I2P vs Tor: Why Garlic Routing Offers Better Anonymity for Darknet Markets
I2P's garlic routing provides superior anonymity through bidirectional tunnels and distributed architecture without central authorities.

I2P's garlic routing architecture provides superior anonymity for darknet marketplace operations compared to Tor's onion routing through bidirectional tunnels, distributed directory services, and resistance to traffic analysis attacks that commonly compromise Tor hidden services.
Garlic Routing vs Onion Routing Architecture
I2P implements garlic routing where multiple messages get bundled together and encrypted in layers, similar to cloves of garlic wrapped together, making traffic analysis significantly more difficult than Tor's onion routing approach.
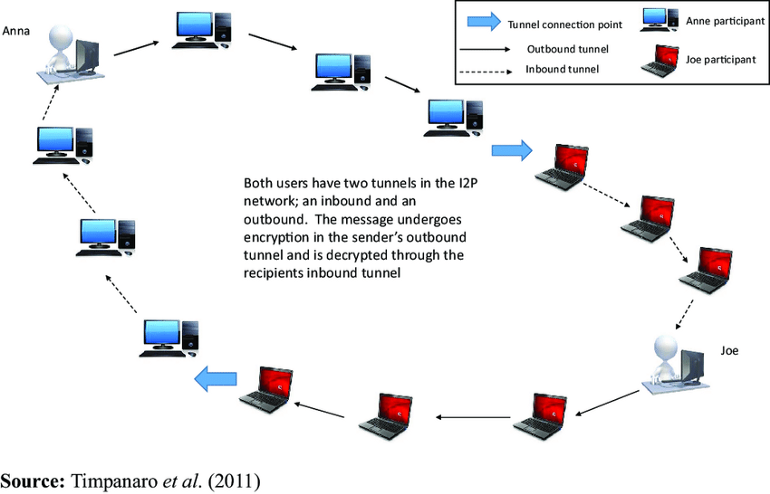
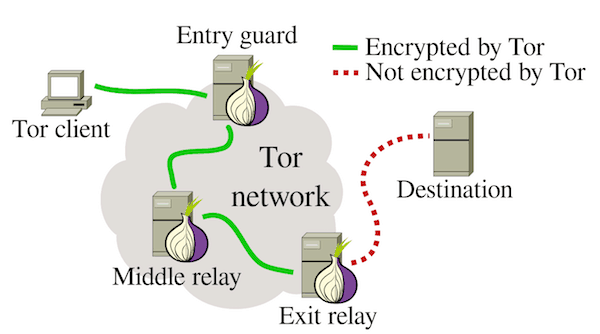
While Tor creates circuits through three relays for each connection,
I2P establishes two separate unidirectional tunnels - one for outbound traffic and another for inbound responses - with each tunnel typically consisting of two to three hops through different routers.
This bidirectional approach means that even if an attacker controls both the entry and exit points of communication, they cannot easily correlate traffic since outbound and inbound paths use completely different routes through the network. The garlic routing protocol allows multiple messages destined for different recipients to be bundled together in a single garlic message, creating additional confusion for traffic analysis attempts since observers cannot determine how many distinct communications are occurring or their intended destinations.
I2P routers maintain pools of pre-built tunnels that applications can use for communication, reducing the timing correlations that plague Tor's circuit establishment process where the time to build circuits can leak information about user behavior and destination patterns.
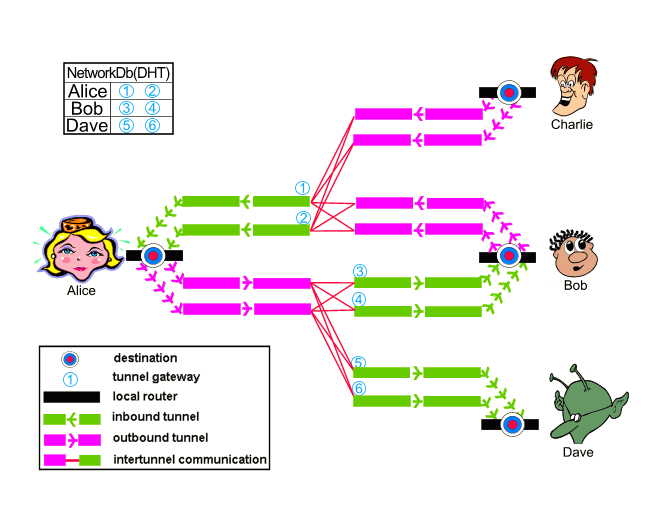
The tunnel-based architecture also provides better resistance to intersection attacks where adversaries monitor multiple network points to correlate user activities across time, since I2P's tunnels are rebuilt automatically on regular intervals and the paths change unpredictably.
Distributed Network Services and Eepsite Architecture
I2P operates as a fully distributed network without central directory authorities, unlike Tor's reliance on a small number of directory servers that create centralized points of failure and control. Every I2P router participates in a distributed hash table that maintains network state information, meaning there's no single point that can be compromised to monitor or disrupt the entire network. This distributed approach extends to eepsite hosting, where hidden services (equivalent to Tor's onion services) benefit from the network's peer-to-peer architecture rather than depending on centralized infrastructure that law enforcement can target.

I2P eepsites use base32-encoded addresses that are distributed through the network's DHT, making them resilient to takedown attempts since the directory information exists across thousands of nodes rather than a handful of directory authorities. The network's self-organizing nature means that as more users join I2P, the network becomes stronger and more resistant to attacks, while Tor's centralized directory system creates scalability bottlenecks and surveillance opportunities for well-resourced adversaries.
I2P's approach to service discovery through distributed hash tables also prevents the kind of hidden service directory correlation attacks that have been used against Tor, where monitoring directory requests can reveal user interest in specific hidden services even without accessing them directly. The peer-to-peer architecture makes it extremely difficult for adversaries to gain comprehensive network visibility, since they would need to compromise a significant portion of the entire network rather than just key infrastructure points.
Traffic Analysis Resistance and Market Security
I2P's design provides inherent protection against many traffic analysis techniques that have been successfully used against Tor-based darknet markets through its packet padding, message mixing, and tunnel diversity features.
The garlic routing protocol includes variable message delays and dummy traffic generation that makes timing correlation attacks significantly more difficult to execute successfully against I2P users compared to Tor users who generate more predictable traffic patterns. I2P automatically pads messages to standard sizes and mixes real traffic with cover traffic, creating a more uniform traffic signature that resists the kind of statistical analysis that law enforcement has used to de-anonymize Tor users through correlation of entry and exit traffic timing.
The network's tunnel diversity, where each application can use different tunnel paths simultaneously, prevents the single point of failure problem that affects Tor circuits where compromise of one circuit exposes all of a user's traffic during that session. For darknet market operations, I2P's resistance to traffic confirmation attacks provides critical protection since law enforcement often attempts to confirm suspected criminal activity by correlating network traffic patterns rather than breaking encryption directly.
The bidirectional tunnel architecture means that even sophisticated adversaries who can monitor large portions of internet infrastructure cannot easily perform end-to-end correlation attacks, since the inbound and outbound paths traverse different network segments with different timing characteristics. I2P's automatic load balancing across multiple tunnels also provides natural protection against traffic analysis, since user activities get distributed across multiple paths with varying latencies and bandwidth characteristics that frustrate attempts to build consistent traffic profiles for individual users or services.