always see the same fake value within a single session.
Canvas fingerprinting gets defeated through pixel-level noise injection that corrupts the unique signatures tracking scripts try to extract. When websites render text or graphics to hidden HTML5 canvas elements and read back pixel data, Brave adds imperceptible color variations that change the resulting hash. The visual appearance remains identical, but the cryptographic fingerprint becomes useless for tracking.
Audio context fingerprinting faces similar disruption through controlled modifications to Web Audio API responses. Tracking scripts synthesize audio signals and analyze the output to detect differences in hardware audio processing that can identify specific devices. Brave introduces subtle timing variations and amplitude adjustments that preserve audio functionality while poisoning the fingerprinting data.
WebGL fingerprinting attempts get blocked through graphics driver information spoofing. GPU vendor strings, supported extensions, and renderer capabilities all contribute to unique device signatures. Brave returns generic values for these parameters while maintaining compatibility with legitimate WebGL applications that need basic graphics capabilities.
The shield system scales efficiently because rule evaluation happens in compiled C++ code rather than interpreted JavaScript. Browser extensions that attempt similar blocking must parse filter rules and evaluate URL patterns in slower scripting environments. Brave's native implementation processes requests at near-CPU speeds while extensions introduce milliseconds of latency per decision.
Storage partitioning integration ensures that any tracking data that slips through network-level blocks can't persist across browsing sessions. Even if a tracker manages to set cookies or store data in localStorage, that information gets isolated to specific domain contexts and cleared according to Brave's ephemeral storage policies. Network blocking and storage isolation work together to eliminate both active tracking and passive data accumulation.
Debounce and Unlinkable Bouncing
Traditional privacy tools miss bounce tracking because it exploits the fundamental way browsers handle navigation between websites. Instead of blocking cookies or scripts after pages load, bounce tracking hijacks the clicking process itself. When you click a link that appears to go directly to your destination, malicious redirects route you through tracking domains that log your interest before forwarding you to the intended site.
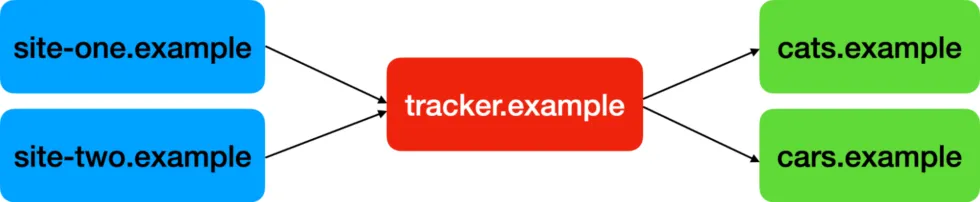
The attack works by manipulating link URLs that websites display versus where they actually send you. A news article might show a link to "amazon.com/product" in your browser's status bar, but the actual href attribute contains "tracker.example/redirect?url=amazon.com/product&user=12345". Your click triggers a navigation to the tracking domain, which records your visit in server logs, sets tracking cookies, and immediately redirects you to Amazon. The entire detour happens so quickly that most users never notice the intermediate stop.
This technique bypasses cookie blockers and script filters because no client-side tracking code runs on your device. The surveillance happens at the network level through HTTP server logs that record which IP addresses requested which redirect URLs. Even users with JavaScript disabled and all cookies blocked still generate trackable navigation patterns through these server-side logs.
Email marketing campaigns amplify bounce tracking through link modification services. When you receive promotional emails, every link gets rewritten to route through tracking proxies that log which recipients clicked which offers before redirecting to the actual destinations. These services build comprehensive profiles of your interests based purely on your clicking behavior, regardless of your browser's privacy settings.
Brave's debouncing feature (2021) recognizes bounce tracker URLs through pattern matching against known redirect domains and parameter structures. The browser maintains updated filter lists that identify tracking services like linksynergy.com, out.reddit.com, and facebook.com/l.php. When you click a link that matches these patterns, Brave extracts the final destination URL from the redirect parameters and navigates there directly.
The technical implementation examines URL structures in real-time during navigation events. Bounce tracking URLs typically contain the real destination encoded as query parameters, like "tracker.com/click?dest=example.com" or "redirect.service/go?u=https%3A//target.site". Brave's parser recognizes these common patterns, decodes the embedded destination URL, and replaces the navigation target before any network requests get sent to tracking domains.
This analysis happens locally within milliseconds of each click, using filter lists that get updated through Brave's component update system. The browser downloads new bounce tracking patterns automatically, similar to how antivirus software updates malware signatures. New tracking services get detected and added to filter lists faster than they can establish widespread adoption.
Unlinkable bouncing (2022) handles cases where you must visit tracking domains because they provide legitimate services beyond just surveillance. Some URL shorteners offer analytics to link creators, and some affiliate marketing systems require tracking for commission attribution. Complete blocking would break these services, so Brave implements selective memory wiping instead.
The browser creates temporary first-party storage areas for suspected tracking domains, isolated from your normal browsing data. When you visit a bounce tracker, any cookies, localStorage data, or other identifiers get stored in ephemeral containers that exist only for that browsing session. The moment you close all tabs for that tracking domain, Brave automatically deletes the temporary storage and all associated data.
This approach implements "first-party ephemeral storage" that extends beyond just clearing cookies. Modern tracking attempts use multiple browser storage mechanisms including IndexedDB, WebSQL, Cache API, and Service Worker registrations. Unlinkable bouncing wipes all of these storage types simultaneously, ensuring that tracking domains can't maintain persistent identifiers across your visits.
The memory isolation works bidirectionally, not only does the tracking domain lose memory of your previous visits, but it also can't correlate your current session with future ones. Each bounce tracking encounter starts with completely clean storage, making it impossible for trackers to build long-term behavioral profiles even when you must interact with their services.
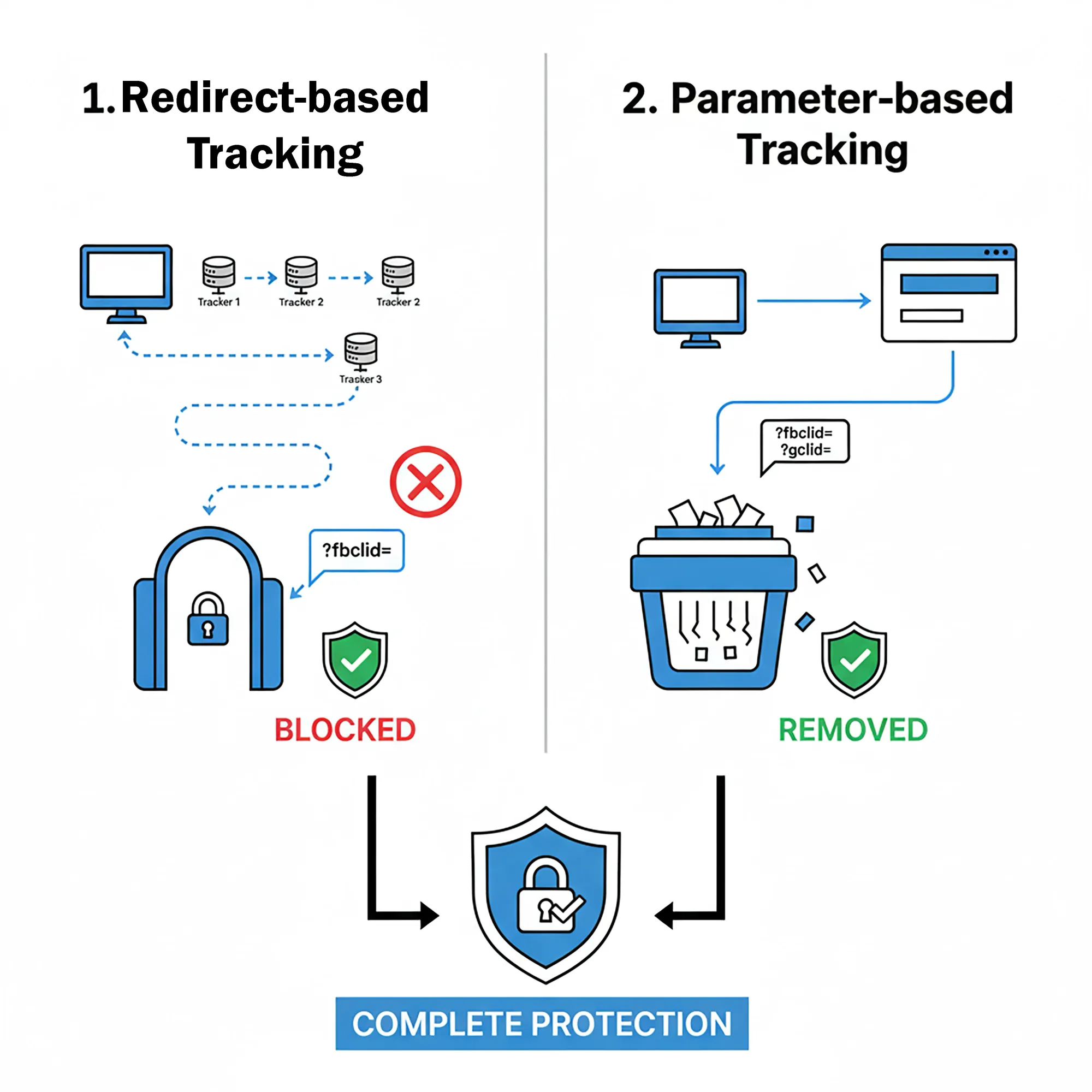
Combined with query parameter stripping that removes tracking codes like Facebook's fbclid and Google's gclid from URLs, these protections neutralize both redirect-based and parameter-based tracking methods. Your browsing patterns remain fragmented across isolated sessions rather than building into comprehensive surveillance profiles that follow you across the web.
The effectiveness compounds because most users encounter bounce tracking dozens of times per day without realizing it. Social media platforms, email newsletters, affiliate marketing links, and even legitimate news sites often route clicks through tracking intermediaries. Brave's automated detection and mitigation handles this invisible surveillance without requiring users to manually identify and avoid tracking services.
Tor Integration
Private Windows with Tor (2018) integrate The Onion Router directly into the browser engine, but the technical implementation reveals why this matters more than traditional VPN services for serious operational security. Tor's onion routing creates layered encryption where each network hop can only decrypt one layer to reveal the next destination, no single relay can trace the complete path from your device to destination servers.\

The cryptographic architecture uses nested encryption layers that get peeled away at each relay node. Your browser establishes a circuit through three randomly selected relays: a guard node, middle relay, and exit node. Each connection leg uses different encryption keys derived through Diffie-Hellman key exchange, ensuring that compromise of one relay can't decrypt traffic from other hops in the circuit.
Your traffic gets wrapped in three encryption layers before leaving your device. The outer layer contains routing information for the guard node, encrypted with that node's public key. Inside that wrapper sits another encrypted packet destined for the middle relay, and at the core lies the final packet for the exit node. Each relay can only decrypt its own layer, the guard node sees your IP address but not your destination, the middle relay sees neither source nor destination, and the exit node sees your destination but not your source IP.
This differs fundamentally from VPN architectures where single companies control entire network paths. Commercial VPN providers can log both your real IP address and your destination traffic because both endpoints terminate on their infrastructure. Even "no-logs" policies become meaningless when law enforcement can compel access to live traffic streams or install monitoring equipment on VPN servers.
Brave's integration runs tor as a subprocess that maintains separate SOCKS proxy connections for each private window. The browser doesn't simply route HTTP requests through Tor, it establishes independent circuits for DNS resolution, preventing correlation attacks where your DNS queries might reveal browsing patterns even when web traffic stays anonymous.
Circuit rotation happens automatically every ten minutes or when you request a new identity, forcing attackers to continuously reestablish surveillance across different network paths. Static VPN connections maintain the same route for entire sessions, making traffic analysis easier for adversaries who control multiple network observation points.
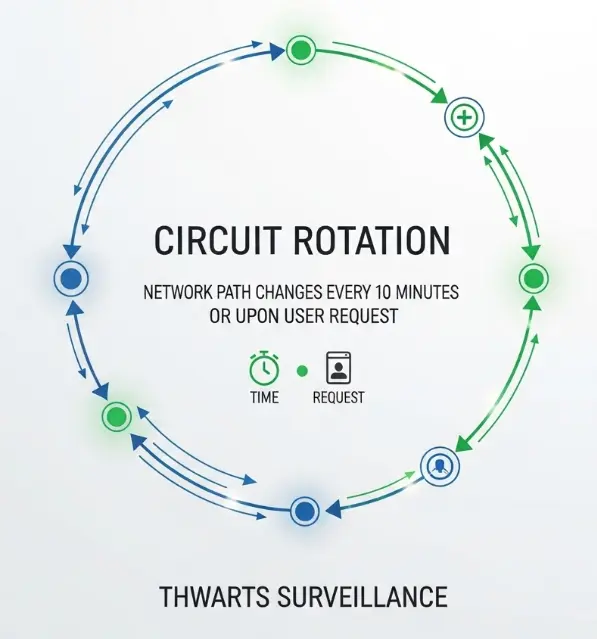
The tor subprocess runs isolated from Brave's main browser process through sandboxing that prevents cross-contamination between anonymous and identified browsing sessions. Private Tor windows use completely separate storage containers, cookie jars, and network stacks. Even if malicious websites exploit browser vulnerabilities in regular windows, they can't access data from Tor sessions or correlate your anonymous activity with your identified browsing.
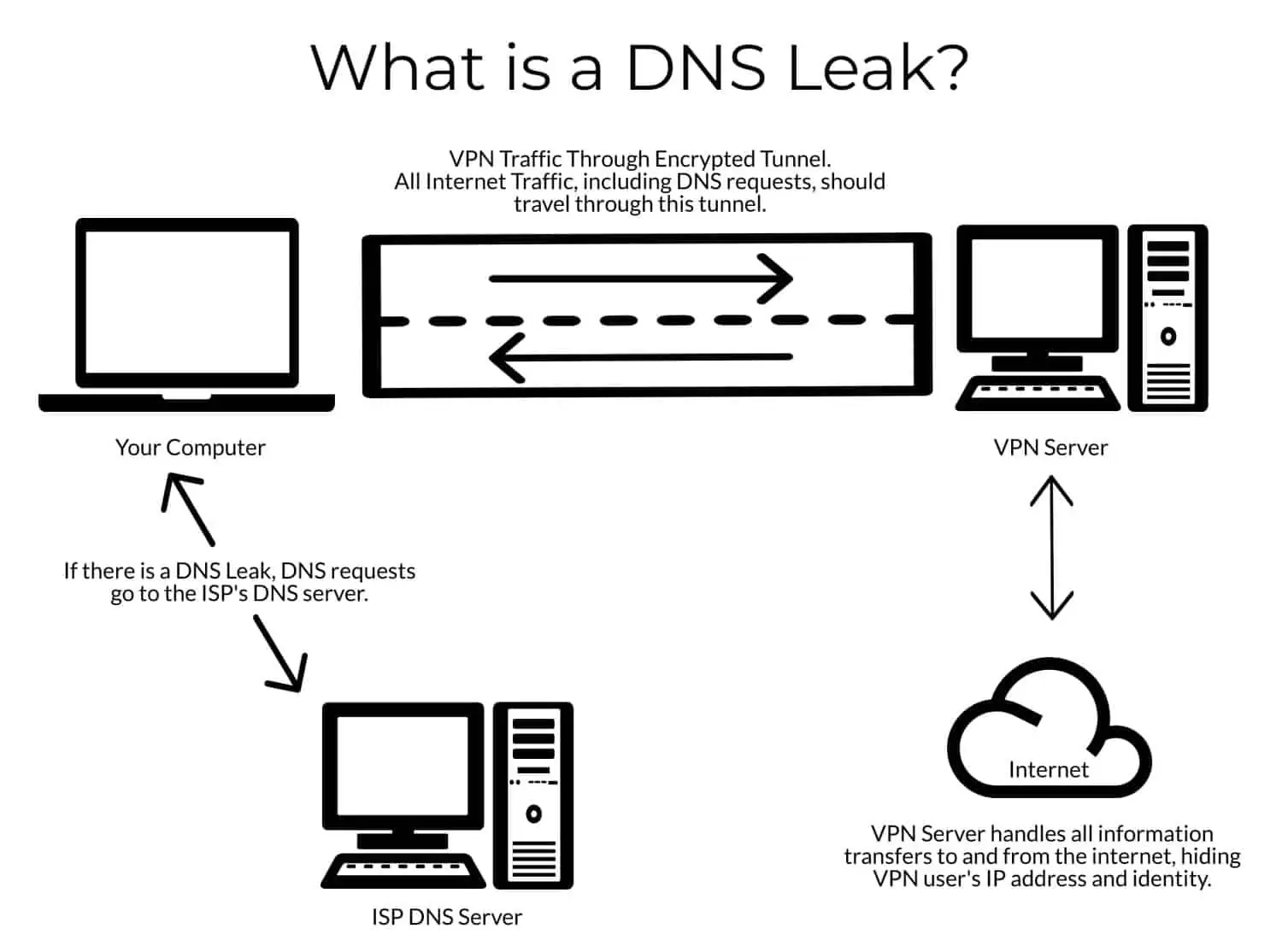
DNS resolution happens entirely within the Tor network rather than leaking queries to your ISP's resolvers. Traditional browsers send DNS requests to configured resolvers before establishing HTTP connections, revealing your intended destinations even when subsequent traffic gets encrypted. Brave's Tor integration resolves hostnames through the SOCKS proxy, ensuring that destination queries never escape the anonymity network.
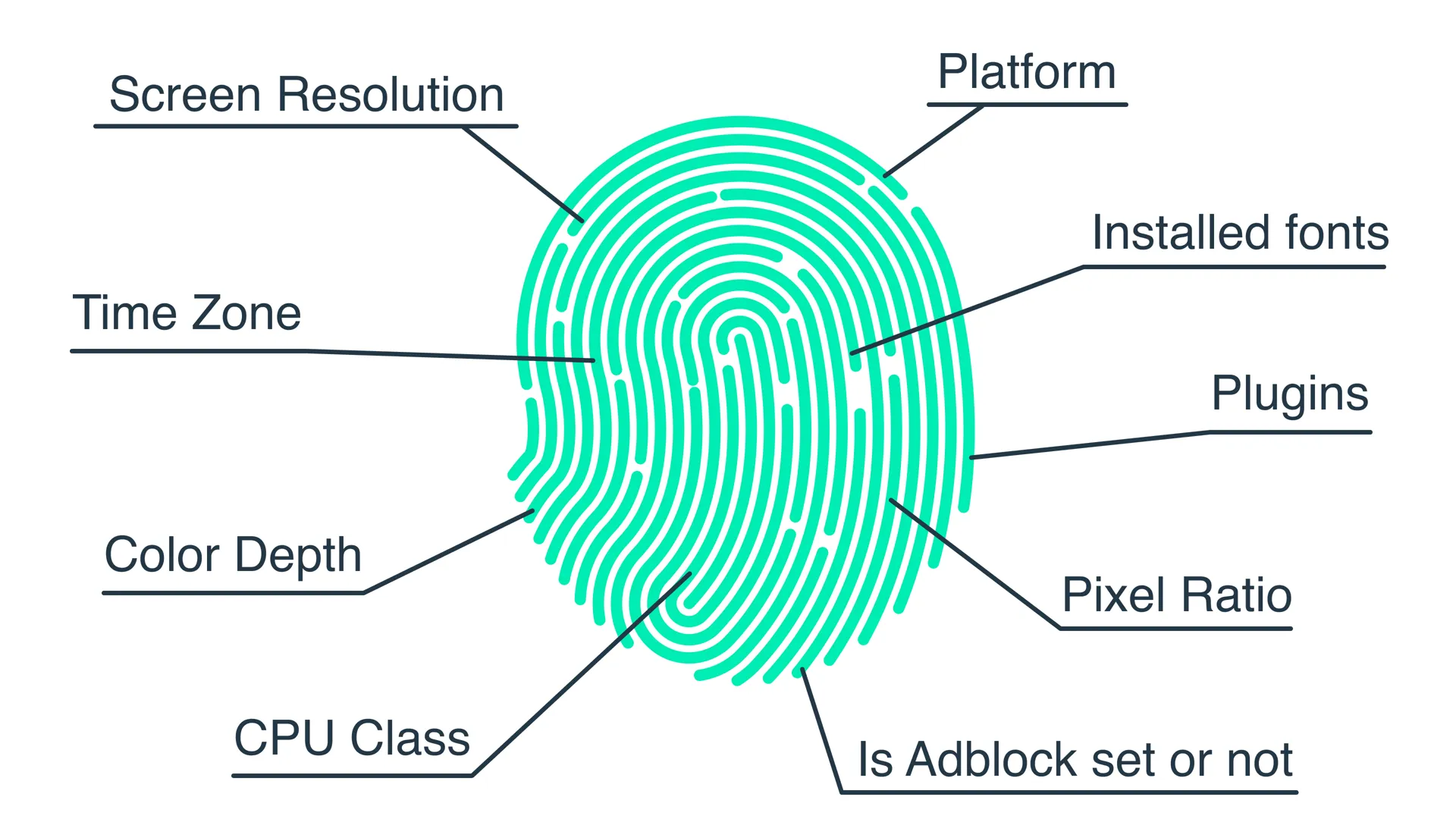
Browser fingerprinting resistance gets enhanced through Tor Browser's hardened user agent and feature detection responses. Tor windows report generic browser versions, screen resolutions, and installed plugin lists that match thousands of other Tor users. This fingerprint uniformity prevents websites from distinguishing individual users based on browser characteristics that normally create unique device signatures.
The JavaScript execution environment gets restricted to prevent timing attacks and resource enumeration that could reveal system details. High-precision timers get reduced to millisecond granularity, preventing websites from measuring execution speeds that might indicate specific hardware configurations. WebGL rendering gets disabled to prevent GPU fingerprinting, and media device enumeration gets blocked to hide camera and microphone details.
Exit node selection uses weighted probability that favors high-bandwidth relays while maintaining geographic diversity. The tor daemon automatically avoids exit nodes that might be controlled by the same entity as your guard node, reducing the probability that single adversaries can correlate traffic across multiple circuit hops. However, exit nodes can still observe unencrypted traffic, making HTTPS enforcement critical for protecting content privacy.
The threat model acknowledges that Tor doesn't provide perfect anonymity against well-resourced adversaries who control large portions of internet infrastructure. Traffic correlation attacks can potentially link entry and exit traffic when attackers observe both your ISP connection and destination servers. But for most operational security scenarios, this protection level exceeds what commercial privacy services can provide.
Network latency increases significantly compared to direct connections because traffic must traverse three random relays that might span multiple continents. This performance cost becomes acceptable for sensitive research, whistleblowing, or browsing in countries with internet censorship where anonymity outweighs speed considerations.
Brave's integration makes Tor accessible to mainstream users who wouldn't install and configure standalone anonymity software. The single-click activation lowers technical barriers while maintaining the same security properties as dedicated Tor Browser installations, potentially expanding the anonymity set that provides cover for all Tor users.
Search Independence!
Cutting Microsoft Dependencies
Brave Search achieved full independence from Microsoft Bing in April 2023. The transition eliminated the last external API dependencies that could be weaponized through pricing changes or service termination.
Microsoft's 2023 API price increases jumped 1000% in some cases. Search engines dependent on Bing faced impossible costs. DuckDuckGo still depends entirely on Bing's index, Microsoft could kill their business with a single contract change.
Brave operates its own web crawler and maintains an independent index of over 30 billion pages. The Brave Search API now competes directly with Google and Microsoft, offering developers an alternative to Big Tech's search infrastructure.
The Web Discovery Project contributes to index quality. Browser users who opt in share anonymous browsing data that helps identify high-quality pages. Unlike Google's invasive data collection, participation is optional and the data remains anonymized.
AI Without Surveillance
Brave Leo launched in November 2023 as the first privacy-preserving browser-native AI assistant. While Chrome and Edge force you to log into Google or Microsoft accounts for AI features, Leo requires no authentication.
The privacy architecture uses reverse proxies to anonymize requests. Your IP address gets stripped before queries reach AI model servers. Conversations get deleted immediately after responses generate, no persistent storage for training future models.
Model diversity reduces vendor lock-in. Leo supports Mixtral, Anthropic's Claude, Meta's Llama, and Qwen models. Users can even connect their own local models through Bring Your Own Model (BYOM) for complete control over AI inference. Learn how to actually implement it here:
Leo runs locally when possible. The browser can analyze page content without sending data to external servers. PDF analysis, page summarization, and content generation happen on-device for sensitive documents.
Web3 Infrastructure: IPFS and Wallet Integration
IPFS support (2021) made Brave the first major browser to handle decentralized web protocols natively, but the technical implementation reveals why content addressing threatens surveillance capitalism's foundation. InterPlanetary File System replaces location-based URLs with cryptographic content identifiers (CIDs) derived from SHA-256 hashes of the actual data. When you request content, the network verifies that received data matches the requested hash tampering becomes mathematically impossible rather than policy-dependent.
The browser integration runs go-ipfs as a subprocess that maintains its own DHT (Distributed Hash Table) connections to the IPFS swarm. Type an IPFS hash into Brave's address bar and the local node queries peer nodes for content chunks, reconstructs the original file through merkle tree verification, then serves it to the browser engine as if it came from a traditional web server. This eliminates single points of failure that enable censorship, content persists as long as any network participant hosts copies.
Brave's IPFS node implementation includes block deduplication across different content identifiers. Multiple websites might reference the same image or JavaScript library, but IPFS stores only one copy locally regardless of how many sites link to it. This storage efficiency becomes crucial for surveillance resistance because it reduces the cost of hosting controversial content across many nodes.
Brave Wallet integration eliminates the attack surfaces that browser extensions create through elevated privileges and remote code execution vectors. Traditional cryptocurrency wallets run as browser extensions that inject JavaScript into every webpage and maintain persistent background processes with access to all browsing activity. These extensions often phone home to their developers' servers for balance updates and transaction broadcasting.
The integrated wallet approach confines cryptocurrency operations within the browser's existing security sandbox. Private keys get stored in the browser's encrypted profile directory using the same key derivation functions that protect saved passwords. Transaction signing happens through native browser APIs rather than injected scripts that could be intercepted by malicious websites.
Multi-chain support spans Ethereum's virtual machine for smart contract execution, Solana's proof-of-history consensus for high-throughput transactions, and Filecoin for decentralized storage incentives. Each blockchain requires different cryptographic primitives—secp256k1 elliptic curves for Ethereum, Ed25519 signatures for Solana, and merkle proofs for Filecoin storage verification. The wallet handles these differences transparently while maintaining consistent security guarantees across networks.
The notable limitation is Brave Wallet's lack of support for privacy-focused cryptocurrencies like Monero (XMR), despite years of community requests. This creates an operational security gap where users need external wallets for truly private transactions. Monero's ring signatures, stealth addresses, and RingCT technology provide mathematical privacy guarantees that surpass any surveillance coin. The irony of a privacy-first browser excluding the most private cryptocurrency exposes Brave's incomplete commitment to financial anonymity.
Bitcoin support remains limited to basic wallet functionality without advanced privacy features like CoinJoin mixing or Lightning Network channels. Users requiring serious financial privacy must rely on dedicated privacy wallets like Cake Wallet or Feather Wallet for XMR transactions, fragmenting their operational security across multiple applications (lame).
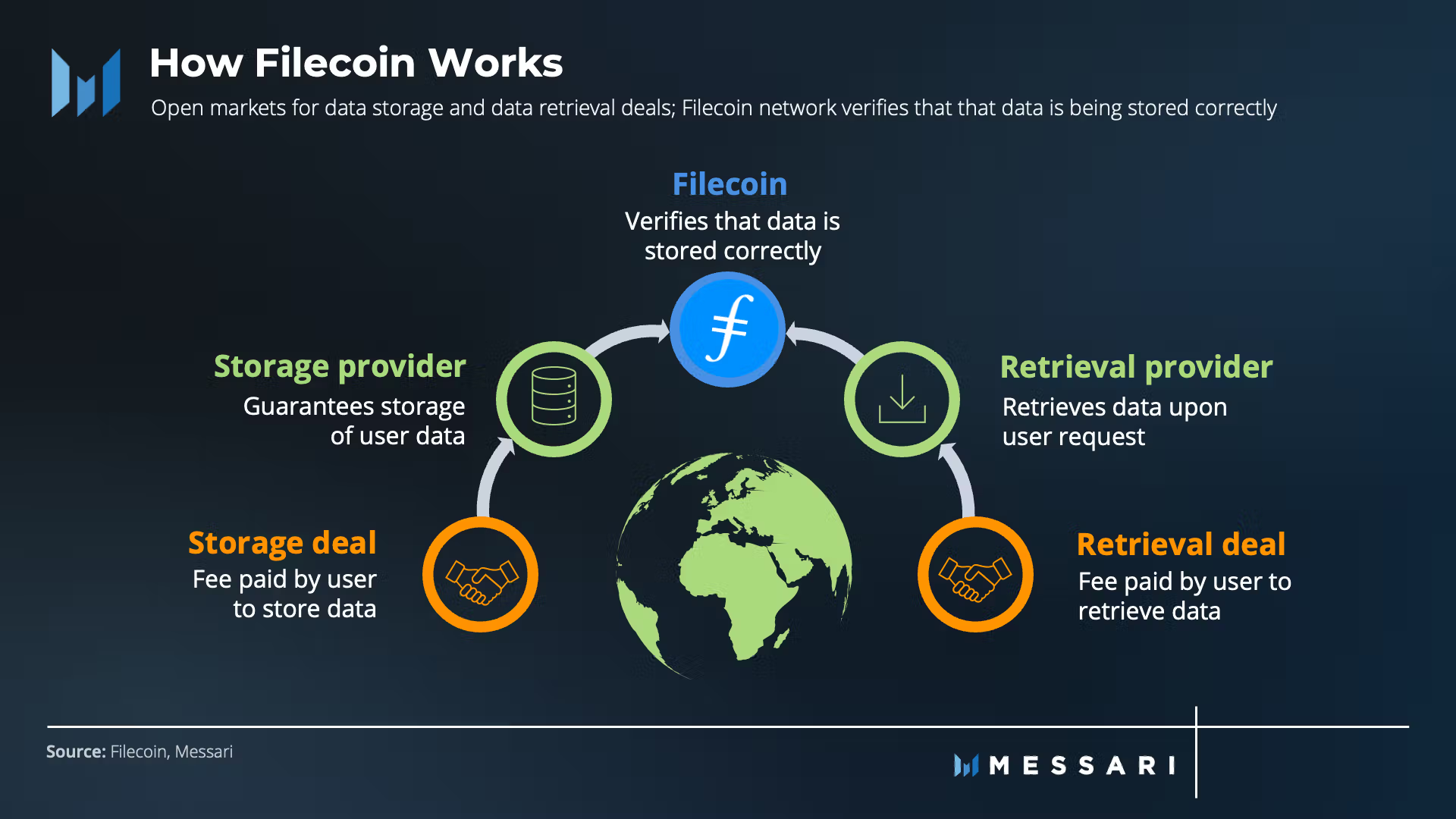
The Filecoin integration extends storage capabilities through cryptographic contracts that incentivize long-term data persistence. Instead of hoping volunteer IPFS nodes continue hosting content indefinitely, Filecoin pays storage providers through smart contracts that verify data integrity using zero-knowledge proofs. Brave facilitates these storage deals directly through the browser interface, making decentralized storage accessible without corporate intermediaries that comply with takedown requests.
This architecture challenges centralized storage models where cloud providers can terminate accounts, freeze assets, or comply with censorship demands. Filecoin's cryptographic verification ensures stored data remains unmodified and available as long as storage contracts remain funded, creating censorship-resistant infrastructure for sensitive documents and communications.
User Rewards vs. Surveillance
Brave Ads (2019) inverted the traditional advertising model. Instead of tracking users to serve targeted ads, Brave matches ads locally on-device and pays users directly in Basic Attention Tokens (BAT).
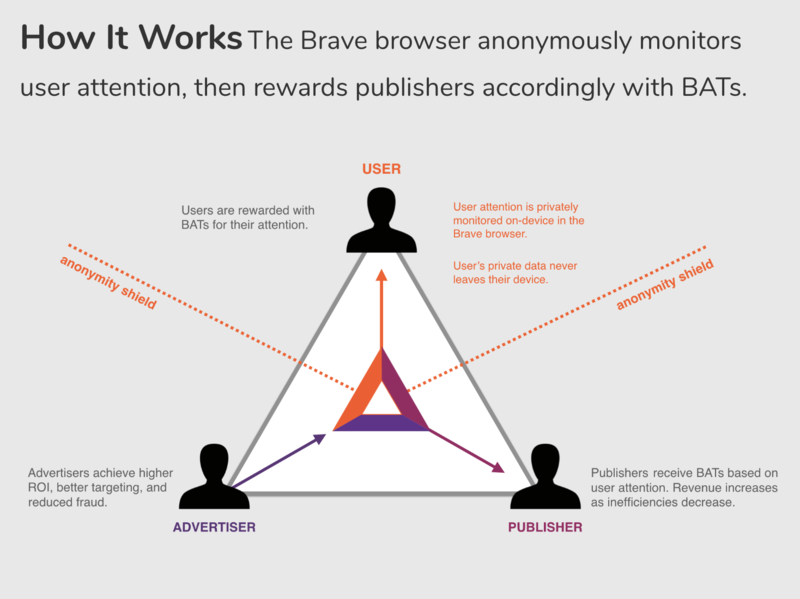
The privacy model matters operationally. Google's ad targeting requires detailed behavioral profiles stored on their servers. Brave's ad matching happens entirely on your device, the browser examines your browsing patterns locally and serves relevant ads without transmitting personal data.
Users earn 70% of ad revenue through BAT rewards. Publishers receive tips and contributions from users who value their content. Advertisers pay for attention rather than surveillance data.
The model scales without privacy compromise. Brave processed over 8 billion annualized searches while maintaining its no-logging policy. Revenue grows through user base expansion rather than increased data extraction per user.
Vertical Integration Strategy
Brave's architecture eliminates external dependencies that create surveillance vectors and business risks. The integrated stack includes:
- Browser engine: Chromium base with privacy modifications
- Search index: Independent crawling and ranking
- Ad network: Local matching without user tracking
- AI models: Multiple providers with anonymized access
- DNS resolution: Custom servers with filtering
- Cryptocurrency wallet: Multi-chain storage and DeFi access
- IPFS node: Decentralized content distribution
This integration reduces attack surfaces compared to extension-based privacy tools. Browser extensions run with elevated privileges and often phone home to their own servers. Brave's built-in features eliminate these external connections.
The business model aligns with user interests.
Traditional browsers monetize through data collection or search deals with surveillance companies. Brave generates revenue by blocking surveillance and sharing profits with users.
Blocking Benefits
Independent measurements show 3-6x faster page loading with Brave's default blocking, but the technical reasons reveal why privacy and performance align rather than conflict. Tracking scripts execute JavaScript that polls device sensors, enumerates installed plugins, and canvas-fingerprints your GPU. These operations consume CPU cycles that delay actual content rendering.
Network-level blocking eliminates entire HTTP request chains before they consume bandwidth. A single Facebook Like button triggers requests to facebook.com, connect.facebook.net, and multiple CDN endpoints. Brave kills these requests at the network stack level, your browser never initiates TCP connections to tracking domains. Traditional ad blockers still establish connections before dropping responses, wasting round-trip time and battery power.
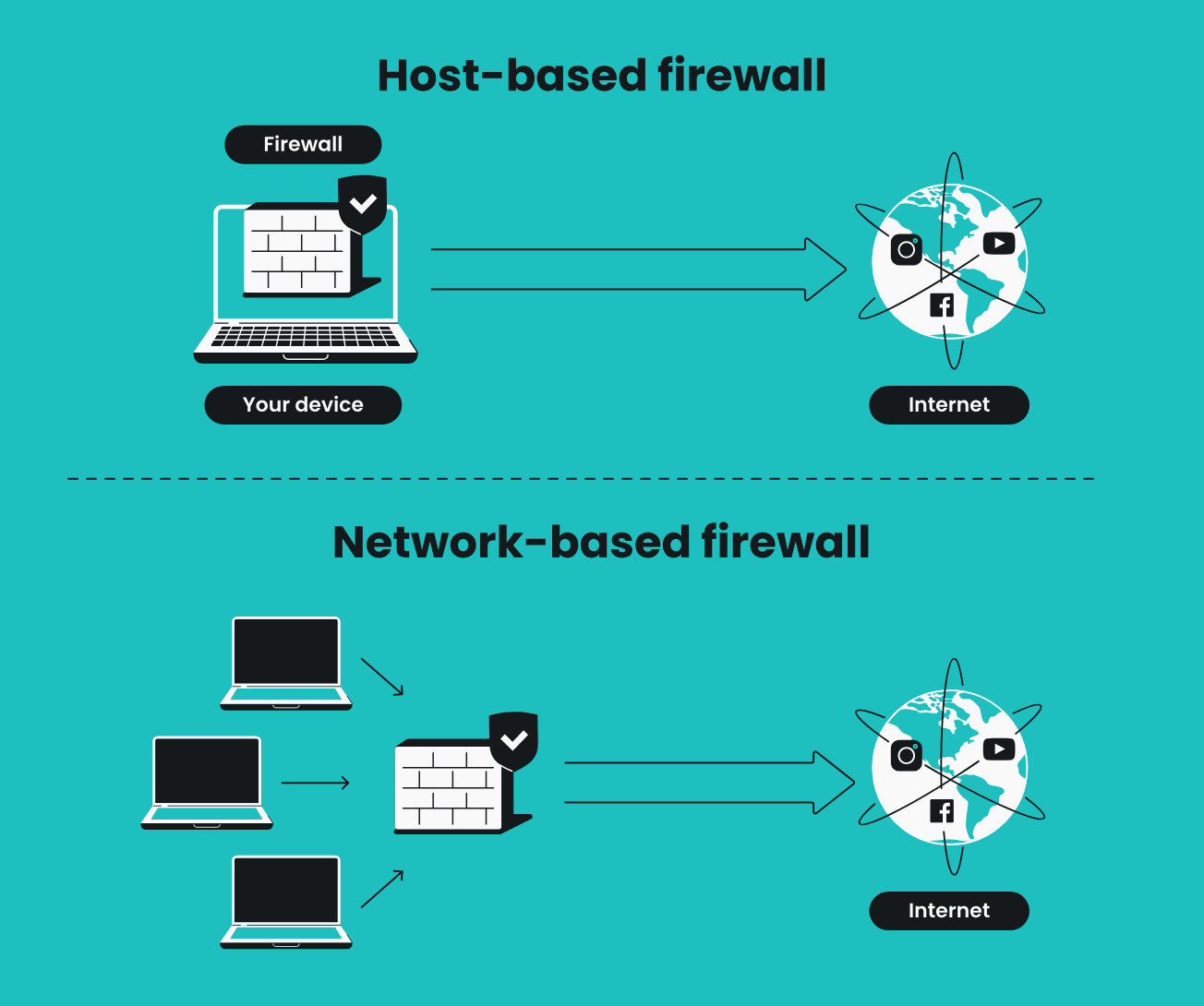
Resource loading becomes predictable without tracking scripts that dynamically inject additional content. Chrome renders pages, then loads dozens of tracking pixels that trigger layout recalculations. Each reflow forces the browser engine to recalculate element positions and repaint affected screen regions. Brave's blocking prevents these cascading performance hits.
Memory allocation patterns improve dramatically. Tracking scripts often create persistent background timers that wake up periodically to phone home with behavioral data. These timers consume memory and prevent JavaScript garbage collection from cleaning up unused objects. Chrome tabs gradually accumulate memory leaks from tracking code that never fully terminates.
Browser extensions for privacy run in separate processes that communicate with the main browser through inter-process messaging. Each blocked request requires serializing data across process boundaries, adding latency. Brave's integrated filters operate within the renderer process itself, decisions happen in microseconds rather than milliseconds.
CPU utilization drops because eliminated scripts never execute their fingerprinting algorithms. Canvas fingerprinting alone requires rendering text and graphics to hidden HTML5 elements, then reading pixel data back to generate device signatures. Audio context fingerprinting synthesizes sounds and analyzes the resulting waveforms. These operations stress both CPU and GPU resources for no user benefit.
The performance gap widens over time as surveillance techniques become more sophisticated. WebGL fingerprinting now renders 3D scenes to detect graphics drivers and hardware configurations. WebRTC probes enumerate local network interfaces to identify users behind NAT routers. Each new tracking method adds computational overhead that Brave eliminates while other browsers accumulate.
Network efficiency improvements compound across browsing sessions. Tracking domains serve megabytes of JavaScript libraries that get cached in browser storage. Brave never downloads these surveillance toolkits, leaving more cache space for actual content and reducing disk I/O operations that slow down subsequent page loads.
Threat Model
Brave's integrated approach dismantles the surveillance infrastructure that other browsers leave intact. Cross-site tracking fails because partitioned storage prevents websites from correlating your visits across domains. Third-party cookies get isolated or blocked entirely, breaking the data-sharing networks that advertising companies depend on.
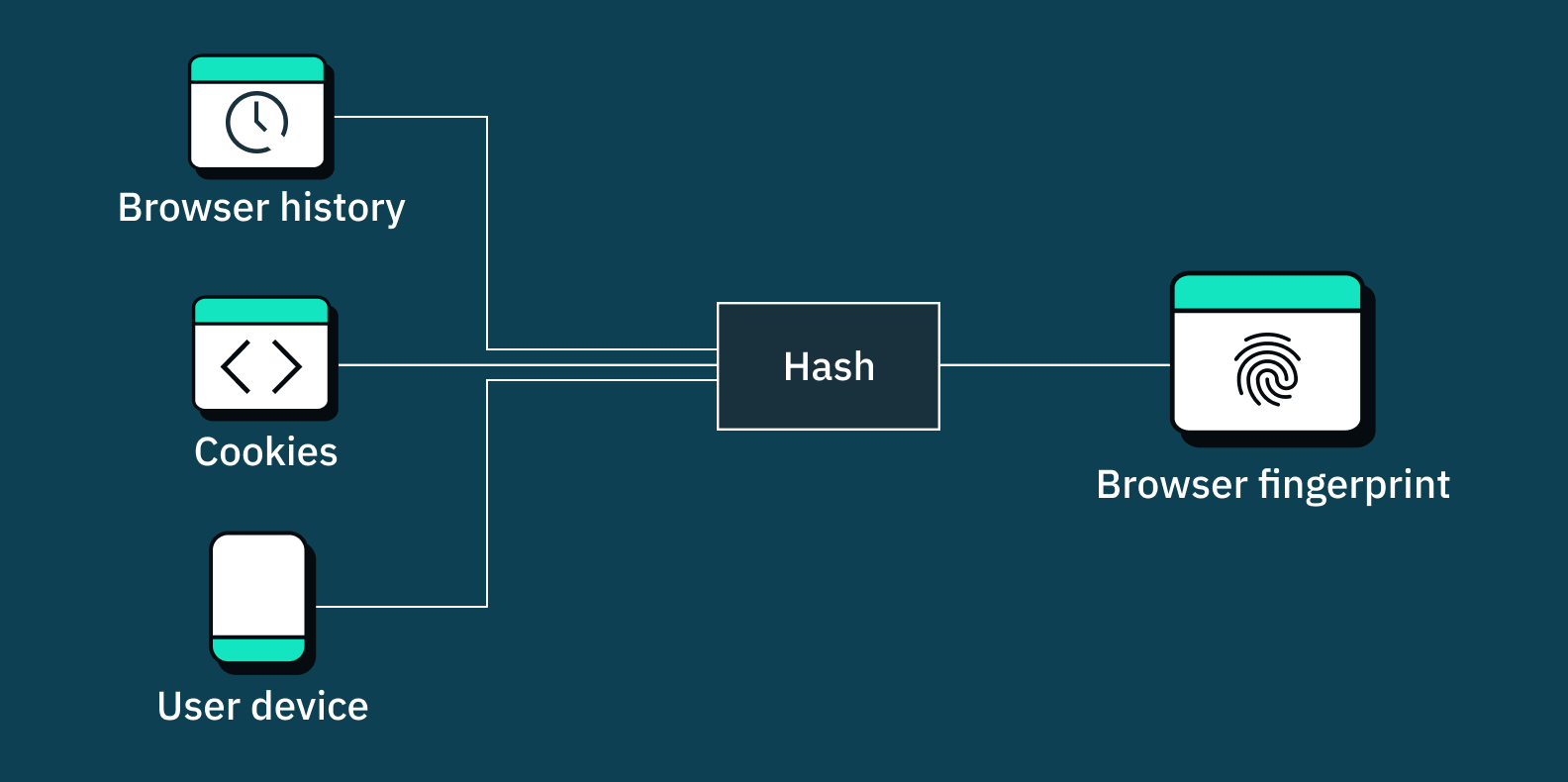
Browser fingerprinting attempts hit randomized characteristics instead of your actual device profile. Tracking scripts see different screen resolutions, font lists, and hardware specs on each visit. They can't build persistent profiles when your browser appears as a different device every time.
The debouncing and unlinkable bouncing systems neutralize redirect-based tracking that bypasses traditional cookie blocks. Automated detection skips intermediate tracking domains entirely, and when bounce visits become unavoidable, temporary storage prevents trackers from linking sessions across time. Your browsing patterns remain fragmented rather than building into comprehensive profiles.
DNS-level tracking gets blocked through custom servers that filter malicious domains and strip telemetry requests before they leave your machine. Search surveillance disappears entirely through Brave's independent index, your queries never flow through Google or Microsoft's data collection systems.
AI interactions stay anonymous through proxy servers that strip identifying information before requests reach language models. Your questions and interests can't build into behavioral profiles because the AI providers never see your real IP address or persistent identifiers. This prevents the next generation of surveillance where your private thoughts and research patterns get monetized through conversational data.
Each protection layer compounds the others. Traditional privacy tools might block some tracking cookies but miss fingerprinting attempts. Brave's systematic approach eliminates multiple attack vectors simultaneously, making comprehensive surveillance technically difficult rather than just policy-prohibited.
Strategic Impact
Brave proves that privacy browsers can achieve mainstream adoption. 94 million monthly users demonstrate market demand for alternatives to surveillance-funded platforms.
The integrated approach pressures other browsers to improve privacy features. Firefox, Safari, and even Chrome added tracking protections after Brave demonstrated their viability.
Search independence threatens Google's core revenue model. If alternative search engines gain adoption, Google loses both search ad revenue and the behavioral data that powers their broader advertising business.
Brave's success validates the principle that users will choose privacy when it doesn't require technical expertise or performance sacrifices.
Operational Recommendations
Brave Browser provides strong default privacy protections suitable for most users without modification. Enable Brave Ads only if you understand cryptocurrency implications.
For sensitive research, use Private Windows with Tor rather than VPNs from commercial providers. The distributed routing model resists traffic analysis better than centralized VPN services.
Consider Brave Search for queries that don't require Google's specialized databases. The independent index handles general searches without feeding your interests to surveillance companies.
Use Brave Wallet for cryptocurrency storage if you need multi-chain support without browser extensions. The integrated approach reduces attack surfaces compared to MetaMask and similar tools.
Brave's evolution from ad-blocker to comprehensive privacy platform demonstrates that Big Tech's surveillance model isn't inevitable. Users can choose alternatives that protect privacy while delivering competitive features and performance.
The browser wars matter because browsers control access to information. Brave's independence from Google and Microsoft's infrastructure creates genuine choice in how the web operates. Every user who switches reduces Big Tech's power to monitor and manipulate online behavior.




