crypto
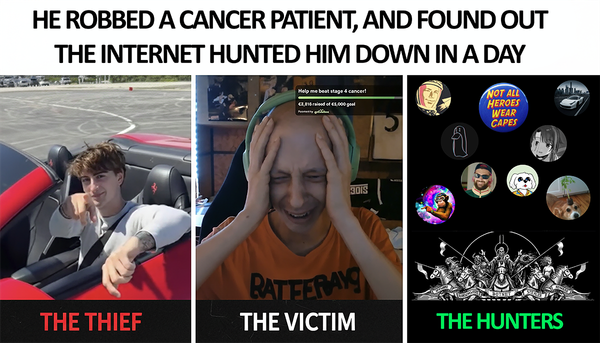
Why You Never Rob Cancer Patients in Front of the Internet, AND Why Steam Sucks
A dying cancer patient lost $32,000 in medical funds when Steam-hosted malware drained his crypto wallet during a live broadcast.

crypto
A dying cancer patient lost $32,000 in medical funds when Steam-hosted malware drained his crypto wallet during a live broadcast.
TorVPN
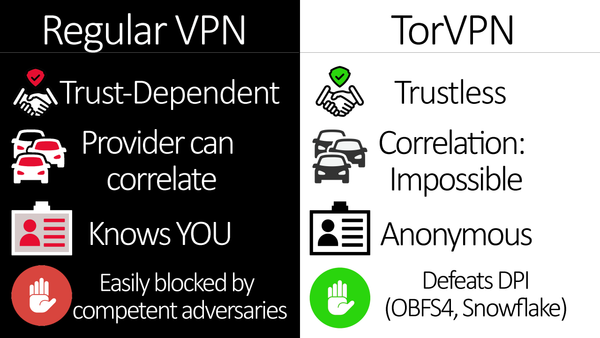
The Tor Project's new Android VPN application fundamentally restructures mobile anonymity through per-app circuit isolation, making commercial VPN trust assumptions obsolete while providing automatic censorship circumvention that adapts faster than authoritarian blocking attempts.
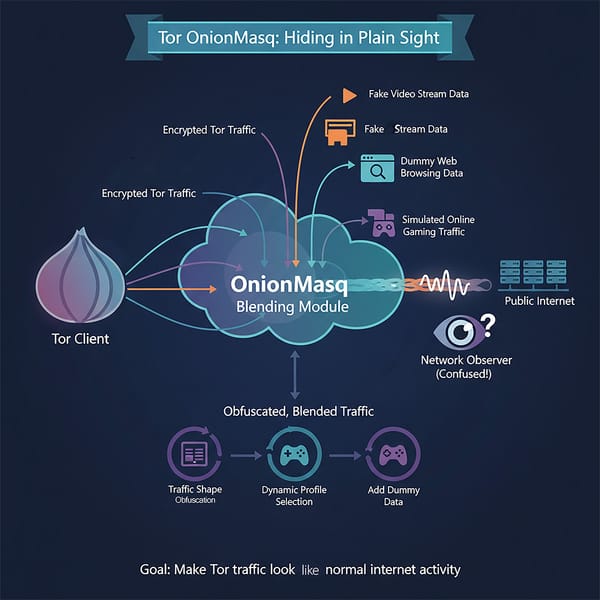
onionmasq
OnionMasq creates VPN-like behavior by trapping applications in kernel-isolated sandboxes where only Tor-routed network interfaces exist, eliminating the bypass vulnerabilities that plague proxy-based solutions.

Monero
While Bitcoin stops at 8 decimal places, Monero goes to 12, a design choice that exposes who's actually thinking about money's future versus who's building digital gold for hodlers.

Surveillance
German and Dutch authorities demonstrated how postal metadata, cryptocurrency analysis, and international surveillance cooperation can penetrate darknet anonymity tools in a multi-million euro drug case.
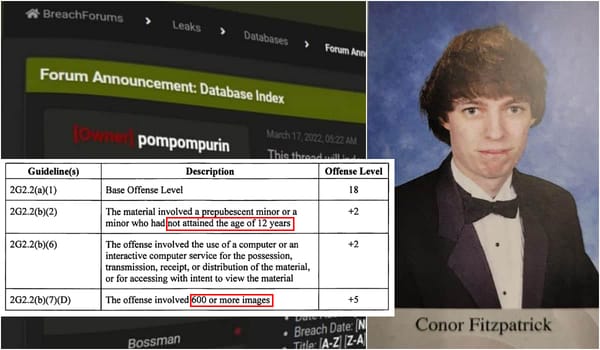
breachforums
Update/correction: On September 16, 2025, the Justice Department announced that Conor Brian Fitzpatrick (aka “Pompompurin”) was resentenced to three years in federal prison.

Signal
Signal just rolled out centralized backups, and the guy who announced it has quite the resume. Jim O'Leary, Signal's VP of Engineering since 2019, spent the previous eight years building surveillance infrastructure at Twitter and Facebook.

Monero
Brave Browser handles 94 million users monthly with zero dependency on Google or Microsoft servers, and Big Tech should be terrified of what this proves.

BGPStream
BGPStream enables automated BGP hijack detection through real-time routing analysis and CLI automation that identifies prefix hijacking and generates security alerts for network operators.

Vaultwarden
Cloud password managers aren't protecting your data, they're collecting it for profit while making you the product in a surveillance economy that profits from your digital enslavement.
ECDH
Most ECDH implementations contain fatal flaws that let attackers recover private keys through mathematical manipulation.

I2P
I2P garlic routing provides enhanced anonymity through multi-layered encryption and timing correlation resistance mechanisms that protect hop metadata and defeat traffic analysis attacks.