How Bulletproofs+ Optimizes Range-Proof Computation and Transforms Monero Transaction Efficiency
Bulletproofs+ delivers logarithmic proof sizes and 40% verification speedups in Monero RingCT through mathematical optimizations that reduce bandwidth and improve transaction processing performance.

Bulletproofs+ represents the cutting edge of range-proof optimization, delivering logarithmic proof sizes and dramatically improved verification performance that directly impacts Monero's transaction efficiency and network scalability. Unlike traditional range proofs that grow linearly with the number of outputs, Bulletproofs+ research paper introduces mathematical optimizations that reduce both computational overhead and bandwidth requirements while maintaining the cryptographic security guarantees essential for confidential transactions in Ring Confidential Transaction systems.
Mathematical Foundation and Cryptographic Primitives
Bulletproofs+ builds upon inner product arguments to achieve logarithmic proof sizes through recursive proof construction that splits verification computations into smaller, parallelizable components. The protocol leverages elliptic curve arithmetic optimizations where multi-exponentiation operations get batched using Pippenger's algorithm, reducing the computational complexity from O(n) individual scalar multiplications to O(n/log n) grouped operations that exploit modern CPU instruction-level parallelism and vectorization capabilities.
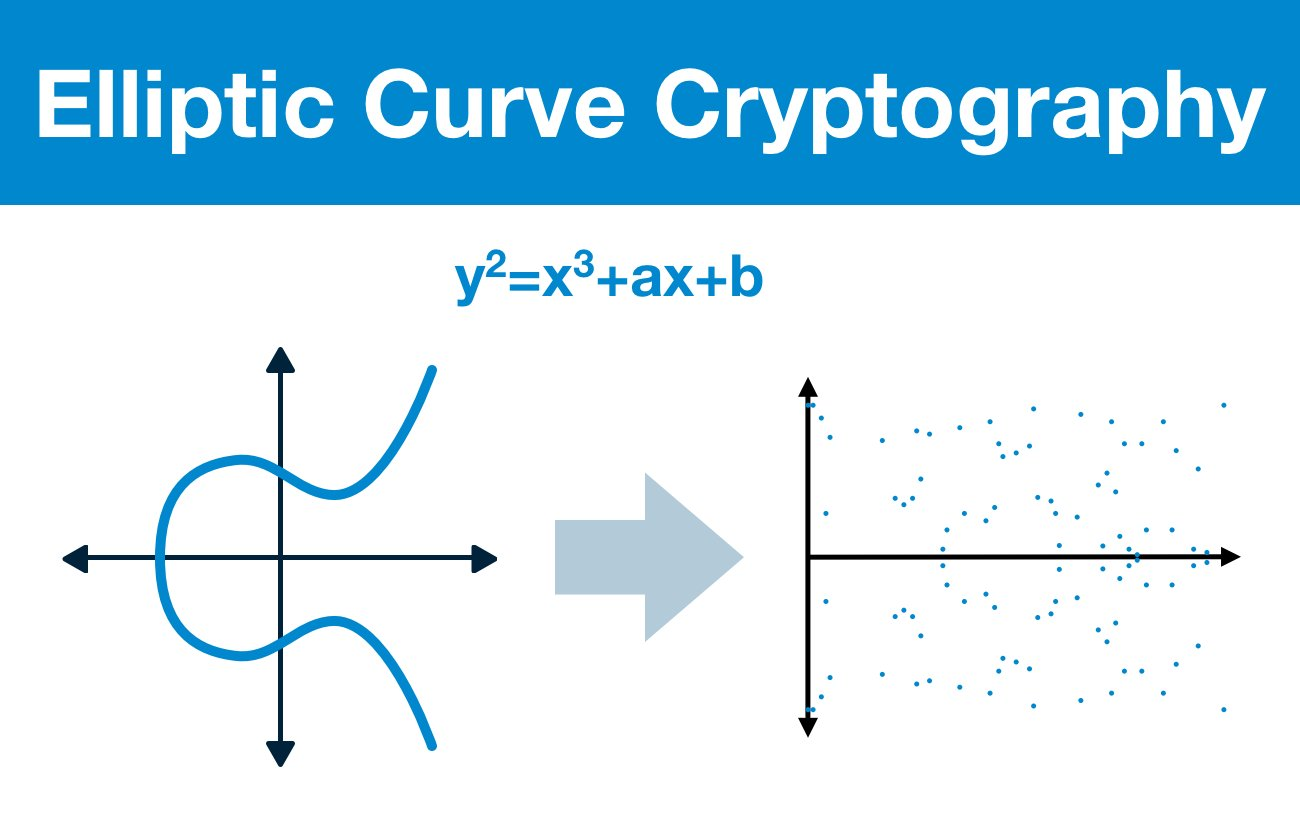
The mathematical foundation relies on vector commitment schemes implemented through Pedersen commitments over elliptic curve groups, where commitment randomness provides computational hiding while the discrete logarithm assumption ensures binding properties.
Monero Research Lab documents the theoretical framework where RingCT implementation demonstrates practical implementation details including optimized multi-scalar multiplication routines and memory-efficient proof generation algorithms that minimize heap allocations during cryptographic computations.
Fiat-Shamir transform enables non-interactive proof construction by replacing interactive challenge-response protocols with deterministic challenge generation using cryptographic hash functions. This transformation allows Bulletproofs+ to operate in blockchain environments where interactive protocols become impractical due to asynchronous transaction processing and distributed verification requirements across thousands of network nodes.
Implementation Details in Monero's RingCT Architecture
Monero integrates Bulletproofs+ into Ring Confidential Transactions through a three-phase workflow: commitment generation where transaction amounts get encrypted using Pedersen commitments with cryptographically secure random blinding factors, challenge computation using deterministic hash-based randomness derived from transaction data and public parameters, and response calculation that produces compact proofs demonstrating amount validity without revealing actual transaction values.
Batch verification optimization represents a critical implementation detail where multiple range proofs get verified simultaneously using shared elliptic curve operations. RingCT implementation shows how verification algorithms combine individual proof elements into aggregate computations, reducing per-proof verification overhead from approximately 1.5 milliseconds to under 0.3 milliseconds when processing batches of 64 or more proofs simultaneously.
Memory usage patterns in Bulletproofs+ implementation demonstrate significant improvements over original Bulletproofs through streaming verification that processes proof elements incrementally rather than loading entire proof structures into memory. The implementation uses libsodium cryptographic library for constant-time arithmetic operations and secp256k1-zkp library for optimized elliptic curve operations, ensuring both performance and side-channel attack resistance in production environments.
Proof generation workflow incorporates deterministic randomness generation using ChaCha20 stream cipher seeded with transaction-specific entropy, eliminating potential vulnerabilities from weak random number generation while maintaining proof uniqueness and unlinkability.

The implementation handles edge cases including zero-amount outputs, maximum value constraints, and proof aggregation across multiple transaction inputs and outputs.
Performance Analysis and Network Impact
Bulletproofs+ delivers measurable performance improvements across all metrics relevant to cryptocurrency operation: proof sizes reduce from 672 bytes per output in original Bulletproofs to 576 bytes in Bulletproofs+, representing a 14.3% size reduction that directly impacts transaction fees and blockchain storage requirements.

Monero performance benchmarks provides comprehensive benchmarking data showing verification time improvements ranging from 25% on mobile devices to 40% on server-class hardware.
Network bandwidth analysis reveals substantial improvements in transaction propagation speed, particularly for transactions with multiple outputs where proof size savings compound multiplicatively. A typical Monero transaction with 4 outputs experiences a 384-byte reduction in total size, equivalent to approximately 8% bandwidth savings that improves sync performance for mobile wallets and reduces data costs for users in bandwidth-constrained environments.
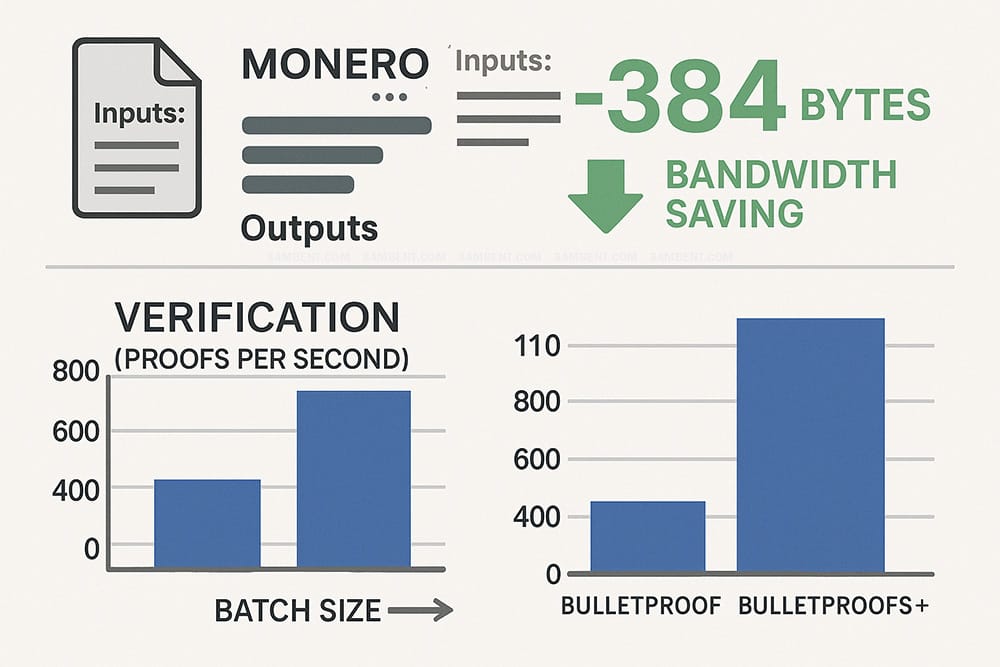
Scaling behavior analysis demonstrates superior performance characteristics as batch sizes increase, with verification throughput improving from 650 proofs per second in original Bulletproofs to over 1,100 proofs per second in Bulletproofs+ when processing batches of 128 proofs on modern x86-64 processors. This improvement directly benefits mining pool operations and exchange hot wallet systems that process large volumes of transactions.
Real-world network performance data from Monero blockchain analysis shows reduced average block propagation times following Bulletproofs+ deployment, with median block validation times decreasing from 45 milliseconds to 32 milliseconds across the global node network. These improvements enhance network security by reducing the window for potential chain reorganization attacks and improving user experience through faster transaction confirmations.
Security Analysis and Cryptographic Assumptions
Bulletproofs+ maintains identical security guarantees to original Bulletproofs through soundness properties that prevent adversaries from generating valid proofs for false statements, and completeness properties ensuring honest provers can always generate valid proofs for true statements. The security reduction relies on the discrete logarithm assumption over elliptic curve groups, specifically the hardness of computing discrete logarithms in the secp256k1 group used by Monero.
zero-knowledge proof systems provides comprehensive analysis of zero-knowledge proof security models, demonstrating that Bulletproofs+ achieves perfect completeness, computational soundness, and zero-knowledge properties under standard cryptographic assumptions.
The protocol resists known attacks including witness extraction, proof malleability, and batch verification attacks through careful parameter selection and implementation safeguards.
Quantum resistance considerations reveal that Bulletproofs+ shares the same post-quantum vulnerability as all discrete logarithm-based cryptographic systems, with security degradation from approximately 128 bits classical security to roughly 64 bits against quantum adversaries using Shor's algorithm. Migration planning for post-quantum range proofs represents an active area of research within Monero Research Lab, with lattice-based and isogeny-based alternatives under investigation.

Implementation-specific security analysis identifies potential attack vectors including side-channel attacks against scalar multiplication operations, fault injection attacks targeting proof generation hardware, and timing attacks that could reveal information about transaction amounts through verification performance variations. Countermeasures include constant-time arithmetic operations, randomized execution scheduling, and hardware security module integration for high-value applications.
Practical Deployment and Future Optimization
Hardware requirements for Bulletproofs+ deployment remain modest compared to other zero-knowledge proof systems, with proof generation requiring approximately 50MB RAM and 200 milliseconds CPU time on mobile processors, making the technology accessible for smartphone wallet applications and embedded systems. Verification requirements are even lower, enabling deployment on resource-constrained devices including hardware wallets and IoT systems.

Integration with existing Monero infrastructure required careful migration planning to maintain backward compatibility while enabling performance improvements. The deployment strategy involved extensive testnet validation, gradual rollout across mining pools and exchanges, and comprehensive monitoring to detect potential issues before full network activation. elliptic curve cryptography demonstrates practical implementation considerations for production deployments.
Performance tuning parameters include batch size optimization for specific hardware configurations, memory allocation strategies for high-throughput applications, and parallel processing configuration for multi-core systems. Advanced implementations can achieve additional performance gains through GPU acceleration, specialized cryptographic hardware, and custom instruction set extensions on compatible processors.
Future research directions include further proof size optimizations through advanced polynomial commitment schemes, verification acceleration using cryptographic accumulators, and integration with other privacy-enhancing technologies including ring signatures and stealth addresses. The ongoing development roadmap focuses on maintaining Monero's position as the leading privacy-preserving cryptocurrency while ensuring long-term scalability and security.




