How SpiderFoot CLI Automation Transforms OSINT Reconnaissance Into Scalable Threat Intelligence Operations
SpiderFoot CLI automation enables large-scale subdomain enumeration and threat intelligence gathering through 200+ reconnaissance modules, processing thousands of targets while maintaining operational security.

SpiderFoot transforms manual OSINT reconnaissance into automated intelligence gathering through comprehensive subdomain enumeration , threat intelligence correlation, and data relationship mapping that reveals attack surfaces and security exposures across entire organizational infrastructures.SpiderFoot documentationdemonstrates how CLI automation allows large-scale reconnaissance operations that process thousands of targets simultaneously while maintaining operational security through proxy rotation , rate limiting, and traffic obfuscation techniques that prevent detection and blocking by target organizations.
SpiderFoot Architecture and Modular Intelligence Collection
SpiderFoot uses a modular architecture where specialized reconnaissance modules collect data from diverse sources including DNS records,, search engines, social media platforms, and commercial threat intelligence feeds.SpiderFoot GitHub repositorycontains over 200 reconnaissance modules categorized by data source and collection methodology, with passive modules gathering publicly available information without direct target interaction, active modules performing controlled probes and queries, and invasive modules conducting comprehensive enumeration that may trigger security monitoring.
Data correlation engine processes collected intelligence through relationship mapping algorithms that identify connections between IP addresses, domain names, email addresses, social media accounts, and organizational infrastructure. The correlation system builds comprehensive target profiles by analyzing DNS relationships, certificate authority patterns, hosting provider associations, and administrative contact overlaps that reveal hidden infrastructure and organizational boundaries..
Module execution follows configurable workflows where reconnaissance phases build upon previous discoveries, with initial passive collection feeding active enumeration targets, and active results triggering specialized modules for vulnerability assessment, credential harvesting, and infrastructure mapping. API integration allows real-time data enrichment from commercial threat intelligence platforms, vulnerability databases, and specialized OSINT services that provide additional context and validation for collected intelligence.
Automated Subdomain Enumeration and Infrastructure Discovery
Passive subdomain discovery usesCertificate Transparency logs, DNS zone transfers, and search engine dorking to identify subdomains without generating detectable traffic to target infrastructure. Certificate transparency mining reveals historical and current subdomain certificates through automated CT log queries that process millions of certificate records to extract relevant subdomain information for target organizations.
Active subdomain enumeration uses brute-force wordlist attacks, permutation generation, and DNS record enumeration through carefully crafted queries that balance discovery effectiveness against detection risk.DNS enumeration techniquesprovides comprehensive enumeration techniques including recursive DNS queries, reverse DNS lookups, and zone walking that reveal additional subdomains and infrastructure components not discoverable through passive methods alone.
Search engine automation queries Google, Bing, DuckDuckGo, and specialized search platforms using automated dorking techniques that extract subdomain references from cached pages, indexed documents, and public code repositories. Advanced search operators combined with automated result parsing enable large-scale subdomain discovery from search engine indexes while respecting rate limits and avoiding automated query detection mechanisms.
DNS infrastructure analysis examines nameserver configurations, MX records, SPF/DKIM policies, and DNSSEC useations to identify mail servers, content delivery networks, and third-party service integrations that expand the attack surface beyond directly controlled infrastructure. Automated analysis reveals misconfigured DNS records, expired domains, and subdomain takeover opportunities that pose security risks to target organizations.
Threat Intelligence Integration and Risk Assessment
Indicator of Compromise (IOC) collection validates discovered infrastructure against threat intelligence databases containing known malicious IP addresses, domains, and certificate fingerprints.threat intelligence platformsprovides structured threat intelligence that allows automated risk scoring based on reputation data, malware associations, and historical compromise indicators that prioritize security assessment efforts.
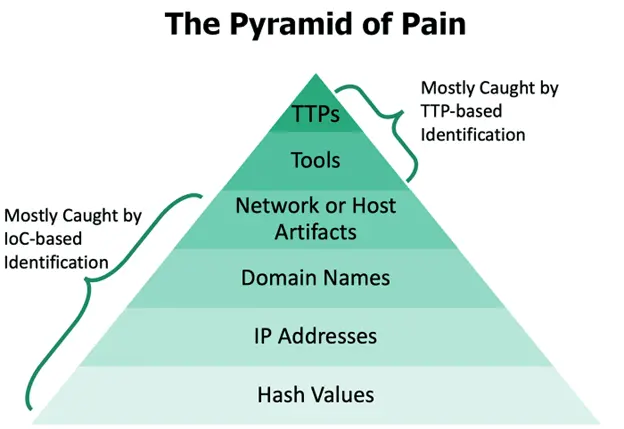
Threat actor attribution correlates infrastructure patterns with known adversary tactics, techniques, and procedures (TTPs) through behavioral analysis and infrastructure fingerprinting that identifies potential threat actor groups targeting the organization. Attribution analysis examines hosting patterns, certificate usage, domain registration practices, and operational security indicators that suggest specific threat actor involvement or campaign association
Vulnerability correlation cross-references discovered services and technologies against CVE databases, exploit frameworks, and security advisory feeds to identify potential attack vectors and exploitation opportunities. Automated vulnerability assessment prioritizes findings based on exploitability, impact, and available exploit code that allows rapid security assessment and remediation planning.
Risk scoring algorithms combine threat intelligence data, vulnerability assessments, and exposure metrics to generate prioritized risk assessments that guide security team response efforts. Scoring considers factors including public exposure, service criticality, vulnerability severity, and threat actor interest to produce actionable intelligence for security operations and incident response teams.
CLI Automation and Scalable Operation Workflows
Command-line automation allows batch processing of multiple targets through scripted execution workflows that handle thousands of domains, IP ranges, and organizational identifiers simultaneously.SpiderFoot GitHub repositoryprovides comprehensive CLI documentation showing parameter optimization, module selection, and output configuration that maximizes reconnaissance efficiency while maintaining operational security through automated proxy rotation and request timing.
Parallel execution strategies distribute reconnaissance workloads across multiple processes and systems to accelerate large-scale operations while respecting rate limits and avoiding detection. Advanced automation uses intelligent load balancing, failure recovery, and progress monitoring that ensures reliable execution of long-running reconnaissance campaigns spanning days or weeks of continuous operation.
Output parsing automation extracts structured data from SpiderFoot results through custom parsers and data transformation scripts that integrate with security information and event management (SIEM) systems, vulnerability management platforms, and threat intelligence platforms. Automated parsing allows real-time intelligence feed generation, alert triggering, and dashboard visualization for continuous security monitoring operations.
Integration withsubdomain enumeration toolsandOSINT automation frameworkscreates comprehensive OSINT automation pipelines that combine multiple reconnaissance tools through coordinated execution workflows. Tool integration allows cross-validation of results, data enrichment through multiple sources, and comprehensive attack surface mapping that provides complete organizational intelligence pictures.
Operational Security and Stealth Reconnaissance Techniques
Proxy rotation and traffic obfuscation prevent reconnaissance detection through distributed query execution across multiple IP addresses, user agents, and request patterns that mimic legitimate traffic rather than automated scanning. Advanced stealth techniques include timing randomization, request header variation, and traffic shaping that avoid triggering rate limiting, bot detection, and security monitoring systems.
Data sanitization procedures ensure that collected intelligence removes personally identifiable information (PII), sensitive credentials, and confidential business information that could violate privacy regulations or create liability exposure. Automated sanitization filters use configurable rules for data classification, retention policies, and sharing restrictions that maintain operational security while enabling intelligence sharing and collaboration.
Large-scale deployment considerations include resource management, bandwidth optimization, and infrastructure scaling that allows reconnaissance operations across enterprise-scale target lists without overwhelming local network capacity or triggering provider-level traffic analysis. Deployment architectures use cloud computing, containerization, and distributed processing to achieve massive scale while maintaining cost efficiency and operational flexibility.
Reporting automation generates standardized intelligence reports, executive summaries, and technical documentation through templated reporting systems that transform raw reconnaissance data into actionable intelligence for diverse stakeholder audiences.OSINT methodology guideprovides best practices for intelligence presentation, risk communication, and actionable recommendation generation that allows effective security decision-making based on OSINT collection results.




