AI-Generated npm Wallet Drainer Exposes Supply Chain Catastrophe
The package literally advertised itself as an 'enhanced stealth wallet drainer' in its own source code, and npm still served it up for days.
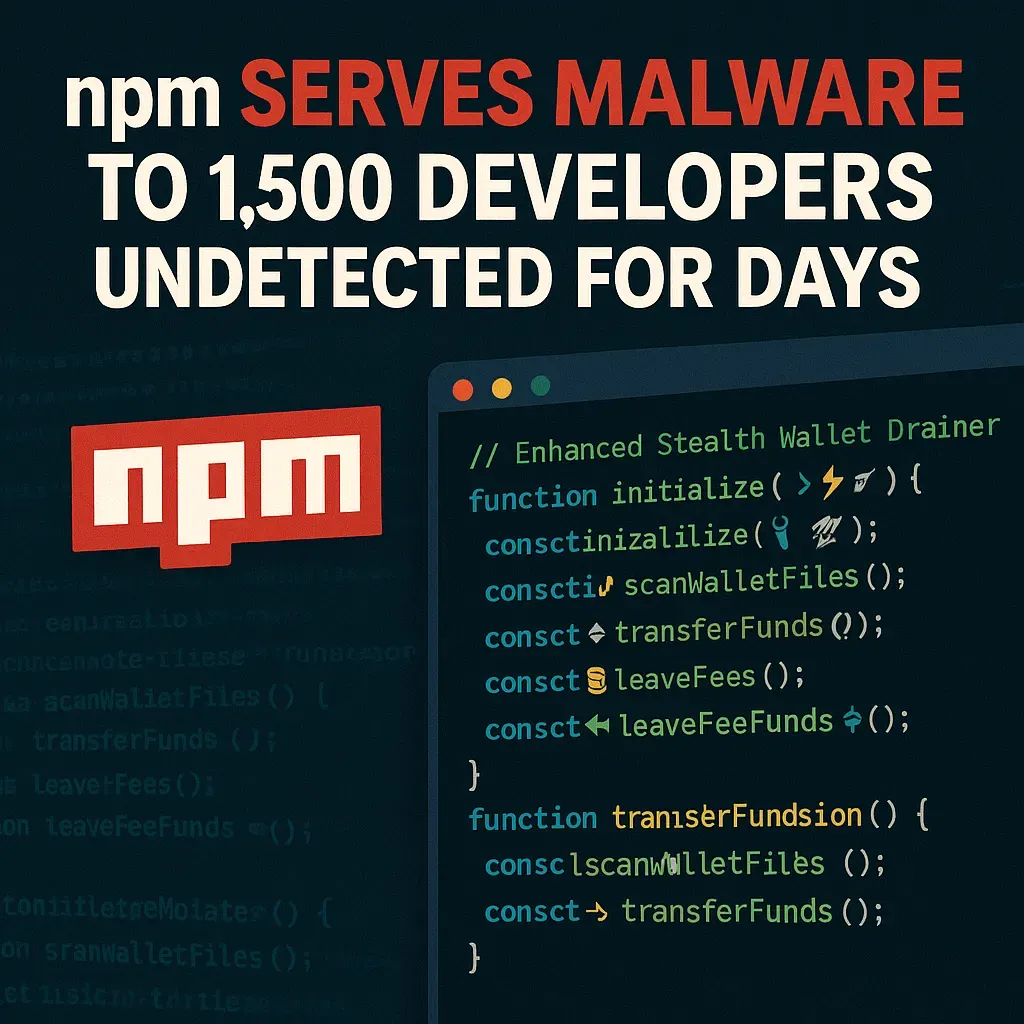
So npm just served malware to 1,500 developers and nobody noticed for days.
The @kodane/patch-manager package claimed it was for "advanced license validation and registry optimization utilities." Total nonsense. What it actually did was drain Solana wallets through postinstall scripts, the same attack vector security researchers have been screaming about for years while the JavaScript ecosystem did exactly nothing to fix it.
Paul McCarty from Safety found this thing after it had already infected 1,566 machines between July 28 and July 30, 2025. The malware author pushed 19 versions in two days, basically iterating in real-time while victims installed poison straight into their dev environments and CI/CD pipelines.
The package literally advertised itself as an "enhanced stealth wallet drainer" in its own source code. Like, they weren't even trying to hide it, and npm still served it up for days.
Claude's Fingerprints All Over the Malware
The malware screams "I was written by Claude." Emojis everywhere in the code, which no actual malware author would ever do. McCarty nailed it: "Claude, however, does this every time I use it. It's obsessed with emojis." The comments are pristine English explaining every function, markdown docs formatted exactly how Claude does it, and the word "Enhanced" plastered on everything like Claude's personal signature.
Technical Breakdown of the Attack
The technical stuff is straightforward evil. Postinstall script runs automatically after you npm install, drops payloads into hidden directories: %APPDATA%\npm\registry-cache\ on Windows with the attrib +H treatment, ~/.local/share/npm/registry-cache/ on Linux, ~/Library/Application Support/npm/registry-cache/ on macOS. Standard obfuscation renamed the files: monitor.js became connection-pool.js, sweeper.js became transaction-cache.js, utils.js became post-install.js. Any decent security scanner should've caught this, but here we are.
Once it's in, the malware phones home to sweeper-monitor-production.up.railway[.]app, with backup C2 servers at sweeper-monitor.railway.app and va.vision-node.com:8899. Railway.app is this Platform-as-a-Service that developers love for its GitHub integration and free tier. Perfect cover for malicious traffic. The malware generates a unique machine ID and reports back to the C2 server, which was completely open when McCarty checked it. Two compromised machines were already listed.
The wallet draining is almost elegant in its cruelty. Scans for Solana wallet files, finds them, initiates transfers to B2XwbrGSXs3LAAcqFqKqGUug5TFA1Bug2NNGH3F3mWNK. The detail that shows either experience or AI help: it leaves just enough funds to cover transaction fees. The author used a Helius RPC endpoint with the API key right there in the code: https://mainnet.helius-rpc.com/?api-key=97188cdf-0b78-4cba-86f9-c4bbbd44c6aa. Amateur hour operational security despite professional-looking code.

Upload timestamps put this at UTC+5, so we're looking at Russia, China, India, or somewhere nearby. Author email was apexoperationsinc@gmail.com, probably throwaway. "Kodane" means "offspring" or "child" in Japanese. Either they're being cute with misdirection or it's a cultural tell.
The Systemic npm Failure
The real problem goes way deeper than one bad package. Every npm install runs arbitrary code from strangers on the internet, and we've all just accepted this insanity. Postinstall scripts execute automatically, meaning you get compromised without even running the package. The --ignore-scripts flag exists but it breaks legitimate packages that compile native extensions or do necessary setup. You're screwed either way.
CI/CD pipelines make this exponentially worse. Dependabot, Renovate, all these automated dependency updaters, they're basically installing malware directly into production without any human looking at it. Those 1,500+ downloads probably represent a fraction of actual infections, since build servers and dev machines were silently running this payload during routine operations.

Anthropic's fingerprints being all over this malware is uncomfortable. They publish these reports about "detecting and countering malicious uses of Claude" and claim they ban accounts for "violative activity," but their AI just helped steal real money from real people. They even admitted AI enables "novice actors to develop sophisticated tools beyond their actual skill level," which is exactly what happened here.
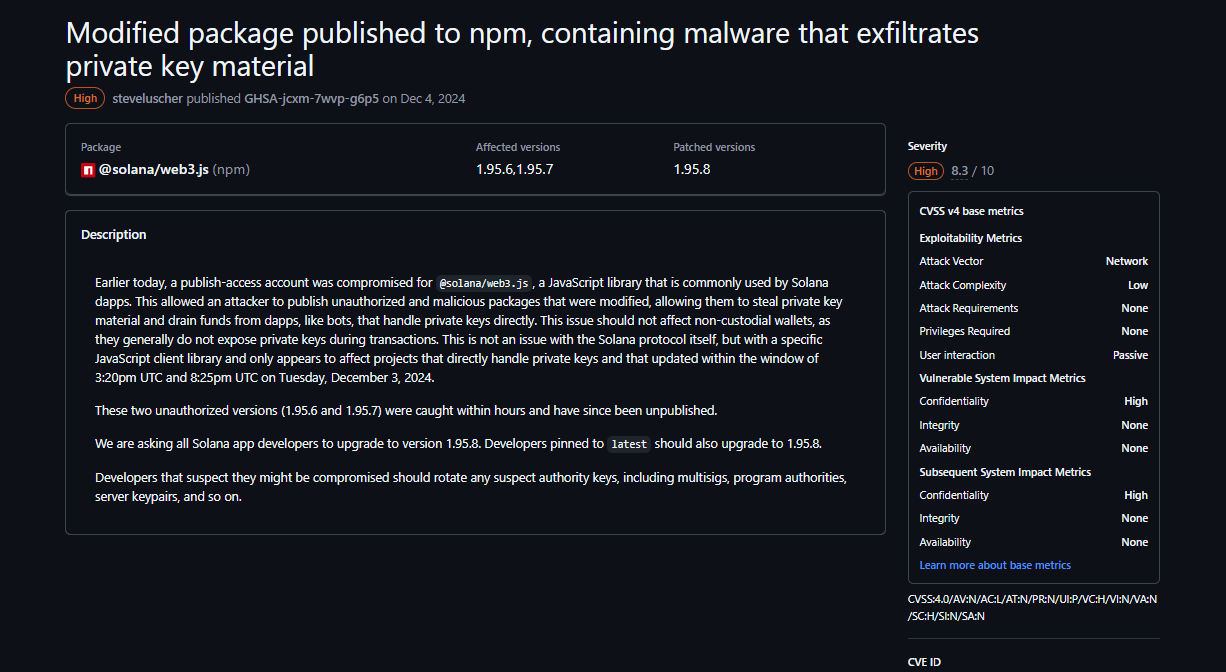
npm's security model is pure trust in a trustless world. Package maintainers use garbage passwords, skip 2FA, fall for phishing emails, and npm publishes whatever they upload to millions of developers. Remember the eslint-scope compromise in July 2025? Infected packages with 30 million weekly downloads. The @solana/web3.js backdoor in December 2024? Could've compromised every Solana dApp using the official SDK. Socket reported 70+ malicious packages stealing crypto in 2024 alone.
Traditional antivirus and endpoint detection are useless against supply chain attacks. The malware comes through trusted channels, signed by legitimate certificates, running in the context of dev tools that need broad system access. By the time behavioral analysis might flag something suspicious, your wallets are already empty.
Privacy-conscious developers face an impossible choice. Participate in the npm ecosystem and accept the risk, or build everything from scratch. The ignore-scripts option breaks too many packages to be practical. Sandboxing helps but isn't foolproof. Malware can wait, hiding until it detects production credentials or crypto wallets. The only real protection is not having wallets on development machines, but that's basically impossible for blockchain developers who need to test transactions.

This attack shows AI's dual nature perfectly. Same tool that helps developers write better code helps criminals write better malware. McCarty said it best: "threat actors are leveraging AI to create more convincing and dangerous malware" and "AI-generated packages may bypass conventional defenses by appearing clean or even helpful." The professional documentation and clean code that would normally indicate a trustworthy package now serve as camouflage for theft.
Railway.app getting abused as C2 infrastructure highlights another failure: legitimate services can't or won't prevent malicious use. Cloud platforms provide APIs, attackers use them, and distinguishing legitimate from malicious traffic becomes someone else's problem. That sweeper-monitor-production subdomain ran for days, openly logging successful wallet thefts, before anyone shut it down.
No Real Solutions Coming
npm's post-mortem will recommend the same useless measures as always: enable 2FA, audit your dependencies, use lockfiles, pin versions. None of which would've prevented this attack. The malware author created a new account, published a new package, and users installed it. System working as designed.
Real solutions need fundamental changes npm will never make: mandatory code signing with hardware tokens, sandboxed installation environments, capability-based security models, or most radically, eliminating automatic script execution entirely. Each would break backward compatibility and developer workflows, so the ecosystem keeps serving malware alongside legitimate code.

For developers still forced to use npm, operational security becomes everything. Dedicated dev machines isolated from production credentials, crypto wallets on separate hardware, network segmentation preventing lateral movement, aggressive egress filtering might limit damage. Running npm install inside disposable VMs adds friction but prevents persistent compromise. Monitoring DNS queries for suspicious domains like railway.app subdomains could give early warning.
The Kodane incident won't be the last AI-generated supply chain attack. As LLMs improve, distinguishing AI-generated from human-written code becomes impossible. Attackers get professional-quality malware for free, complete with documentation and comments that pass casual review. Same AI that accelerates legitimate development accelerates malicious development equally.
JavaScript's ecosystem depends on thousands of micro-packages from anonymous authors. That's the vulnerability. The median npm package has zero tests, documentation, or maintenance commitment. Installing any package means trusting not just its author but every author of every dependency recursively. That trust model worked when the community was small and attacks were rare. At current scale, it's a disaster on repeat.
Until we get fundamental architectural changes addressing the root cause, arbitrary code execution by strangers, these attacks continue. Each incident gets a blog post, a CVE number, and recommendations nobody follows. Developers keep running npm install, attackers keep publishing malware, and cryptocurrency keeps disappearing. The system works exactly as designed, which is the whole problem.

Check your systems for these IOCs, but honestly, by the time you read this, the next attack's probably already running:
- monitor.js:
7a0a3e64ecb4212ce08315400ed7ed79617843e2bc4326439ca8b81d1960ecbc - sweeper.js:
3aa51674e3d46062b6de2cfd6c20f8b70fef2b6a28add462a870f686e387f9de - utils.js:
e8e5ace2a791d519e69c547e1a8491bf6a5d3060c080ff7e8350b86f2a0aab30
And like, at the end of the day, this is something we should all be aware of. And definitely beware of.




