CryptPad: Zero-Knowledge Architecture
While Google Docs reads everything you type, CryptPad's XSalsa20-Poly1305 encryption and Nakamoto-style consensus protocol ensure the server never decrypts your documents.

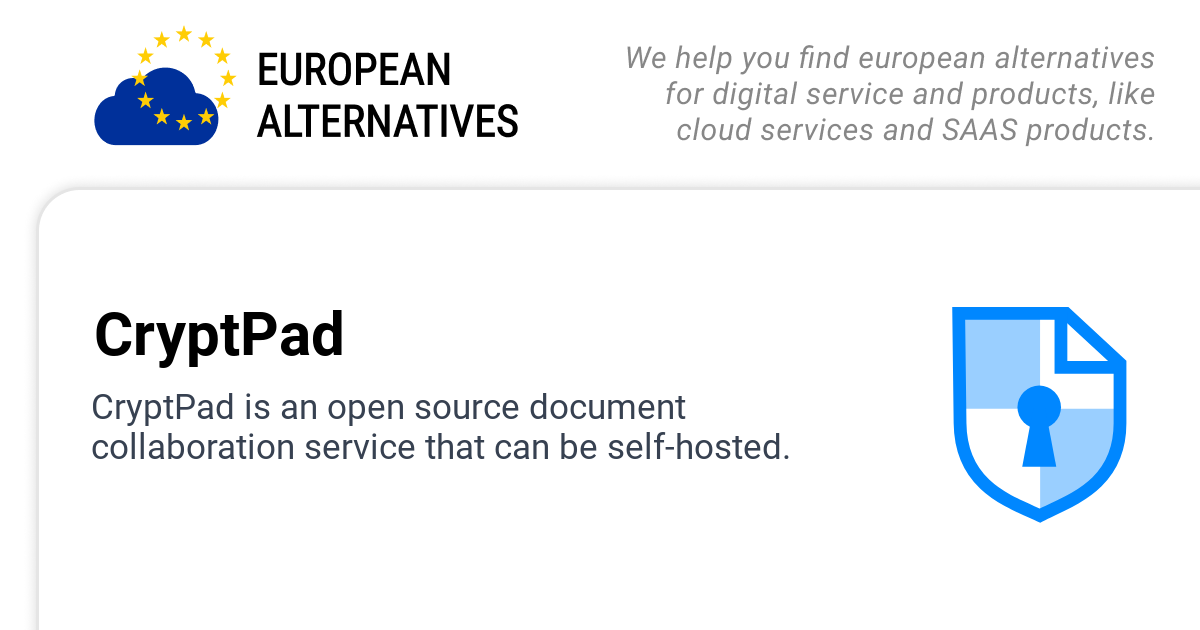
Google Docs encrypts your documents in transit and at rest, which sounds reassuring until you realize Google holds the keys to both locks. The company can read everything you type, everything you share, every comment you make. So can any government with a subpoena, any employee with database access, any attacker who breaches their systems. The encryption protects your data from network eavesdroppers while leaving it completely exposed to the platform itself. CryptPad built something different a collaborative editing platform where the server genuinely cannot access your content, even if administrators wanted to.
The architecture relies on client-side encryption using XSalsa20-Poly1305, an authenticated encryption scheme from the TweetNaCl library. Your browser encrypts documents before transmission, using keys derived from the URL fragment the portion after the # symbol that browsers never send to servers. When you share a CryptPad link, you're sharing the decryption key embedded in that fragment. The server stores encrypted blobs without any ability to decrypt them. If attackers compromise the database, they get useless ciphertext. If governments demand data, CryptPad can hand over encrypted files that provide zero intelligence value.
This zero-knowledge design solves the fundamental trust problem with cloud collaboration. Traditional platforms ask you to trust the company, trust their employees, trust their security, trust their response to legal pressure. CryptPad removes trust from the equation through cryptographic guarantees. The server cannot access user data even if developers explicitly programmed it to try.
But zero-knowledge collaborative editing creates a nasty technical problem. How do multiple people edit the same document simultaneously when the server coordinating their changes cannot read the document? Google Docs solves this easily the server sees every keystroke, merges conflicts, broadcasts changes to all participants. CryptPad needs a synchronization algorithm that works on encrypted data the server cannot interpret.
ChainPad provides the solution through a Nakamoto consensus protocol adapted from Bitcoin's blockchain. Instead of blocks containing transactions, ChainPad uses patches containing document changes. Each patch points to the previous document state, creating a chain. When conflicts occur two people editing the same section simultaneously the system uses "lowest hash wins" as a deterministic tie-breaker. Every client independently applies the same conflict resolution rules to arrive at identical document states. The server merely relays encrypted patches without understanding their content.
The creator Caleb James De Lisle designed ChainPad to avoid centralized conflict resolution. Traditional operational transformation algorithms require a central server to authoritatively resolve editing conflicts. That server must see document content to make intelligent decisions about which changes to keep. ChainPad's Nakamoto-style approach achieves distributed consensus without central authority, enabling clients to agree on document state while the relay server remains ignorant. The algorithm prioritizes eventual convergence over immediate consistency acceptable for collaborative editing where users expect slight delays.
Authentication follows similar zero-knowledge principles. Registration and login happen entirely client-side using scrypt password-based key derivation. Your username and password become arguments to a computationally expensive function designed to take several seconds on modern hardware, making brute-force attacks prohibitively slow. The scrypt output generates login keys an encryption key and unique identifier which retrieve an encrypted block from the server containing your actual account credentials. The server stores this block but cannot decrypt it. Your password never reaches the server, so breaches cannot expose it.
The scrypt function deliberately burns CPU cycles to increase attack costs. In 2021, execution took several seconds on high-end computers. This creates user-facing latency login requires waiting while your browser derives keys. Most platforms optimize for speed, running cheap hash functions that attackers can parallelize across GPU farms. CryptPad sacrifices convenience for security, forcing attackers to spend equivalent computational resources for every password guess.
For document encryption, CryptPad implements multiple cryptographic primitives: X25519-XSalsa20-Poly1305 for public-key encryption, Ed25519 for signatures, SHA-512 for hashes. The symmetric encryption key allowing content decryption derives from the URL hash the fragment after # that remains local to your browser. Modern browsers treat fragments as client-side routing information, never including them in HTTP requests. This architectural choice transforms URLs into encrypted communication channels. Sharing a link shares the decryption key. Intercepting network traffic reveals only the document identifier, not the key needed to access it.
The privacy model has explicit limitations that the CryptPad team documents clearly. The platform provides privacy, not anonymity. Your chosen instance sees your IP address, browser fingerprint, operating system details. Administrators can theoretically correlate IP addresses of users frequently collaborating on the same documents, inferring social graphs without reading content. Network observers ISPs, state-level adversaries, corporate surveillance can track which CryptPad documents you access by watching encrypted identifiers in your traffic. They cannot read document contents, but they know you accessed specific resources at specific times.

The documentation recommends accessing CryptPad through Tor for stronger anonymity guarantees. The browser bundle routes traffic through multiple relays, obscuring your IP from the instance. For high-risk scenarios dissidents coordinating under authoritarian regimes, journalists collaborating on sensitive investigations Tor provides necessary protection against traffic analysis and user correlation. Standard HTTPS hides content but not metadata; Tor hides both.
CryptPad's architecture differs fundamentally from platforms claiming "encryption" while maintaining full content access. Notion encrypts data at rest but holds the keys, reading your notes to train AI models. Microsoft markets Office 365 encryption while scanning documents for policy violations and responding to law enforcement requests. These services provide transport security and storage encryption without zero-knowledge guarantees. CryptPad's threat model assumes server compromise, designing cryptography that remains secure even when attackers control infrastructure.
The platform reached version 2025.6.0 following a three-month release cycle. Recent updates include OnlyOffice 8.3 integration for document, spreadsheet, and presentation applications, bringing improved right-to-left language support and compact interfaces. The Spring 2025 release refactored core code for modularity, dramatically improving load times for users with large drives or shared folders. Previous versions loaded all resources before opening documents; the new architecture loads only required components.
Performance optimization has focused on client-side computation. CryptPad deliberately offloads encryption, decryption, and document processing to user browsers rather than servers. This design enables massive scaling the server merely stores and relays encrypted data without expensive processing. The CryptPad Sodium plugin halved CPU usage on the flagship instance cryptpad.fr by optimizing cryptographic operations. When computation happens on millions of client devices instead of centralized infrastructure, adding users costs storage and bandwidth, not processing power.
The project explores conflict-free replicated data types as an alternative to operational transformation. CRDTs enable offline editing with automatic merging when connectivity returns. The experimental Yjs integration aims to support fully offline collaboration, allowing document changes without network access. Traditional operational transformation requires continuous server connectivity to relay patches; CRDTs work asynchronously, synchronizing changes whenever network becomes available. This matters for unreliable connections, air-gapped environments, and scenarios where internet access poses security risks.

Enterprise deployment supports self-hosting with full source transparency. Organizations can run CryptPad instances on internal infrastructure, maintaining complete control over data location and access policies. The AGPL-3.0 license permits modification and deployment while requiring derivative works remain open source. XWiki SAS provides commercial support, long-term maintenance, and enterprise features for organizations unwilling to manage open-source deployments themselves.
GDPR compliance comes naturally from zero-knowledge architecture. EU data protection regulations demand strict limitations on data collection, processing, and retention. CryptPad avoids these requirements by design the server cannot process content it cannot decrypt. Instances hosted in European data centers meet geographic restrictions without policy changes. The platform collects no analytics, uses no tracking cookies, integrates no third-party services. Compliance becomes automatic when the architecture prevents data access.
Authentication integration supports OpenID Connect through an official SSO plugin. Organizations can connect CryptPad to identity providers like KeyCloak or Univention UCS, enabling centralized user management while preserving zero-knowledge properties. The server authenticates users through external systems without accessing document encryption keys. Enterprise requests for LDAP integration date back to 2017, but the team prioritized modern federation protocols over legacy directory services. OpenID Connect provides equivalent functionality through standardized APIs.
The trust model requires careful consideration of what "zero-knowledge" actually guarantees. CryptPad cannot read your documents, but users must trust that instances run unmodified code from the GitHub repository. Malicious administrators could deploy modified versions that exfiltrate keys or documents. Browser extensions can access page content, including decrypted documents and URL fragments containing encryption keys. Local device compromise malware, physical access, keyloggers defeats cryptographic protections by capturing data before encryption or after decryption.
The platform acknowledges these limitations transparently. Documentation clearly states trust assumptions: users must trust their chosen instance runs legitimate code, that administrators don't block network messages, that collaborators protect shared links appropriately. These requirements apply to any client-side encryption system. The alternative server-side encryption where platforms hold keys eliminates user control entirely. CryptPad shifts trust from platform operators to individual users and their chosen instance administrators.
Commercial platforms lock users into proprietary ecosystems with incompatible formats, limited export options, and discontinued services erasing years of work. CryptPad uses open formats, supports standard export options, and provides full source code allowing community forks if development stops. The architecture prevents vendor lock-in at the protocol level encryption happens client-side using standard algorithms that any compatible implementation can decrypt. Your documents remain accessible regardless of CryptPad's commercial future.
The privacy-preserving collaborative editing space has few legitimate competitors. Etherpad offers open-source collaboration without encryption. OnlyOffice provides office suite features with optional encryption, but uses server-side keys. Nextcloud integrates end-to-end encryption for file storage but not real-time collaborative editing. Standard Notes offers encrypted notes without multi-user editing. CryptPad occupies a specific niche: zero-knowledge architecture with Google Docs-equivalent collaboration features.
Development funding comes from grants, donations, and enterprise subscriptions. The model avoids surveillance capitalism no data harvesting for advertising, no AI training on user content, no selling analytics to third parties. Open Collective donations and NLnet grants support core development. Enterprise customers pay for hosted instances, support contracts, and custom features. This financial structure aligns incentives with user privacy rather than data extraction.
The platform won't replace Google Docs for most users. Mainstream adoption requires convenience, not cryptographic guarantees. People accept surveillance as the cost of free services, rarely questioning what happens to their data. CryptPad targets different users: activists coordinating under hostile governments, journalists protecting sources, businesses handling sensitive IP, anyone who treats document privacy as non-negotiable. The architecture proves collaborative editing and strong encryption can coexist, even if markets reward surveillance over privacy.
Real-time collaboration with zero server knowledge seemed theoretically interesting but practically impossible until CryptPad demonstrated working implementation. ChainPad's Nakamoto consensus, URL fragment key distribution, and client-side operational transformation create a system where servers relay encrypted patches without understanding contents. The cryptographic foundation XSalsa20-Poly1305 encryption, scrypt key derivation, authenticated encryption provides security guarantees that survive server compromise. Privacy requires more than marketing promises; it demands architecture that makes data access cryptographically impossible.
The uncomfortable truth about cloud collaboration is that convenience platforms deliberately architect systems for maximum data access. They need to read your documents to serve ads, train AI, comply with government requests, and monetize user behavior. CryptPad's existence proves that technical limitations don't require this architecture business models do. Zero-knowledge collaborative editing works. Markets simply don't reward it over surveillance-based alternatives. For users who prioritize privacy over convenience, who demand cryptographic protection over corporate promises, CryptPad delivers functional tools that actually prevent rather than merely discourage unauthorized access.




