How ChaCha20-Poly1305 AEAD Delivers Constant-Time Authenticated Encryption Without Timing Vulnerabilities
ChaCha20-Poly1305 AEAD combines stream cipher encryption with universal hash authentication, delivering 2-4x performance over AES-GCM on mobile processors while resisting timing attacks through constant-time implementation.
ChaCha20-Poly1305 AEAD is a modern encryption system that combines two powerful cryptographic tools to keep your data both secret and tamper-proof. Unlike older encryption methods, this system resists timing attacks—a sophisticated hacking technique where attackers measure how long encryption takes to guess secret keys.
What makes ChaCha20-Poly1305 special is that it runs faster than traditional AES-GCM encryption on smartphones and tablets, while using constant-time implementation that takes the same amount of time regardless of what data is being encrypted.
The RFC 8439 specification officially defines how this system works by combining Daniel J. Bernstein's ChaCha20 stream cipher (which scrambles your data) with the Poly1305 universal hash function (which creates a digital fingerprint to detect tampering). This creates authenticated encryption with associated data—meaning it protects both your message's secrecy and proves no one has modified it, all without needing special computer chips or complicated key management systems.
ChaCha20 Stream Cipher Architecture and Quarter-Round Operations
ChaCha20 works by repeatedly applying quarter-round functions. These functions mix four 32-bit pieces of data together using three simple computer operations: addition, rotation, and XOR (exclusive or). The goal is to quickly spread changes throughout the entire encryption state, making the output look completely random. The ChaCha20 research paper shows the mathematical foundation behind this process. Each quarter-round performs a specific sequence: a += b; d ^= a; d <<<= 16; c += d; b ^= c; b <<<= 12.
This creates mathematical relationships that resist two major types of cryptographic attacks called differential and linear cryptanalysis. The design remains simple to implement on many different types of computer processors.
ChaCha20's 4×4 Matrix Structure
This grid gets mixed 20 times to create random-looking output
Key expansion takes your 256-bit encryption key and transforms it into a larger 512-bit internal state. This happens by carefully arranging your key material, nonce values (unique numbers used once), and counter information into a 4x4 grid of 32-bit words. Think of this grid like a spreadsheet with 16 cells, each containing a 32-bit number.
The cipher then applies 20 rounds of quarter-round operations. These rounds alternate between working on columns (10 rounds) and diagonals (10 rounds) of the grid. This process produces 512 bits of pseudorandom output per block. By incrementing the block counter, ChaCha20 can generate encryption streams of any length needed for your data.
Constant-time implementation means ChaCha20 must take exactly the same amount of time to run, regardless of what data it processes. This prevents timing side-channel attacks, where hackers measure how long operations take to guess secret information.
Poly1305: Your Message as Math
If encryption took longer for certain keys or data patterns, attackers could use those timing differences to break the encryption. Modern implementations achieve this by using branch-free arithmetic (avoiding if-then statements that might take different amounts of time), fixed-iteration loops (always running the same number of times), and careful memory access patterns. This ensures consistent execution timing across all possible inputs and processor cache states.
Poly1305 Universal Hash Function and Authentication Tag Generation
Poly1305 is a universal hash function that works over a special mathematical field called Z/(2^130-5). It treats messages like polynomials, where each piece of your message becomes a coefficient in a mathematical equation. These polynomials get evaluated at secret points that come from your encryption keys. Think of it like plugging secret numbers into a complex mathematical formula based on your message content.
Poly1305 authenticator paper provides the mathematical foundation showing how the libsodium implementation creates one-time authentication keys from the ChaCha20 keystream. This process ensures that each message gets its own unique authentication parameters. This prevents key reuse vulnerabilities and protects against forge-and-replay attacks, where attackers try to copy and reuse old authentication tags.
How ChaCha20 Creates Keys
Authentication tag computation works by processing your message in 16-byte chunks. Each chunk gets treated as a little-endian integer (a way of organizing the bytes) with an extra '1' bit added to the end. The system then evaluates the resulting polynomial using modulo 2^130-5 math and the secret evaluation point. Field arithmetic requires careful implementation of modular reduction algorithms. These algorithms must maintain constant-time execution while efficiently handling the non-power-of-two modulus across different types of computer processors.
How ChaCha20-Poly1305 Protects Your Data
Key derivation security depends on using fresh Poly1305 keys for each message. This happens through ChaCha20 keystream generation with unique nonce values (numbers used only once). The first 32 bytes of ChaCha20 output, generated with counter=0, provide the one-time Poly1305 key. The subsequent keystream bytes, starting with counter>=1, encrypt your actual message content. This design ensures cryptographic independence between authentication and encryption operations, meaning one cannot compromise the other.
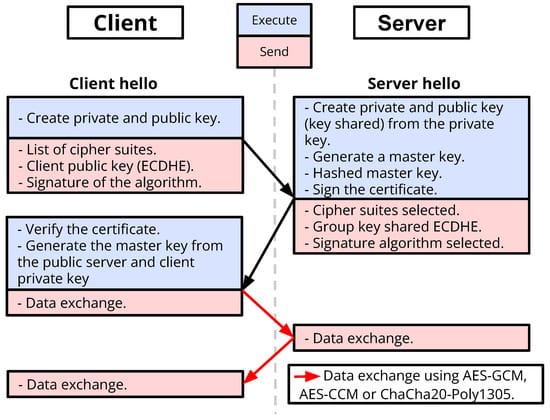
AEAD Mode Construction and Protocol Integration
Nonce + Counter = Unique Every Time
ChaCha20-Poly1305 AEAD mode integrates stream cipher encryption with polynomial authentication through careful ordering of operations and shared key material derivation. Encryption works by generating a ChaCha20 keystream using your provided key and nonce. The system extracts the first 32 bytes for Poly1305 authentication, then XORs the remaining keystream with your plaintext to produce ciphertext. At the same time, it computes authentication tags over both associated data and the ciphertext to ensure everything is protected.
ChaCha20-Poly1305 in Action
Associated data authentication lets protocol designers include unencrypted but authenticated metadata. This might include packet headers, version numbers, or routing information that must be protected against tampering but can remain visible to network intermediaries. Think of it like a shipping label that everyone can read, but no one can modify without detection. The AEAD construction authenticates this associated data along with the ciphertext and their respective lengths, providing comprehensive integrity protection across the entire authenticated scope.
Why Constant-Time Matters
❌ Bad Implementation
Different times = Hackers can guess your key
✅ ChaCha20 Way
Same time always = Your key stays safe
Nonce requirements mandate 96-bit random or counter-based nonce values that must never repeat for the same key. The RFC 8439 specification provides explicit construction guidelines for different use cases. Counter-based nonces work well for session-oriented protocols (like secure connections that last a while), while random nonces suit packet-oriented communications (like individual data packets). Both approaches require adequate entropy sources and collision avoidance mechanisms to ensure nonce uniqueness across all encrypted messages.
What Hackers Try to Exploit
Real-world protocol integration appears in TLS 1.3, WireGuard VPN, Signal messaging, and SSH implementations where ChaCha20-Poly1305 provides authenticated encryption for performance-critical applications. These are the secure protocols that protect your web browsing, VPN connections, private messaging, and remote server access. The OpenSSL ChaCha20-Poly1305 implementation contains production-quality code that demonstrates integration patterns, error handling, and security parameter management required for robust deployment in security-sensitive environments.
Timing Attack Resistance and Side-Channel Protection
timing attack research documents how timing variations in cryptographic implementations can leak secret key information. Attackers can carefully measure execution times, cache access patterns, and power consumption characteristics to guess encryption keys. ChaCha20-Poly1305 design naturally resists many timing attacks through its regular computational structure. However, implementation quality determines the actual side-channel resistance in production deployments.
Memory Access Patterns
Constant-time implementation techniques ensure that execution paths, memory access patterns, and computational operations remain independent of secret key values and intermediate computation results. This means the code takes the same amount of time and follows the same steps regardless of what secrets it processes. constant-time programming provides comprehensive guidance on branch-free programming (avoiding if-then statements), table lookup elimination, and conditional operation implementation. These techniques maintain security against sophisticated timing analysis while preserving computational efficiency.
Mobile Device Performance Comparison
Encryption Speed (ARM processors)
Battery Life Impact
Memory access pattern protection prevents cache-timing attacks where adversaries infer secret information through cache miss patterns, memory allocation timing, or virtual memory behavior. These attacks work by measuring how long it takes to access different parts of memory, which can reveal what data the encryption algorithm was processing. ChaCha20-Poly1305 implementations avoid data-dependent memory accesses, use streaming operations for large data processing, and implement explicit memory clearing for sensitive intermediate values.
Hardware acceleration trade-offs balance performance improvements against potential side-channel vulnerabilities introduced by specialized cryptographic instructions or co-processors. While software implementations provide predictable security characteristics, hardware-accelerated versions require careful analysis. Developers must examine instruction-level timing, power consumption, and electromagnetic emission characteristics that might leak cryptographic secrets through specialized computer chips.
Performance Analysis and Deployment Optimization
Performance benchmarking demonstrates ChaCha20-Poly1305 advantages on processors lacking AES hardware acceleration. Software implementations achieve 2-4x throughput improvements over AES-GCM on ARM Cortex-A series processors commonly found in mobile devices and embedded systems.
This means your smartphone or tablet can encrypt data much faster using ChaCha20-Poly1305 than traditional AES encryption. cryptographic benchmarks provides comprehensive benchmark data across multiple processor architectures and implementation variants.
Choosing the Right Crypto Library
Power consumption analysis reveals significant energy efficiency gains for battery-powered devices. ChaCha20-Poly1305 software implementation consumes 30-50% less energy than AES-GCM software encryption at equivalent security levels. This advantage comes from ChaCha20's simple arithmetic operations that map efficiently to processor pipelines without requiring complex key scheduling or lookup table operations. For mobile devices, this means longer battery life when using encrypted communications.
The Future of Encryption
Library implementation quality varies significantly across different cryptographic libraries. The libsodium implementation provides reference-quality constant-time implementation and comprehensive API design.
Production deployments should prioritize libraries with formal security audits, comprehensive test suites, and demonstrated resistance to implementation-level vulnerabilities. These vulnerabilities include buffer overflows, integer overflows, and secret information leakage.
Future development focuses on hardware acceleration through custom instruction sets, optimized assembly implementations for specific processor families, and integration with emerging cryptographic protocols requiring authenticated encryption. Researchers are also working on post-quantum alternatives that could eventually replace current methods.
AEAD security analysis analyzes ongoing research into post-quantum authenticated encryption that may eventually supersede current AEAD constructions while maintaining performance and security characteristics suitable for widespread deployment.




