How Monero's Ring Signatures Provide True Transaction Privacy
Monero uses ring signatures, stealth addresses, and RingCT to provide complete transaction privacy through cryptographic mathematics.

Monero implements ring signatures as a cryptographic mechanism that obscures transaction origins by mixing a real transaction input with decoy inputs from the blockchain. This mathematical approach creates plausible deniability about which inputs are actually being spent, providing transaction privacy that Bitcoin and most cryptocurrencies lack entirely.
Ring Signature Construction and Mathematics
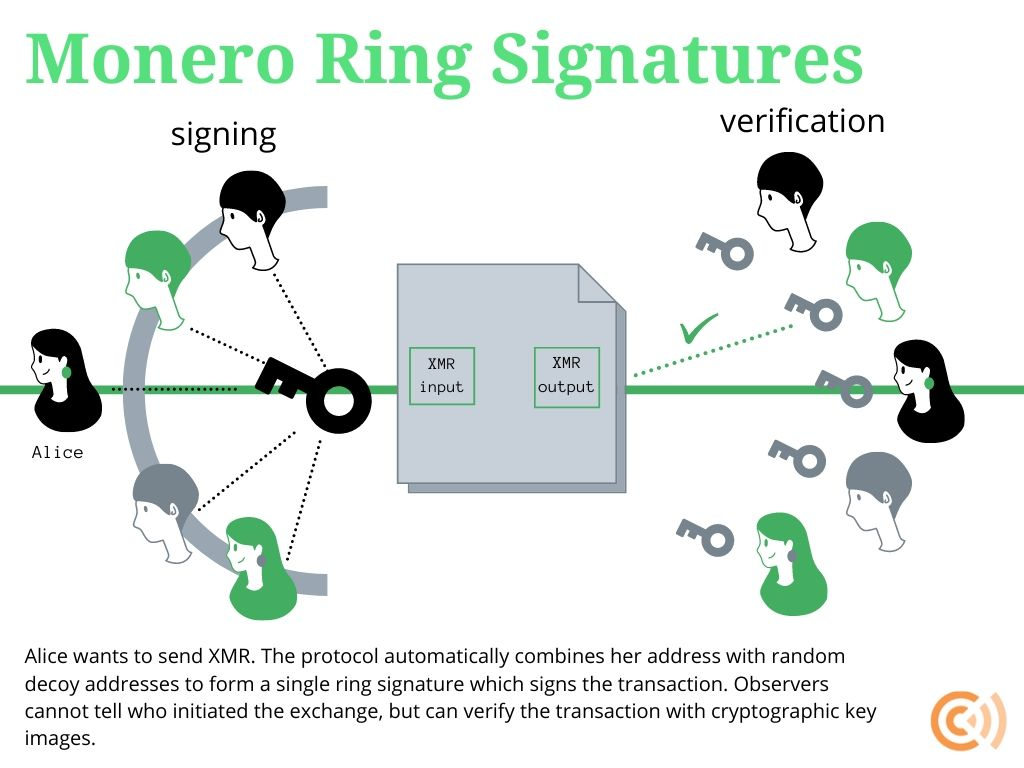
Ring signatures work by allowing any member of a group to produce a signature on behalf of the group without revealing which specific member created it. In Monero's implementation, when Alice wants to spend an output, her wallet automatically selects multiple other outputs from the blockchain as decoys and creates a mathematical proof that she knows the private key for one of these outputs without revealing which one.
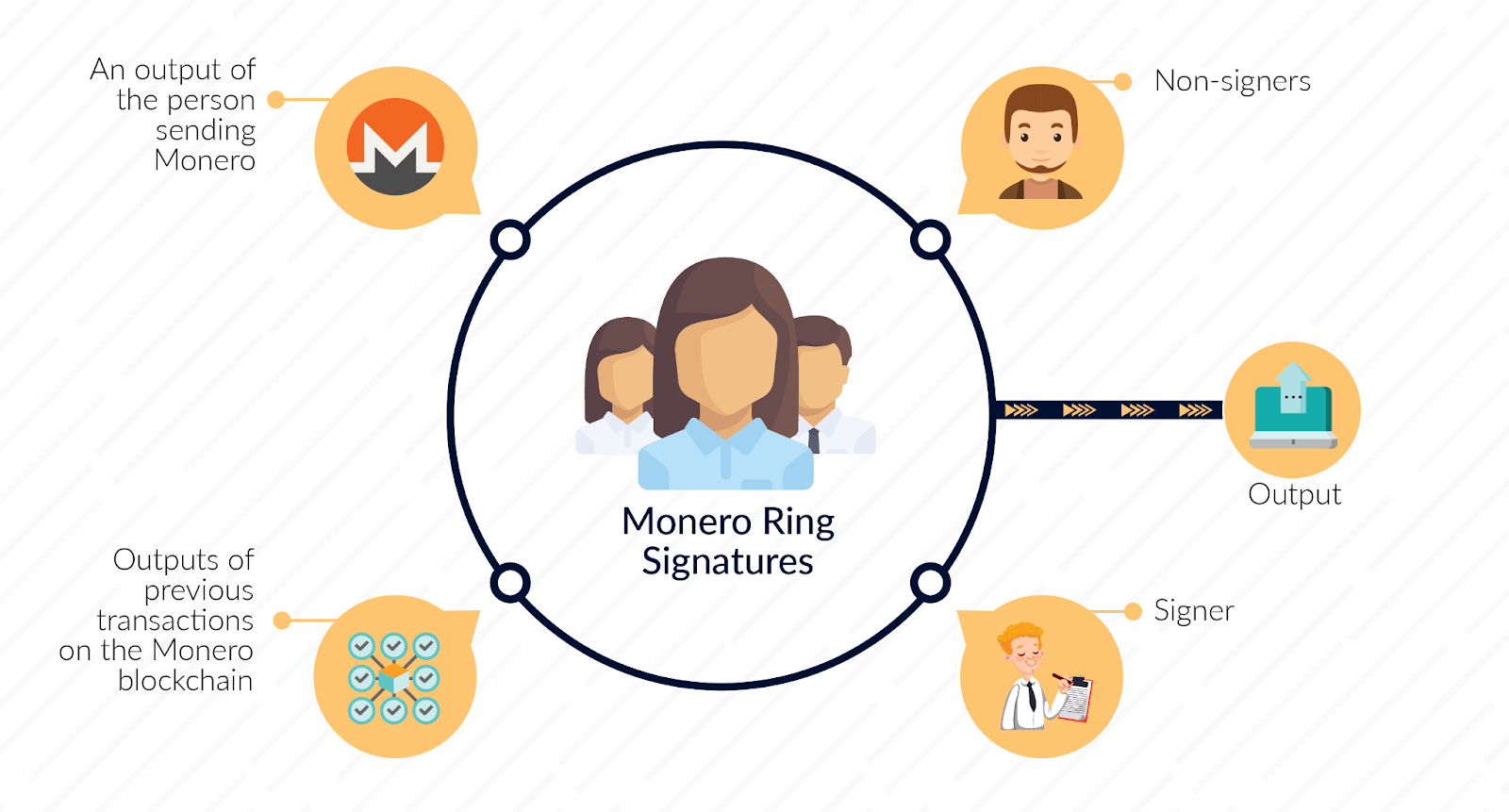
The signature proves that the transaction is valid and authorized while maintaining ambiguity about the actual spender. This differs fundamentally from Bitcoin's transparent model where every transaction input clearly identifies which previous output is being spent. The cryptographic construction uses elliptic curve mathematics to create linkable ring signatures, meaning that while the specific signer remains anonymous within the ring, double-spending attempts can still be detected and prevented.
The signature algorithm ensures that if someone tries to spend the same output twice, the two signatures will be mathematically linked, exposing the double-spend attempt without compromising the anonymity of legitimate transactions. The ring size, or number of decoy outputs included in each signature, directly affects the anonymity set - a larger ring provides better privacy by creating more possible spenders, while smaller rings reduce transaction size and verification time.
Stealth Addresses and Output Unlinkability
Monero combines ring signatures with stealth addresses to prevent transaction outputs from being linked together on the blockchain. When Alice sends Monero to Bob, her wallet doesn't send to Bob's published address directly.
Instead, it uses Bob's public address to derive a one-time stealth address that appears completely unrelated to Bob's known address. This means external observers cannot determine that Bob received funds, even if they know his public address.
The stealth address system works through elliptic curve Diffie-Hellman key exchange, where Alice uses Bob's public view key and spend key along with a random number to generate a unique destination address for each transaction.
Bob can scan the blockchain using his private view key to identify transactions sent to him by attempting to derive the stealth addresses for all transactions and checking if any were created using his keys. This scanning process reveals Bob's incoming transactions to him while keeping them invisible to everyone else.
The separation between view keys and spend keys allows for selective transparency - Bob can share his view key with trusted parties like accountants or auditors to prove transactions without giving them the ability to spend his funds.
This granular control over transaction visibility sets Monero apart from cryptocurrencies that rely solely on address reuse patterns for privacy, which inevitably fail as addresses get reused or linked through external services.
RingCT and Amount Hiding
Ring Confidential Transactions represent Monero's solution to hiding transaction amounts while maintaining mathematical verifiability that inputs equal outputs plus fees.
Before RingCT, Monero transactions revealed the amounts being transferred, which could be used to correlate transactions and reduce privacy. RingCT uses Pedersen commitments and range proofs to encrypt transaction amounts while still allowing network validators to verify that transactions balance correctly without inflation.
The Pedersen commitment scheme allows Monero to prove that transaction inputs equal outputs without revealing the specific amounts involved. Network nodes can verify that no money is being created or destroyed while remaining ignorant of the actual values being transferred. Range proofs prevent negative amounts from being committed, which could otherwise be used to create money out of nothing by committing to negative values that would wrap around in modular arithmetic.
The bulletproofs implementation used in modern Monero reduces the size of these range proofs significantly compared to earlier implementations, making RingCT transactions smaller and more efficient. This mathematical approach to amount hiding means that even if an attacker could somehow break the ring signature anonymity to identify which outputs are being spent, they still wouldn't know how much Monero was transferred in any given transaction.
The combination of ring signatures for sender anonymity, stealth addresses for recipient privacy, and RingCT for amount confidentiality creates a comprehensive privacy system that protects all aspects of transaction metadata that Bitcoin and other transparent cryptocurrencies expose by default.




