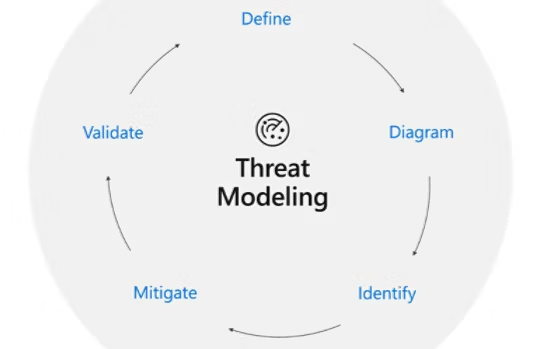
Building Proper Threat Models: What Most People Get Wrong About OPSEC
Effective threat models assess specific adversary capabilities and attack surfaces rather than implementing random security measures.

Most operational security failures occur because people implement random security measures without understanding their specific threats, leading to security theater that provides false confidence while leaving critical vulnerabilities unaddressed.
Adversary Capabilities vs Security Measures
Effective threat modeling starts with honestly assessing who wants to harm you and what capabilities they possess, rather than implementing every security tool available without understanding the threats they address. A journalist investigating local corruption faces different adversaries than someone evading international law enforcement, requiring completely different security approaches despite popular OPSEC guides treating all threats as equivalent.
Local adversaries might have physical access opportunities and legal authority within their jurisdiction but lack the advanced technical capabilities and international reach of nation-state actors or federal law enforcement agencies. Understanding this distinction prevents wasting resources on advanced cryptographic tools when the real threat comes from physical surveillance, social engineering, or legal pressure that technical measures cannot address.
Many people implement elaborate digital security measures while maintaining social media accounts under their real names, or use advanced encryption while meeting sources in locations under physical surveillance, creating security gaps that adversaries will exploit through the path of least resistance.
The key insight is that adversaries will attack the weakest point in your security model, not necessarily the most technically sophisticated, so comprehensive threat assessment must identify all possible attack vectors including physical security, social engineering, legal pressure, and operational security failures that no technical tool can prevent. Building an accurate threat model requires understanding not just what adversaries want to discover about you, but what resources they're willing to invest, what legal authorities they possess, what technical capabilities they can deploy, and what time constraints they operate under, since these factors determine which attacks are realistic versus theoretical.
Attack Surface Analysis and Risk Prioritization
Attack surface analysis involves cataloging every way adversaries can reach you or your operations, then prioritizing defenses based on likelihood and impact rather than technical sophistication or perceived coolness of security measures. Your attack surface includes digital footprints like social media accounts, email addresses, and online services, but also physical elements like home addresses, workplace locations, travel patterns, and social connections that can be exploited through surveillance or social engineering. Most people focus exclusively on digital security while ignoring physical security, financial privacy, and social engineering vectors that are often easier for adversaries to exploit than advanced technical attacks against encrypted communications or anonymous networks.
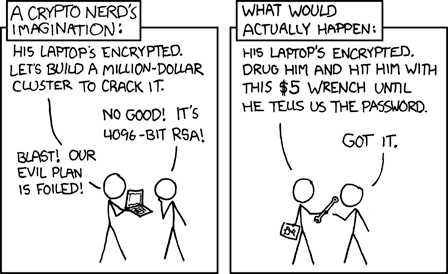
Risk prioritization means understanding that a $5 wrench attack or legal subpoena can be more effective than million-dollar cryptographic research, so security measures must address the most likely and impactful threats first rather than the most technically interesting ones.
The attack surface analysis should include trusted insiders who might be compromised or coerced, service providers who might cooperate with adversaries, and infrastructure dependencies that create single points of failure in your security model.
For example, using the most secure encrypted messaging application provides no protection if your device is compromised through malware, your communications are being intercepted through a compromised contact, or you're being monitored through physical surveillance that makes digital communications irrelevant.
Effective attack surface reduction involves minimizing exposure points, compartmentalizing activities to limit the impact of any single compromise, and implementing layered defenses that force adversaries to overcome multiple independent security measures rather than relying on any single technology or technique for protection.
Operational Constraints & Security Trade-offs
Real-world threat models must account for operational constraints like:
- time pressure
- technical expertise
- budget limitations
- usability requirements
that determine which security measures are actually sustainable versus theoretical ideals that fail under practical pressure. Security measures that are too complex, time-consuming, or expensive will be abandoned or implemented incorrectly when operational demands increase, creating security failures precisely when protection is most needed.
The best security measure is the one that gets used consistently under real-world conditions, not the most theoretically secure approach that gets abandoned when convenience matters more than security.
Threat models must also account for the security implications of the measures themselves - using Tor from your home internet connection (everyone that I have ever talked to who is 'for using a VPN + Tor' does this) creates different risks than using Tor from public WiFi, and both create different risks than not using anonymity tools at all. Some security measures create new attack vectors while mitigating others, such as encrypted messaging applications that require phone numbers for registration, creating identity linkage that might not exist with less secure but more anonymous communication methods.
The sustainability of security practices over time is crucial since adversaries often succeed through persistence rather than sophisticated technical attacks, meaning security measures must remain effective and usable across months or years of operational activity.
Threat model maintenance requires regular reassessment as circumstances change, adversary capabilities evolve, and new attack vectors emerge, since static security models quickly become obsolete in dynamic threat environments where both defensive tools and attack techniques advance rapidly.
The most critical aspect of practical threat modeling is understanding that perfect security is impossible, so efforts must focus on raising the cost and complexity of attacks to levels that exceed what adversaries are willing to invest given their objectives and resources.




